Tags: reverse
Rating: 5.0
I spent a long time on this problem, the program enabled PIE, we can disable random_va_space on Linux:
```
$ sudo echo 0 > /proc/sys/kernel/randomize_va_space
```
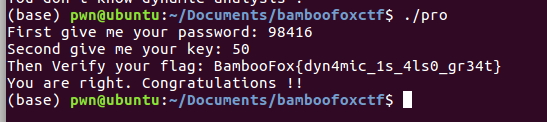
And then use IDA for remote debugging. I know that the program needs to detect two values, one is password, it is easy to get 98416 through IDA static analysis .
The other is the Key, this Key needs to be detected by burst on my first mind. But my coding ability is very weak, and I didn’t write it for one night.
In the end, I know that this Key is used to decode the code of the obfuscated function. It only involves 11 bytes, and it is simply added to the Key to decode. So the size of the key should be only one byte(0x00-0xFF), and then I manually test from 0. After using the wrong key, Segmentation fault error and illegal instruction error will appear. I found that 39 and 43 can avoid the above error, but still I can’t decode the flag.Fortunately, when I tested 50, it happened to be the correct key, and I was able to decode the flag.
**Remark** : Could masters share your brute-code for this challenge? I want to learn how code it. Or it will use `angr` or other?
**Added at 2020.01.02**:
At last, I use `expect` shell to brute the key, there are 7 keys to make this program not occur `Segmentation fault` or `illegal instruction` error. The Script is:
```expect
#!/usr/bin/expect
# For bamboofoxctf-Move or not
set time 30
set i 0
for {set key 0} {$key<=255} {incr key} {
spawn ./pro
expect "*password: " {send "98416\r"}
expect "*key: " {send "$key\r"}
expect "*flag: " {
send "Test_flag\r"
}
}
```
And run it, from the output get the keys, include `[39,43,48,50,114,117,206]`, then use ltrace to test it.
```bash
spwpun@ubuntu:~/Documents/20200102$ ./crack.sh > output.txt
spwpun@ubuntu:~/Documents/20200102$ cat output.txt | grep -B 1 "flag"
Second give me your key: 39
Then Verify your flag: spawn ./pro
--
Second give me your key: 43
Then Verify your flag: spawn ./pro
--
Second give me your key: 48
Then Verify your flag: spawn ./pro
--
Second give me your key: 50
Then Verify your flag: spawn ./pro
--
Second give me your key: 114
Then Verify your flag: spawn ./pro
--
Second give me your key: 117
Then Verify your flag: spawn ./pro
--
Second give me your key: 206
Then Verify your flag: spawn ./pro
```