Tags: hardware canbus
Rating: 5.0
## Recon
after a bit fiddeling around with the webservice at the provided [LINK](https://obd-tuning.ctf.allesctf.net/), we found out
* you can add an arbitrary 7-letter 'dongle code' to the system here: [activate](https://obd-tuning.ctf.allesctf.net/activate)
* you can search for that code here: [dongle](https://obd-tuning.ctf.allesctf.net/dongle)
which also shows a new parameter in link url 'dongleID' (https://obd-tuning.ctf.allesctf.net/dongle?dongleID=28). with a bit testing we had the insigth
* dongleID=7 seems 'connected'
* if a dongleID is not used, like 999, system errors with ``` Oooooops an error occured. Pls contact the admins or if you are an admin, append &isAdmin=1 to the URL to see more information.```
combining those two resulted in: https://obd-tuning.ctf.allesctf.net/dongle?dongleID=7&isAdmin=1, which gives us a special debug version of the dongle number 7 page, where you can
* get a password for the system service ```IP: Checkout our broker. Password for Broker is ed6bf7142581b9e5cd93080b6dcc1426```
* a pcap dump of some canbus
## Loggin In
armed with that info you can login to the system
```
root@kali:~/alles2020/can# ncat --ssl 7b00000099bf9868de13c429.challenges.broker5.allesctf.net 1337
Welcome to the OBD dongle!
Please enter the password to continue!
Should you not have received your password yet, checkout the vendor page at: https://obd-tuning.ctf.allesctf.net
Password: ed6bf7142581b9e5cd93080b6dcc1426
Password correct.
Please reconnect.
root@kali:~/alles2020/can# ncat --ssl 7b00000099bf9868de13c429.challenges.broker5.allesctf.net 1337
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
obd@obd-tuning-ecus:/home/obd$
```
## Dumping
lucky for us, here we have the full toochain installed (canutils, python3, scapy), so first command was
```candump vcan0```
watching a bit the canbus data flowing
```
...
vcan0 350 [3] 02 32 36
vcan0 799 [2] 01 36
vcan0 00000888 [3] 02 36 38
vcan0 002 [2] 01 30
vcan0 00003071 [2] 01 31
vcan0 799 [2] 01 34
vcan0 00000888 [3] 02 36 38
vcan0 642 [8] 10 21 34 38 2E 31 34 38
vcan0 00001337 [3] 30 00 00
vcan0 642 [8] 21 38 32 30 32 38 37 32
vcan0 642 [8] 22 39 34 35 2C 31 31 2E
vcan0 642 [8] 23 37 31 32 35 37 33 33
vcan0 642 [7] 24 30 34 30 31 32 38
vcan0 00000888 [3] 02 36 38
vcan0 799 [2] 01 33
vcan0 799 [2] 01 34
...
```
the well educated car hackers eye, will see after a bit watching, that one of the bigger, sticking out can-ids (642) is some data wrapped in [ISO-TP](https://en.wikipedia.org/wiki/ISO_15765-2) can transport protocol
```
vcan0 642 [8] 10 21 >34 38 2E 31 34 38<
vcan0 642 [8] 21 >38 32 30 32 38 37 32<
vcan0 642 [8] 22 >39 34 35 2C 31 31 2E<
vcan0 642 [8] 23 >37 31 32 35 37 33 33<
vcan0 642 [7] 24 >30 34 30 31 32 38<
```
extracting the ISO-TP payload results in
```34382E313438383230323837323934352C31312E37313235373333303430313238```
which converted to text is
```48.1488202872945,11.7125733040128```
which looks pretty much like GPS coordinates - extracting all those coordinates from the canbus stream and drawing them on a map gave us:
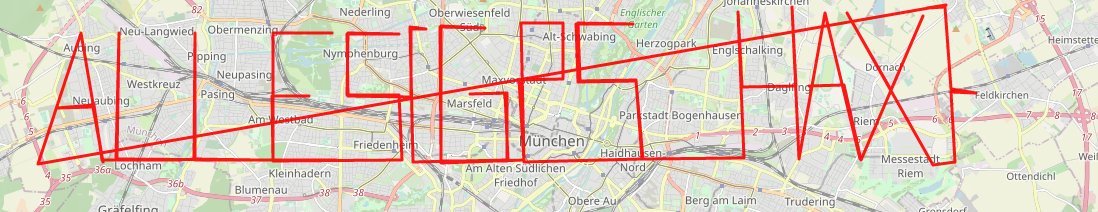
## ALLES{GPS_HAX}
macz