Rating:
We have a file with values of pixels and password-protected archive which contains the next 2 files. To get the password, we have to assemble an image, then somehow read the password from the image (I used pytesseract library for it).
Here is a script I used for it (works with python3, but need to change ```print```s):
```
from PIL import Image
import pytesseract, os
def getFile(extension):
for item in os.listdir(os.getcwd()):
if extension in item:
return item
def getDir():
for item in os.listdir(os.getcwd()):
if os.path.isdir(item):
return item
def prepareImg(fileName):
with open(fileName, 'r') as file:
data = file.read()
tmp = data.split('\n')[:-1]
rows = []
for item in tmp:
rows.append(item.split(' ')[:-1])
height = len(tmp)
width = len(rows[0])
pixels = []
for row in rows:
t = []
for pix_str in row:
p = pix_str[1:-1]
t.append(tuple(int(s) for s in p.split(',')))
pixels.append(t)
print 'Height: ', len(pixels), ' width: ', len(pixels[0])
im = Image.new('RGB', (height, width))
for i in range(0, height):
for j in range(0, width):
im.putpixel((i,j), (pixels[i][j][0], pixels[i][j][1], pixels[i][j][2]))
im.save('output.png')
print 'Output image saved'
def extractPasswd():
passwd = str(pytesseract.image_to_string(Image.open("output.png"))).lower()
print 'Extracted password: ', passwd
usr_passwd = raw_input("Change >>> ")
if usr_passwd != "":
passwd = usr_passwd
return passwd
while True:
fileName = getFile(".png")
print 'Handling image: ', fileName
prepareImg(fileName)
print 'Handling output image with pytesseract'
passwd = extractPasswd()
z = getFile(".zip")
print 'Extracting zip archive: ', z
os.system("unzip -P " + passwd + " " + z)
nextDir = getDir()
# os.system("cp script.py " + nextDir)
print 'Going to the next dir: ', nextDir
os.chdir(nextDir)
print 'Directory changed'
```
Sometimes pytesseract failed and recognized short passwords incorrectly (interesting note: pytesseract correctly extracted long words like "unrecognizable", "subdirectional", "enterpreneurship" in almost 100% of cases), after a few failes I added an ability to edit extracted password.
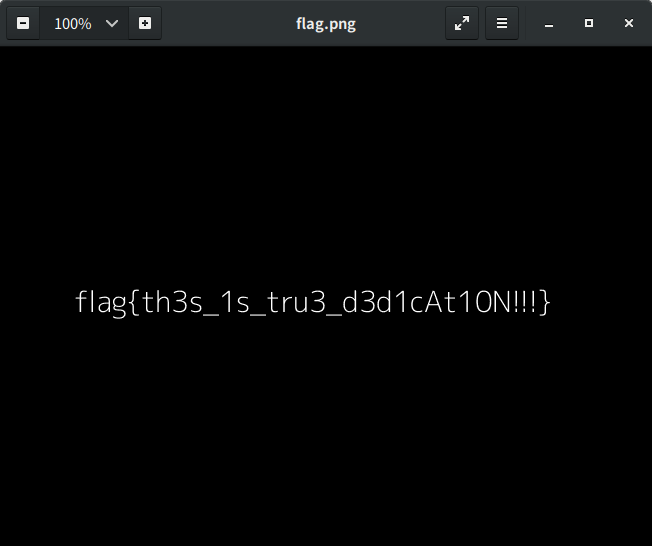
It was very tedious challenge. Finally we got the flag: