Tags: javascript sqlinjection
Rating: 3.0
No brute force.
Seeing the login page you expect brute force...
Lets try admin / admin - nope.
Hmmmm....
So lets try sql injection - what database - lets think something realy basic and general if query has username = '$POST['username']' thingy - You know what I mean...
so lets try ' or id = '1 as username and password to get 2 fields at once
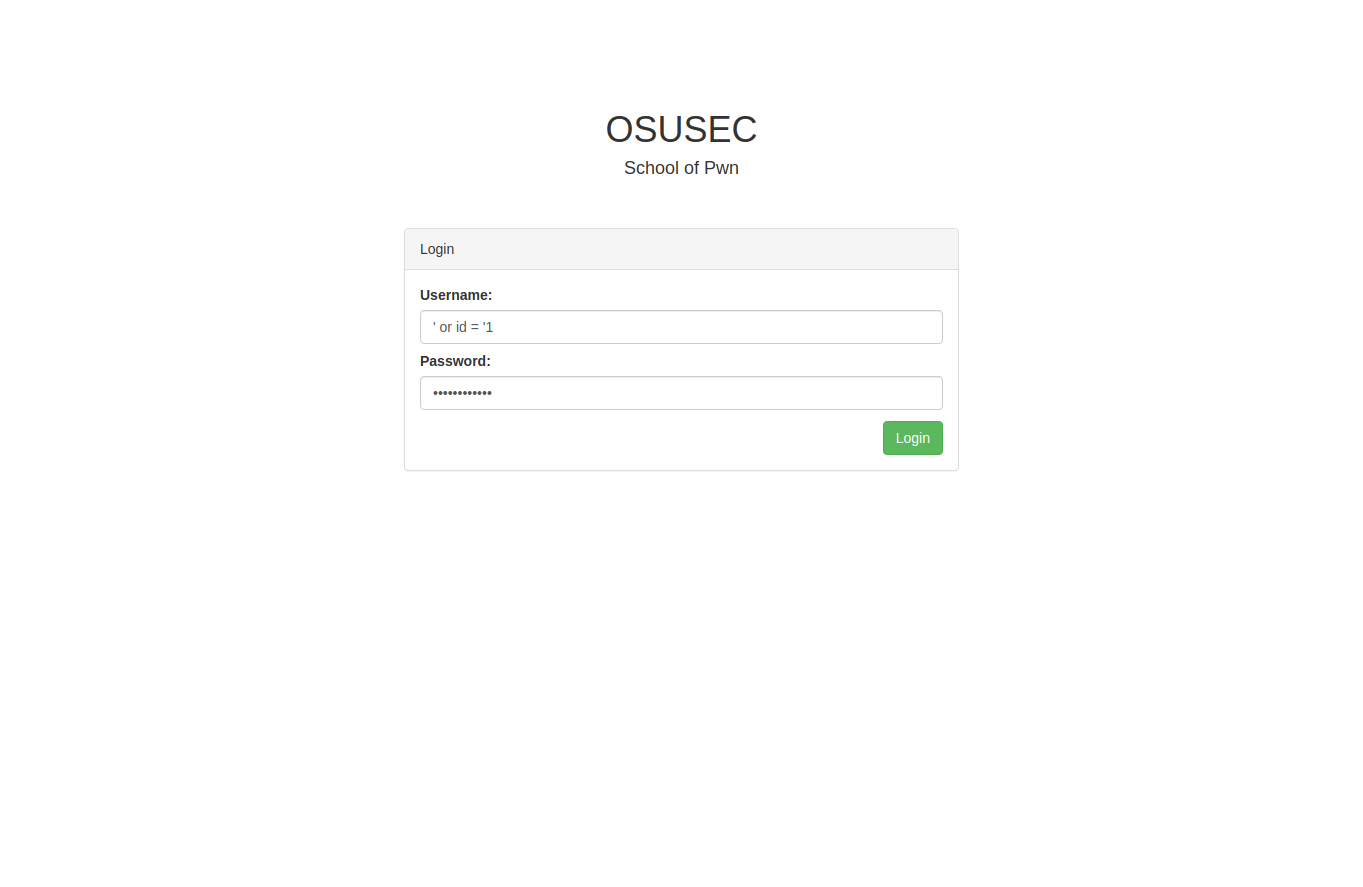
And we are in... But, but there are no niks to edit the students...
So lets search for the user that has admin priveleges...
But how do I fing out if the user is admin...
