Tags: ghidra angr
Rating: 5.0
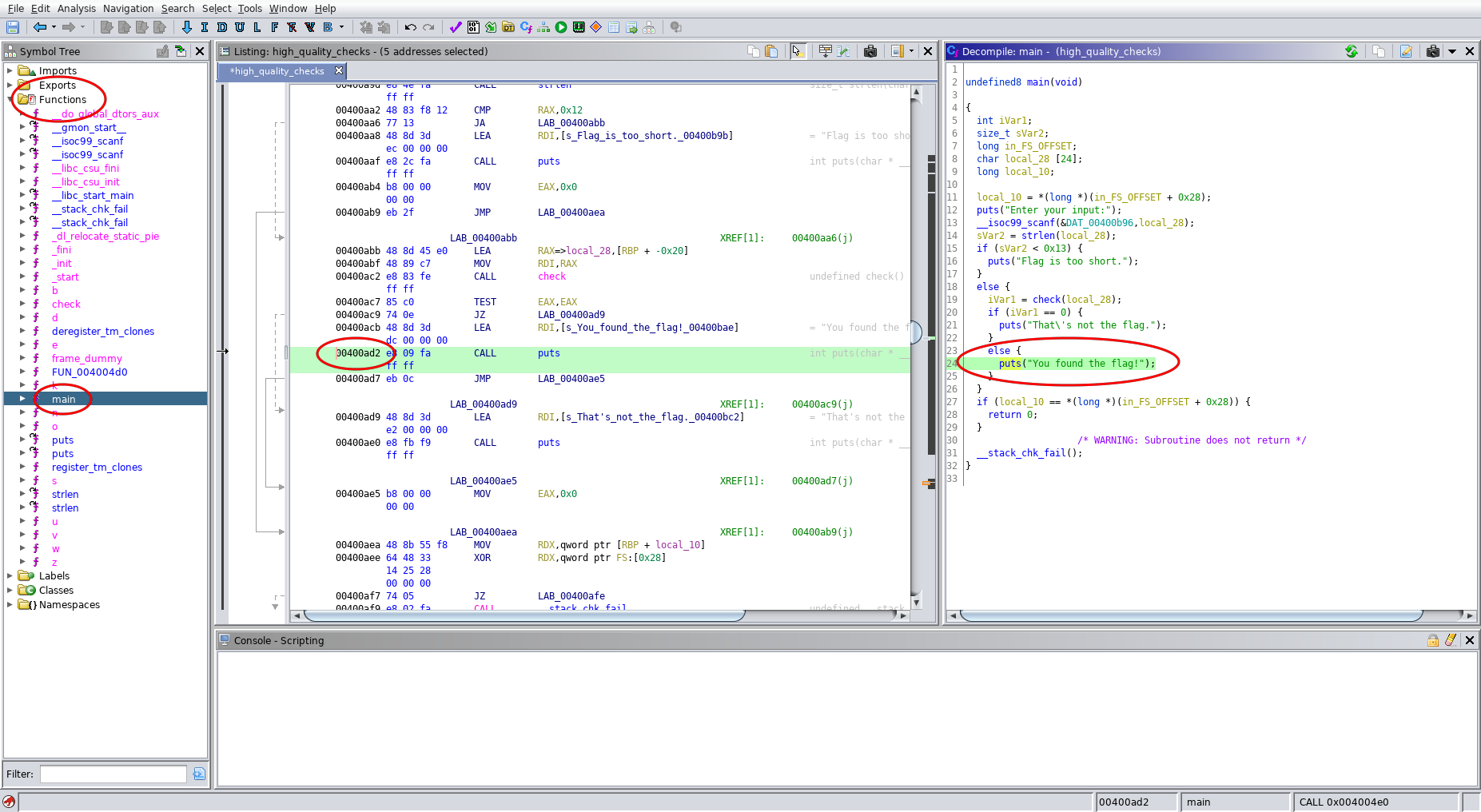
I started manually reversing the binary using ghidra, but it seems like a problem that angr should easily be able to automatically solve.
```python
import angr, claripy
proj = angr.Project('high_quality_checks')
arg1 = claripy.BVS('arg1', 20*8)
initial_state = proj.factory.entry_state(args=["high_quality_checks", arg1])
simgr = proj.factory.simulation_manager(initial_state)
# Address 0x400ad2 is found using ghidra (it is the location that prints "You found the flag")
simgr.explore(find=0x400ad2, avoid=[])
print(simgr.found[0].posix.dumps(0)) # actf{fun_func710n5}
```