Rating: 3.0
# web flask SSTI
# recon
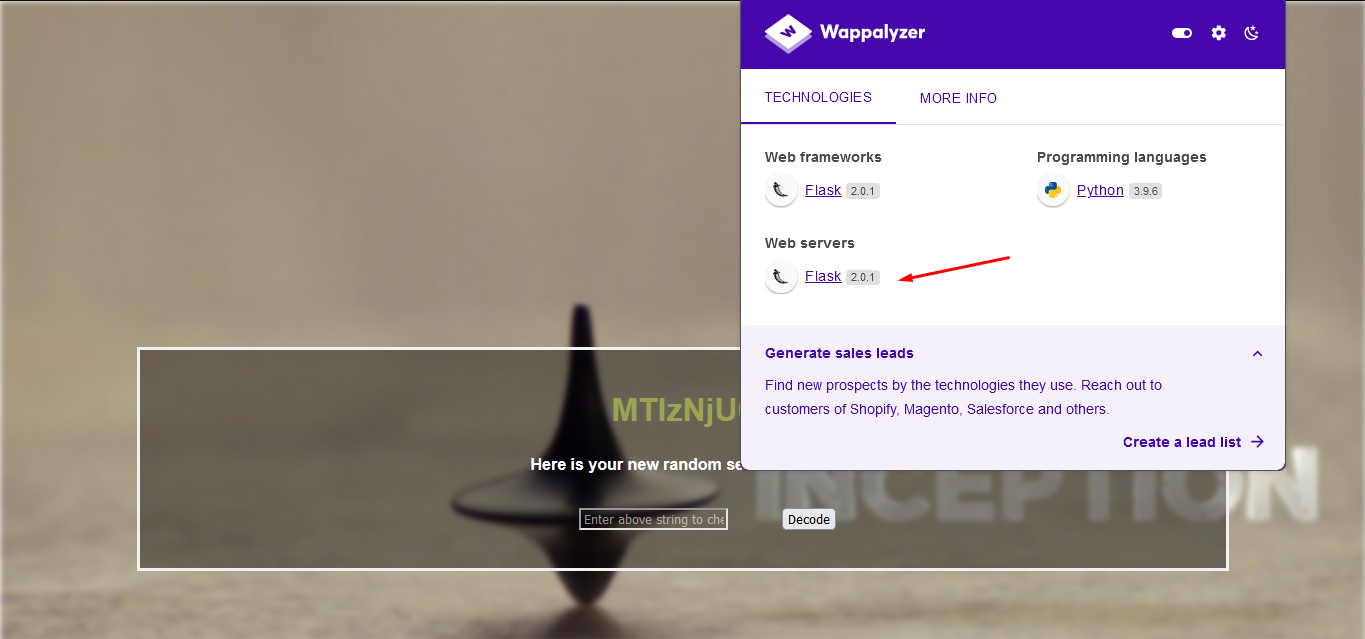
the function of this site is base64 decode the inserted value to the actual value
nothing else and i think it's SSTI
# quất
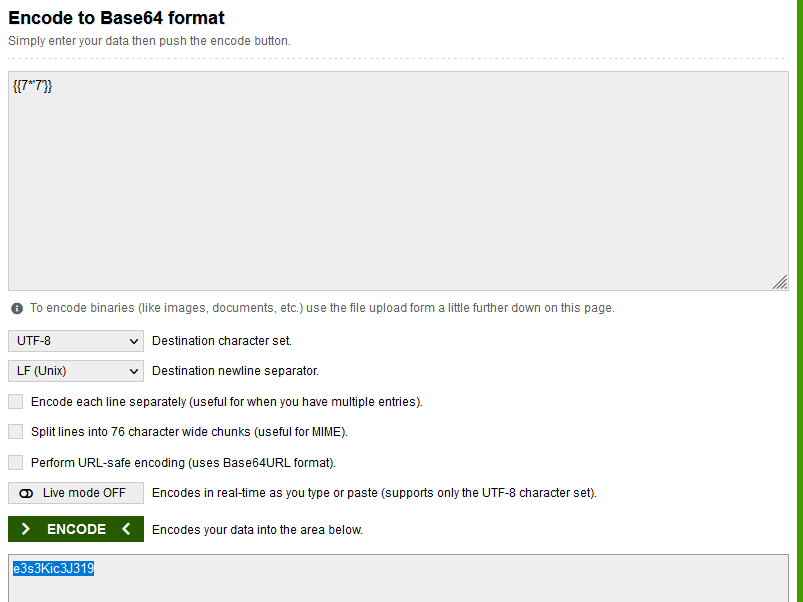
and decode
oke ! next i find payload in here
