Tags: reverse engineering
Rating:
### I just relized when i run this program using ltrace, program is do memcpy.

### so i think the flag maybe saved on memory, so i open it with gdb and add breakpoints after program doing memcpy.
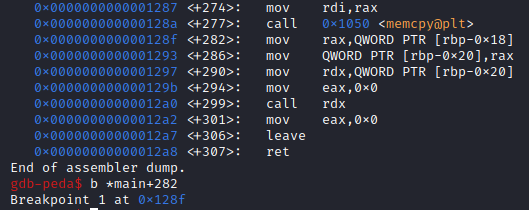
### and i do dump memory.
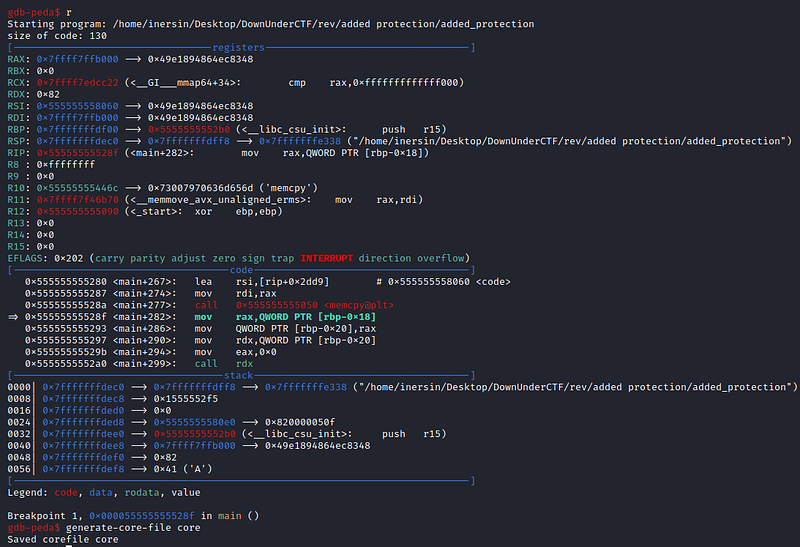
### and i open file that contain memory dump from the program using hexeditor and search for flag format.
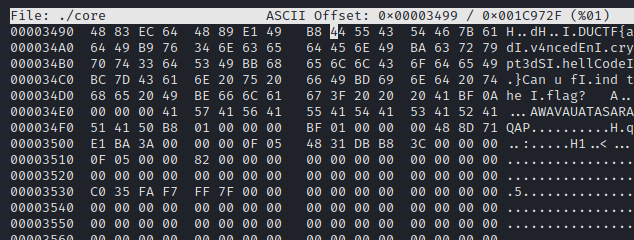
> DUCTF{adv4ncedEncrypt3dShellCode}
[my blog](http://medium.com/@InersIn)