Tags: xor vigenere
Rating:
# Sunshine CTF 2019 All Crypto Challenges Writeups# Welcome Crypto [50]
Here's the challenge
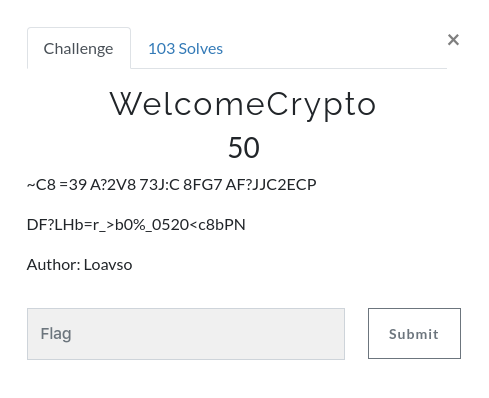
```~C8 =39 A?2V8 73J:C 8FG7 AF?JJC2ECP
DF?LHb=r_>b0%_0520
I don't remember