Tags: forensics wireshark
Rating:
## Eternally Pwned: Infiltration
- Tags: Forensics
- Description: I recently had my passwords and other sensitive data leaked, but I have no idea how. Can you figure out how the attacker got in to my PC?
## Solution
- To solve this question you need to download the following file and open it using Wireshark tool, to intercept all of the traffic.
- There we will see a lot of logs, after searching for something that will look suspicious, we find one of the Echo requests.
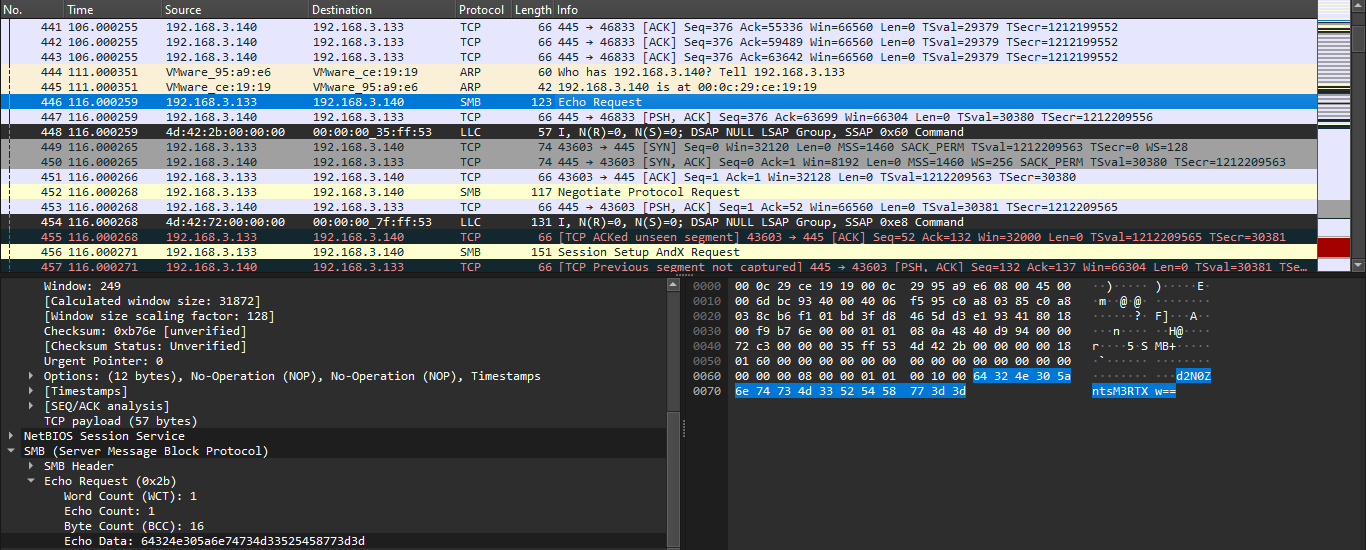
- In there we will see some interesting Base64 stringm when we decode it, we get:
```
wctf{l3tS_
```
- This is the first part of the flag, now let's find another two, using the search bar and look for more of those strings, that will give us the final result with the flag.
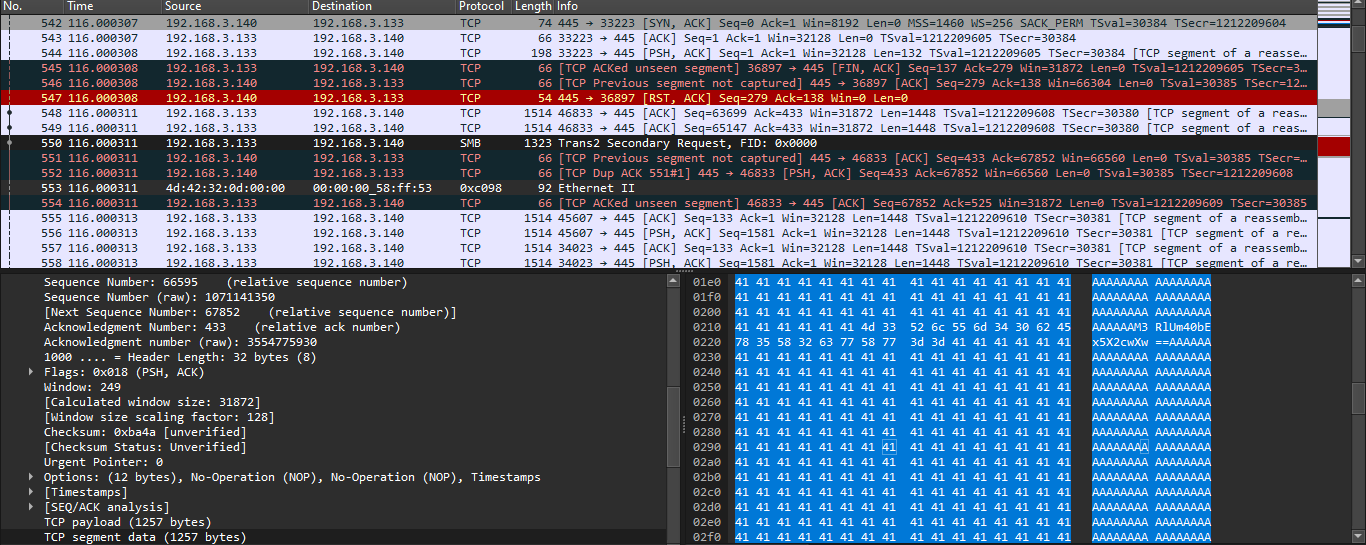
```
3teRn4lLy_g0_
```

```
bLU3_7n9wm4iWnL}
```
- Let's concatenate those parts into one to get the final result.
```
wctf{l3tS_3teRn4lLy_g0_bLU3_7n9wm4iWnL}
```