Rating: 5.0
By using the commands binwalk and file, we found no results
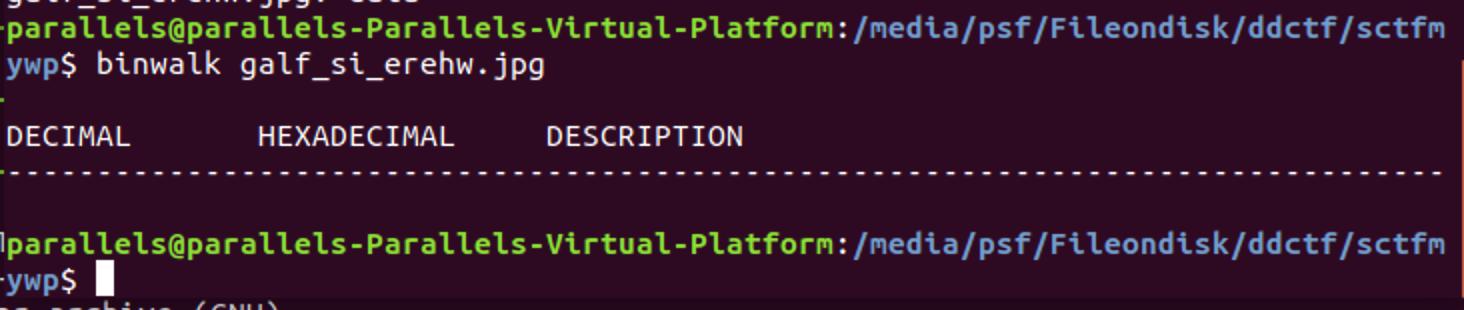
Based on the title, we're guessing it might be an inversion of hexadecimal.
Here we use the strrev function in PHP for this.
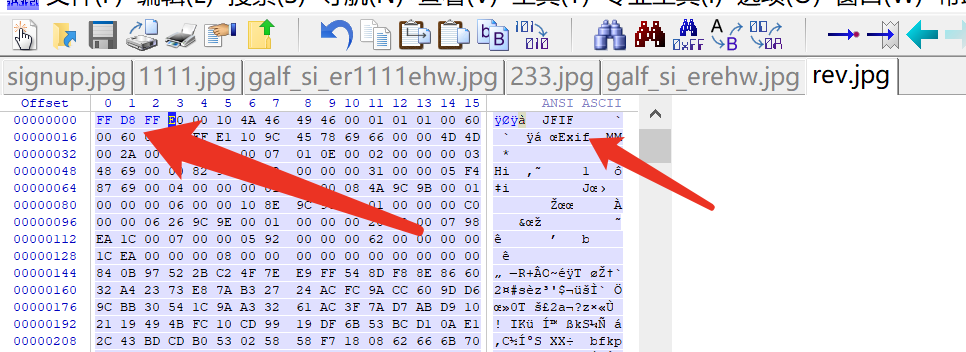
After processing, I opened it and found that it was still reporting an error, considered using winhex to view it, and found that it was a jpg file, so I added the file header(ffd8ff)
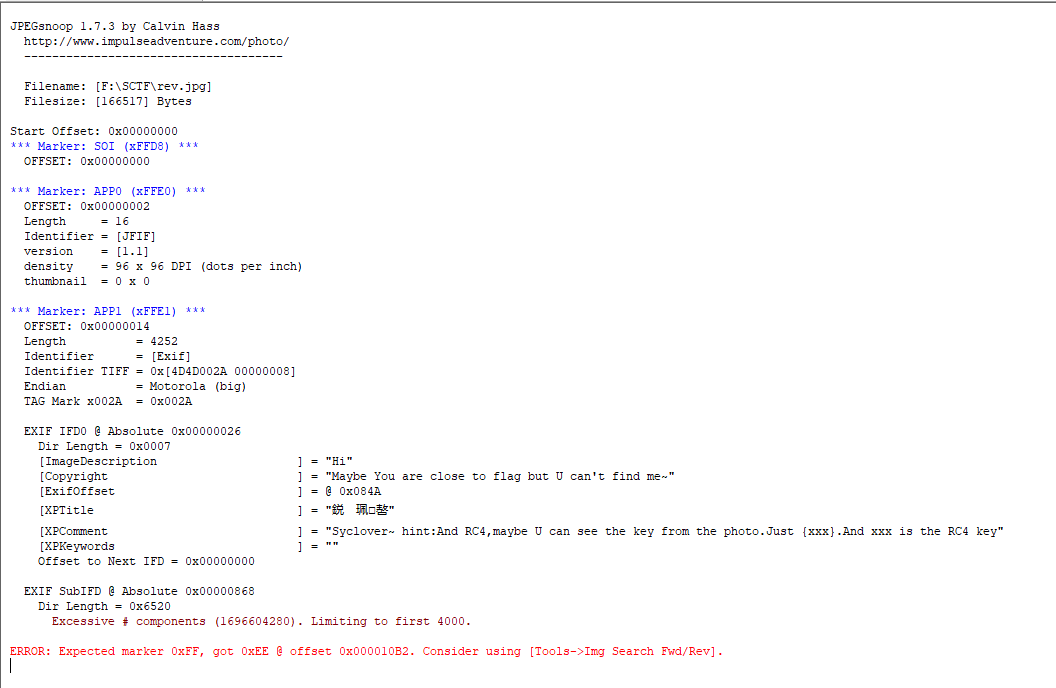
Continued to find hints that it is RC4 encryption, but still no flag. test is not LSB steganography, etc. continued winhex view.
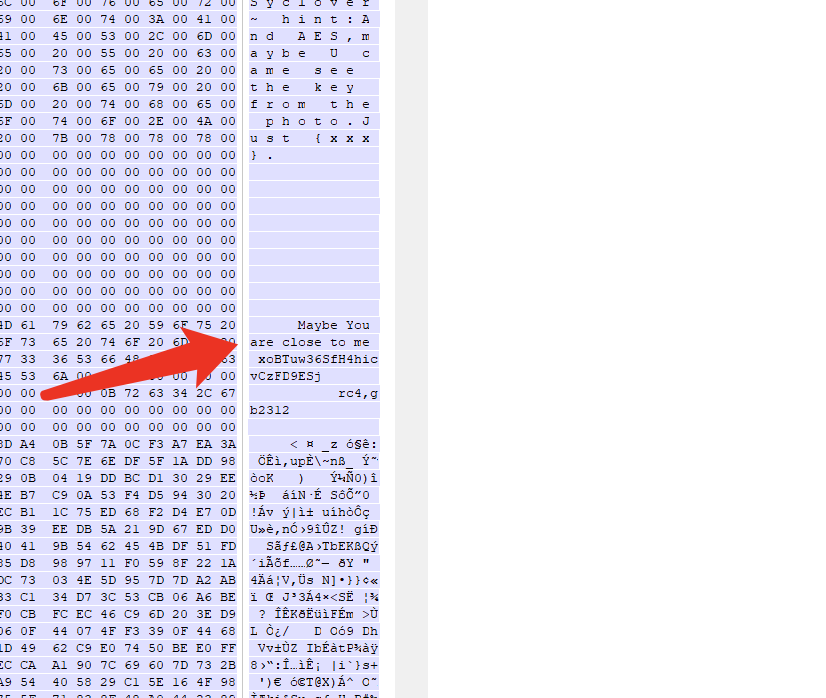
Suspicious strings found
xoBTuw36SfH4hicvCzFD9ESj
