Tags: binary-exploitation
Rating:
The application picks a random number and if this number is 1, we get the flag.
```
λ ./executable-ubuntu
Welcome to the lottery!
So now we're going to pick a ginormous number!
If it's 1, you win!
Your number is 1804289383!
Try again next time!
```
This challenge could be solved in two ways.
**1. strings command**
After running `strings` command on the executable, we see that there is a suspicious string which looks like Brainfuck.
```
--[----->+<]>----.+.--.++.-[--->+<]>--.+++[->+++<]>+.+[----->+<]>.>-[----->+<]>.+[--->++<]>.[++>---<]>-.-[->++<]>-.-[--->+<]>-.-.>-[----->+<]>+.---[->++<]>.++++++++++.[-->+<]>---.--[--->++<]>---.++[->+++<]>.[--->+<]>---.+++[->+++<]>.+++++++.-[--->+<]>--.-------.---------------.+[-->+<]>+.+.++.+[->++<]>.--.---.+++++++++++++.--[->+++++<]>.++++++++.+.-------.++.+.>--[-->+++<]>.
```
After running this Brainfuck code on an [online Brainfuck interpreter](https://copy.sh/brainfuck/), we see the flag as the output:
`bcactf{3x3cut4bl3s_r_fun_124jher089245}`
**2. Debugger**
Another way to solve this challenge is with the help of a debugger. I prefer to use radare2, so lets open this executable in debugger mode.
`r2 -d executable-ubuntu`
After running `aa` and `pdf @ main` we can see the same string, however if we still want to make the random number 1 to win, we can put a breakpoint at the `cmp ebx, 1` line and edit the register ebx to 1.
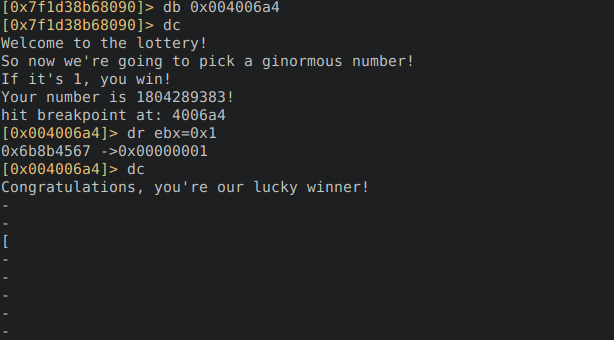
After that, we can remove the newlines in output and get the same Brainfuck code.