Tags: memory_dump forensics volatility gimp paint
Rating:
## Memory 5
### Tags: Memory Forensics, Volatility, Memory Dump, MS Paint, Image Recovery from Process, GIMP
```
I'm an artist too, i love painting. I always paint in these dimensions 600x300
```
I solved this before Memory 4 because the MS Paint process looks more interesting than any other process. Seeing various other writeups and tutorial, I think this is the only way I would install GIMP unironically.
Starting up, of course, seeing the process list and get the PID of `mspaint.exe`.
```
python vol.py -f ../../FWord/foren.raw --profile=Win7SP1x64 pslist
```
```
...
0xfffffa8019ac0640 chrome.exe 3992 3700 14 216 1 0 2020-08-26 09:13:33 UTC+0000
0xfffffa8019bf2060 wuauclt.exe 1876 900 3 98 1 0 2020-08-26 09:13:33 UTC+0000
0xfffffa801adeaa40 mspaint.exe 1044 1000 7 133 1 0 2020-08-26 09:20:28 UTC+0000
0xfffffa8019bc0b00 svchost.exe 3284 488 7 110 0 0 2020-08-26 09:20:28 UTC+0000
0xfffffa8019bf7060 DumpIt.exe 1764 1000 2 52 1 1 2020-08-26 09:22:18 UTC+0000
...
```
After that, I dumped the memory for `mspaint.exe` with PID 1044.
```
python vol.py -f ../../FWord/foren.raw --profile=Win7SP1x64 memdump -p 1044 --dump-dir=../../FWord/
```
`-p` is for the PID of the specific process we want which memory to be dumped. If `-p` is not specified, by default it will dump all the process. `--dump-dir` is for the dumping output directory.
Now we have the memory dump, I opened up GIMP. I loaded the dump as `Raw image data`, and set the offset up until there's some image or solid color came up on the preview. Set the width and height to what the description tells us, 600x300. 6 million offset later we got the image.
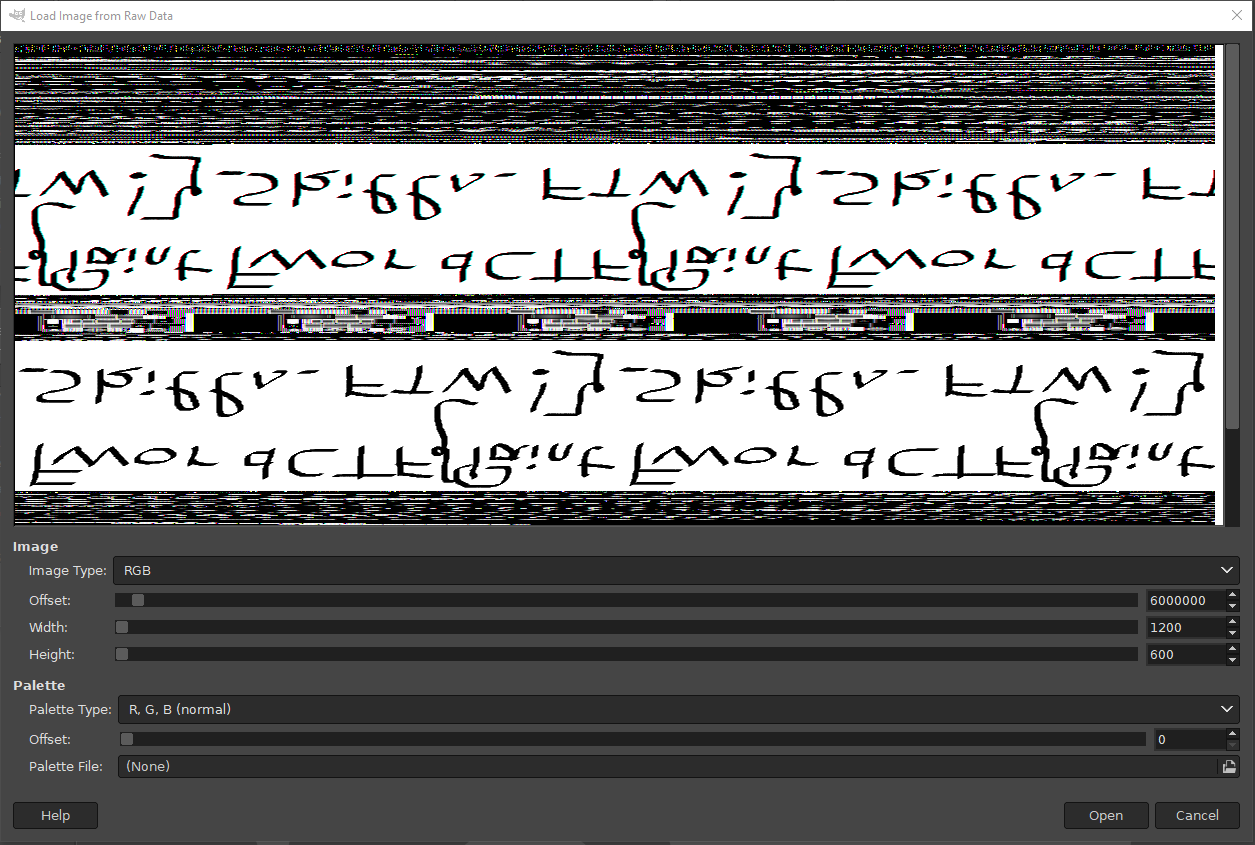
It's rotated and mirrored, but hey, if you're doing forensics you should be able to figure it out right?
Flag: `FwordCTF{Paint_Skills_FTW!}`