Rating:
Opening the binary in IDA, and looking at the imports, we can see `GetCommandLineA`, which is unusual.
I jumped to the first XRef to it, and putted a breakpoint. I then started the debugger, and obtained the following.
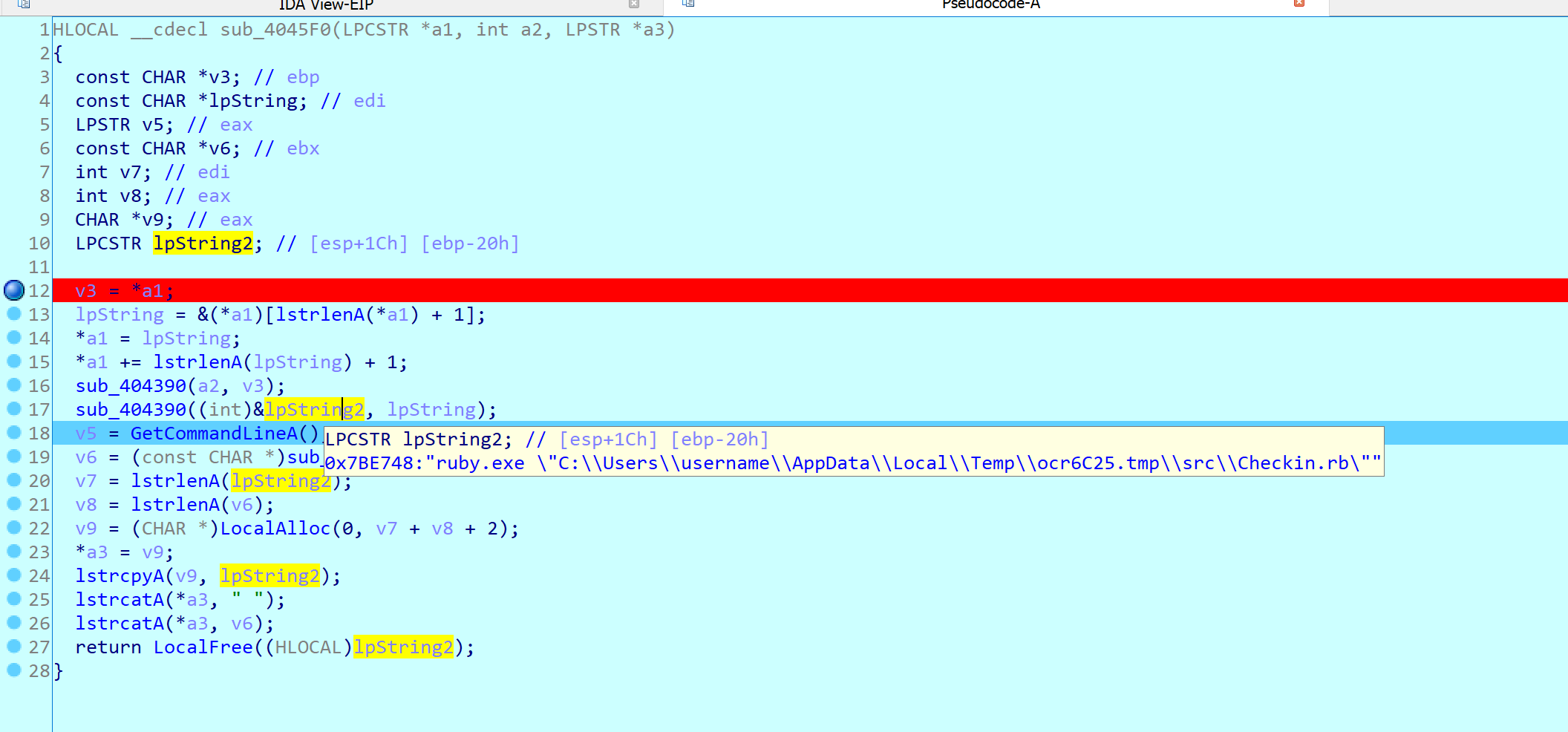
It is running the following ruby script
```ruby
require 'openssl'
require 'base64'
def aes_encrypt(key,encrypted_string)
aes = OpenSSL::Cipher.new("AES-128-ECB")
aes.encrypt
aes.key = key
cipher = aes.update(encrypted_string) << aes.final
return Base64.encode64(cipher)
end
print "Enter flag: "
flag = gets.chomp
key = "Welcome_To_GACTF"
cipher = "4KeC/Oj1McI4TDIM2c9Y6ahahc6uhpPbpSgPWktXFLM=\n"
text = aes_encrypt(key,flag)
if cipher == text
puts "good!"
else
puts "no!"
end
```
I modified it for the following
```ruby
require 'openssl'
require 'base64'
def aes_decrypt(key,encrypted_string)
aes = OpenSSL::Cipher.new("AES-128-ECB")
aes.decrypt
aes.key = key
cipher = aes.update(encrypted_string) << aes.final
return cipher
end
key = "Welcome_To_GACTF"
cipher = "4KeC/Oj1McI4TDIM2c9Y6ahahc6uhpPbpSgPWktXFLM=\n"
puts aes_decrypt(key, Base64.decode64(cipher))
```
Which outputs
```
GACTF{Have_a_wonderful_time!}
```