[dasboard code](https://github.com/slyher/CTF/blob/main/damctf/page_sourcefiles/OSUSEC%20-%20Dashboard.html)
Lets take a look at the source code - we get some interesting javascript at the bottom:
```
<script>
var staff = {
admin : false,
name : 'rhonda.daniels'
}
</script>
<script src="js/app.min.js"></script>
```
After 4 tries there are no more users in the database to log in :(
On the discord chanel there is an information that ordinary access is enough to get the flag.
So let's think this through...
After trying to change the staf.admin = true in the "chrome dev tools" I checked what there was in the javascript app.min.js
[javascript](https://raw.githubusercontent.com/slyher/CTF/main/damctf/page_sourcefiles/OSUSEC%20-%20Dashboard_files/app.min.js)
There is somting creating the links to edit. Without thinking much lets paste it to the console and execute it.
Thing worth mentioning is that the html that element with class student-link looks like this: `<td data-id="TXlyb25fV2lsa2lucw==" class="student-link">Wilkins, Myron</td>`
Lest click the first link that was generated by the javascript we get an edit form, but wait we need to edit it for Natasha Drew - time to take a look at the data-id value- it seems to be bese64encoded string (the two equal signs are a tell)
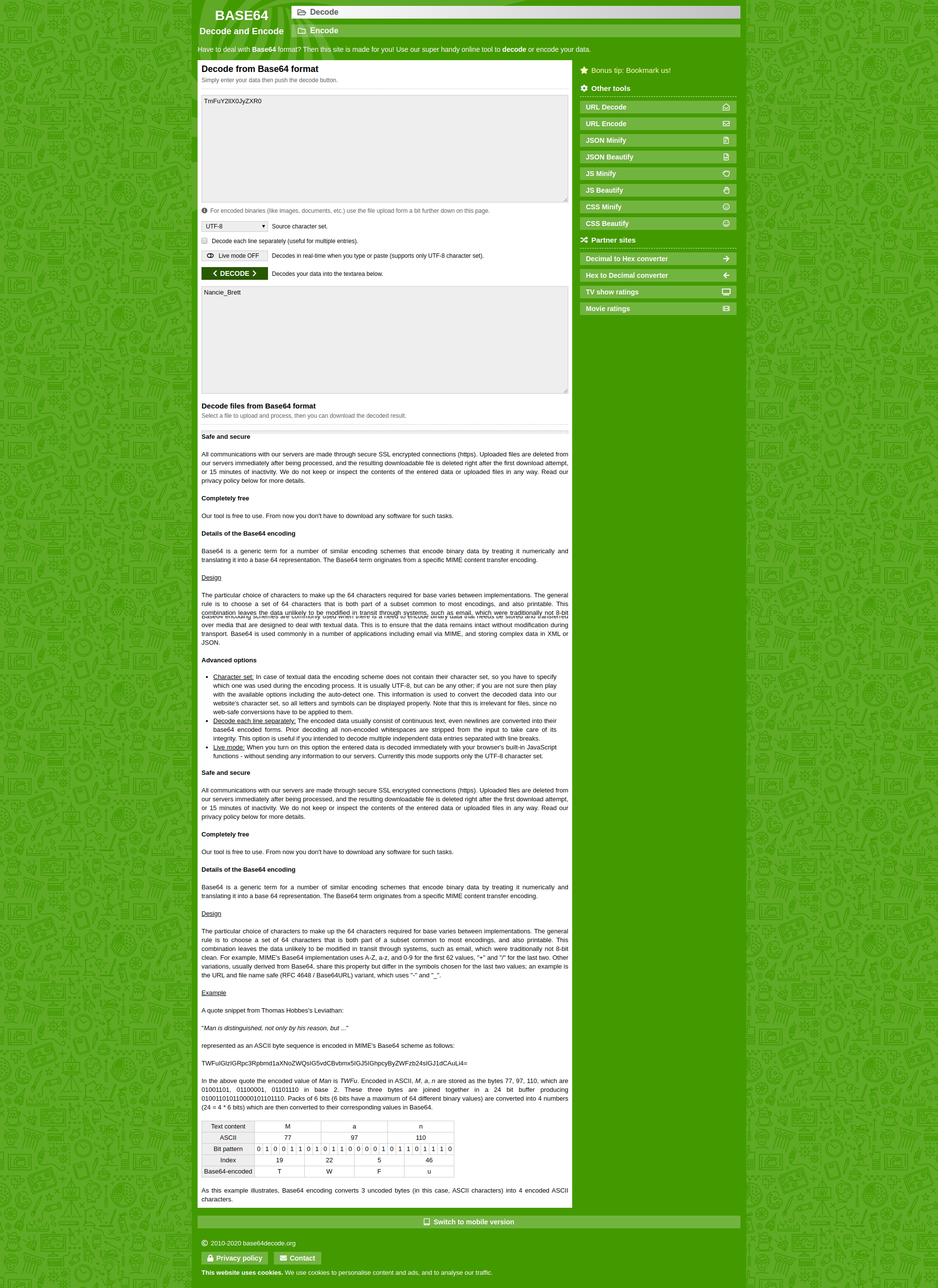
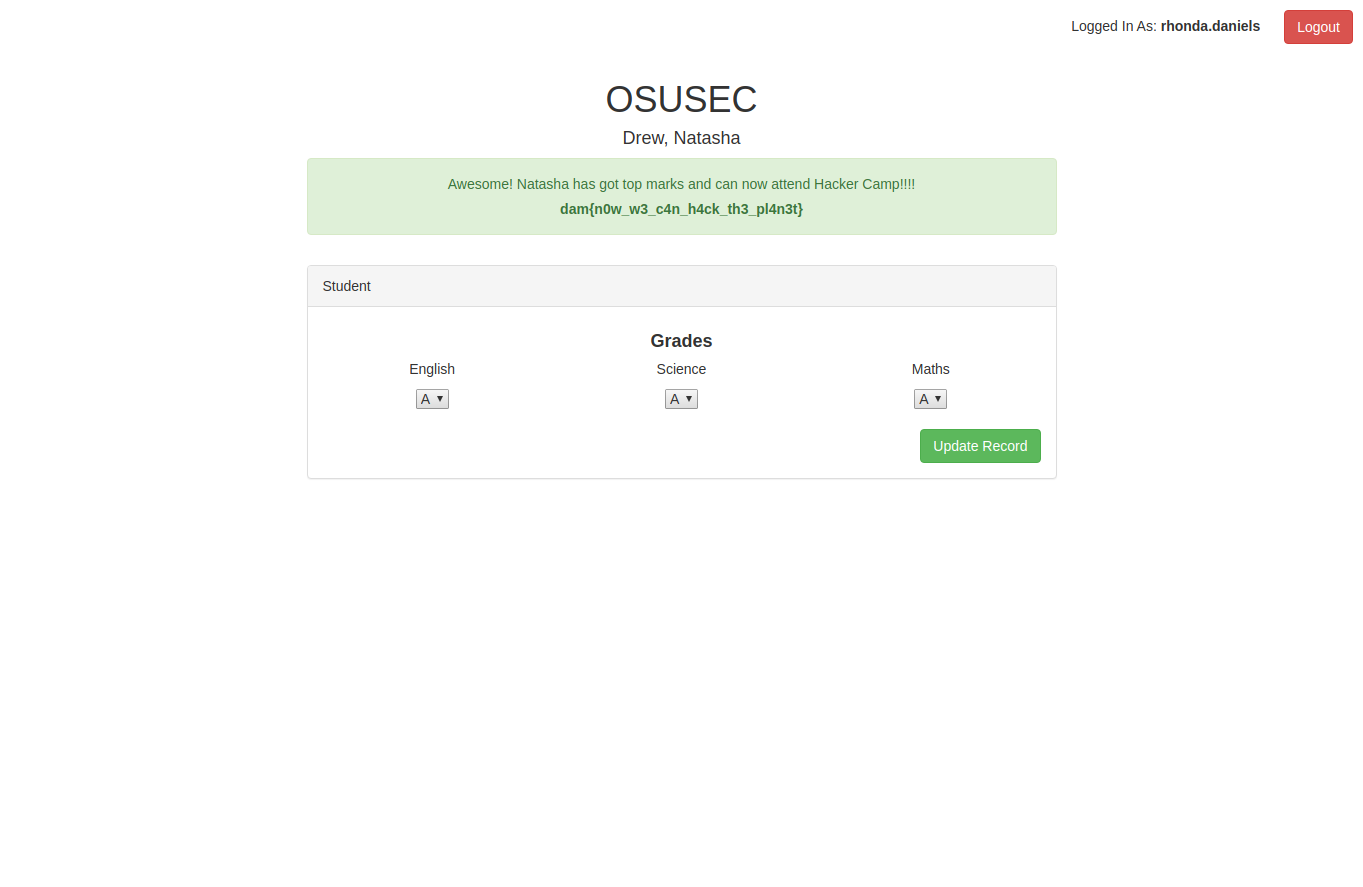
After decoding it online we get Myron_Wilkins- lets try to encode Drew_Natasha and get edit form for her.
