Tags: baby crypto
Rating: 5.0
> Write-up and Inital setup to re-create the challenege in your own system and follow the solution.
The challenge is cateorgorized as crypto hinting what vulnerbailites to look for in the source code downloaded from the CTF website.
### **The target Website looks as show below**
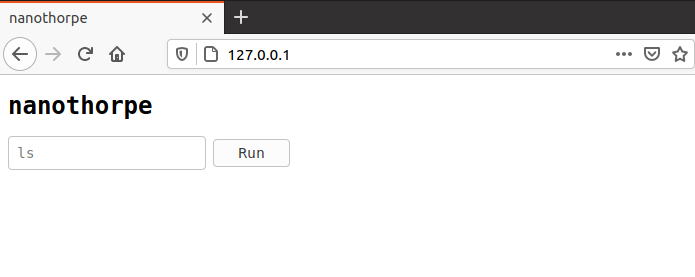
It makes two Http:// GET requests. One to “**authorize**” API and another to “**run**” API.
As the name suggest one API does the user input validation and generates a signature, the other uses the signature to verfiy the inputs and runs the user inputs as command to provide the final output.
Run API end-point is accessible to public internet (in our case the host system), anyone can send a maliciously crafted the request to run API end-point, if they have a valid signature of the data.
Challenege is around finding a vulnerability in the signature (MAC) generation and exploit it to get the flag.