and result :
# FIND Flag
```
Note: Flag is located in etc directory
```
## LS /etc
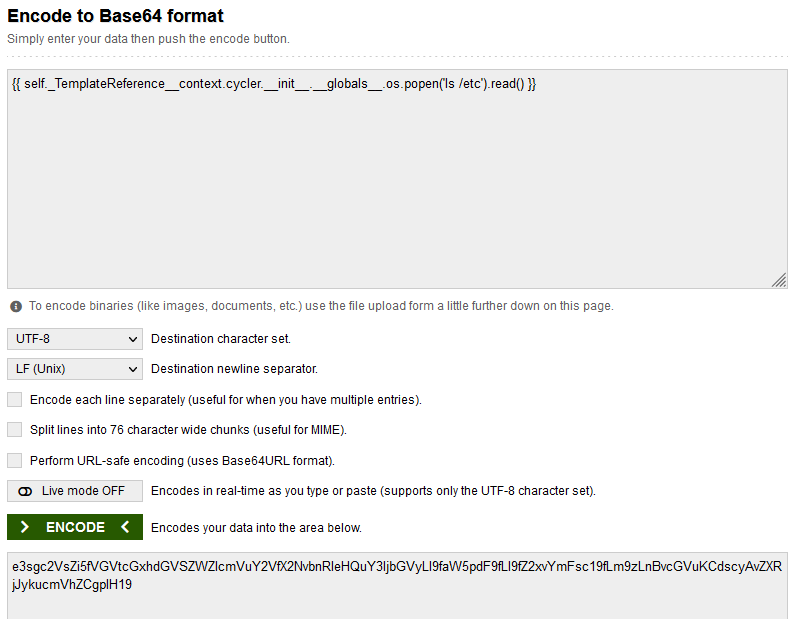
result: found flag.txt
## cat flag.txt
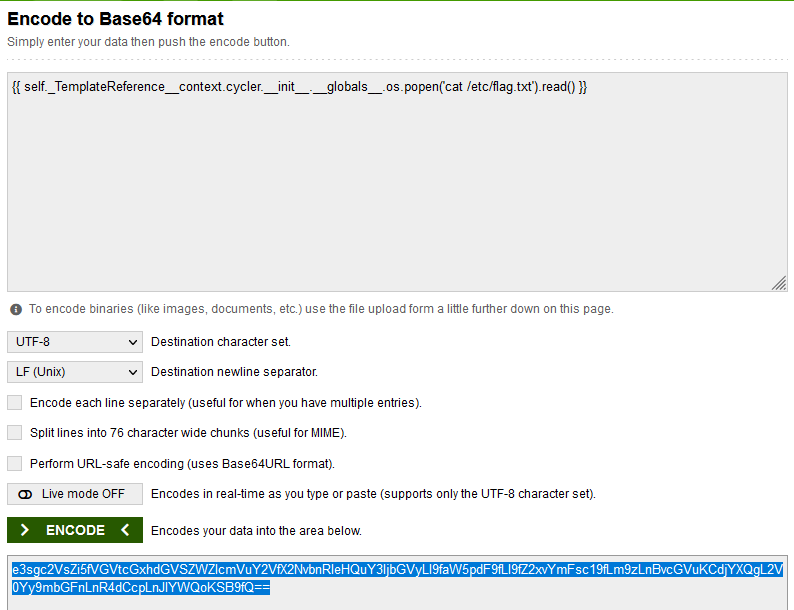
result:
Congratulation for my team AUZ1 , we are new team without exp