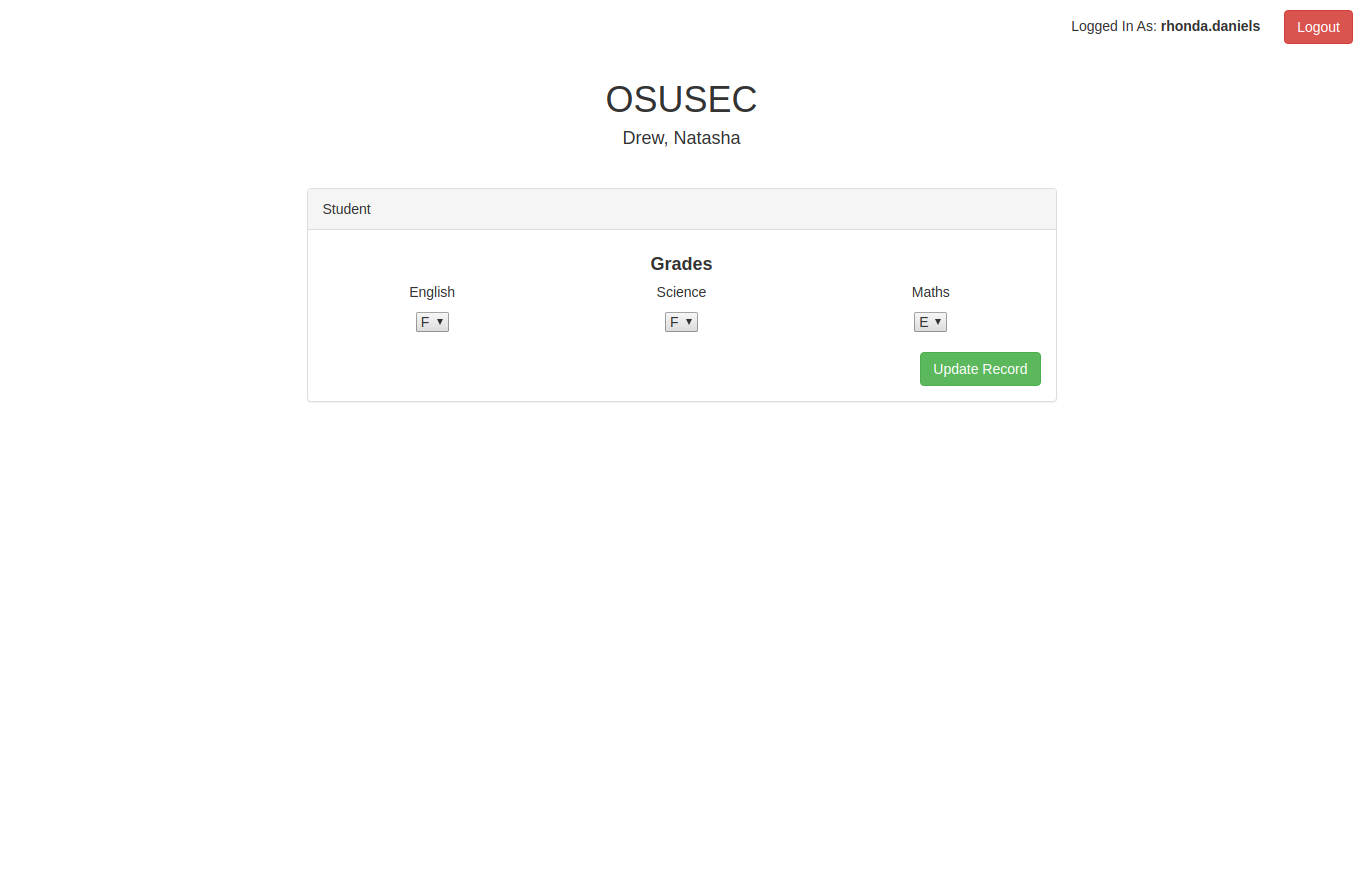
After setting Natasha'a grages to A's and submitting the form we get the flag