Rating: 5.0
# 652AHS Challenge
First, we connect to the server :
He says that we have to select an option. Let's select the first option "Enter password" :
So we have to enter a password to login, but we don't have any password !
Then, let's try to reset it :
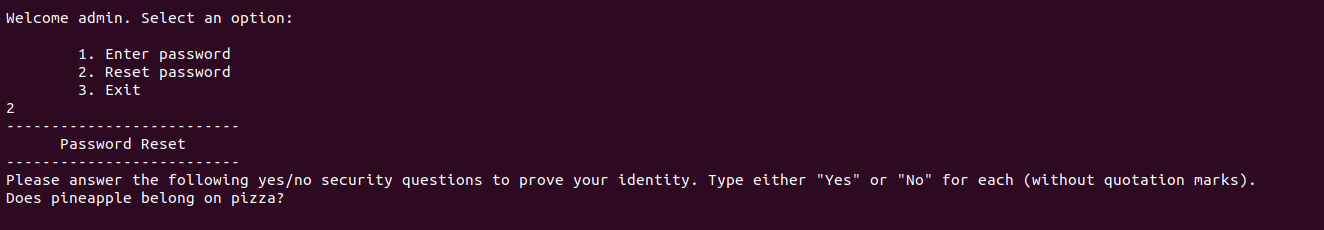
So to prove our identity and reset the password, we have to answer the following 20 yes/no security questions. But are we going to bruteforce 2^20 possibilities ?! Naaah ofc not :D
We try to send "Yes" or "No" to some questions, we notice that sometimes it doesn't take the same time to pass to the next question, it means that he is comparing the answer to something, which leads us to the Timing Attack ! (https://en.wikipedia.org/wiki/Timing_attack)
If the answer is TRUE, he will take more time cause he will enter to a loop and compare all characters. If it's FALSE, he will break.
Based on that, we can determine all the answers and set new password :
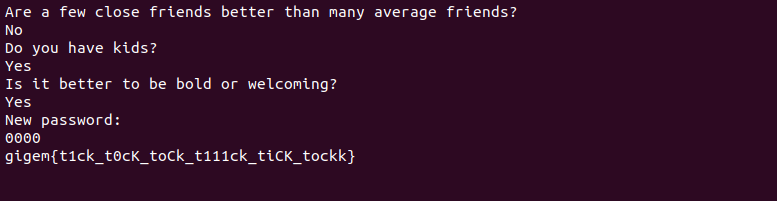
And BOOOOOM !!
gigem{t1ck_t0ck_toCk_t111ck_tiCK_tockk}