Rating:
**Task:** Luciafer cracked a password belonging to the victim. Submit the flag as `flag{password}`.
First, I had no idea about what to do. So, I unlocked 2 hints. One of them said that the password was transferred in plain using `non secure` protocol. The other hint, said that when the password was typed correctly, a plain text is returned showing that connection is ok.
So, I guessed that might be FTP protocol. I searched deeply and I found that Luciafer tried to crack the FTP password by using a lot of passwords until one of them works. I scrolled down until I found the connection established and I looked for the last password sent.
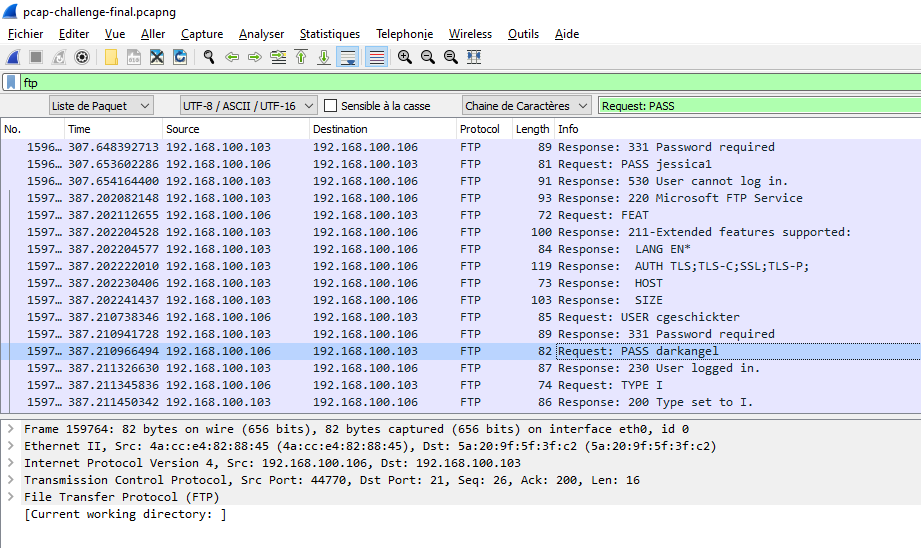
Now as I solved it, I found a faster way. That's to filter for successful FTP response (230) : `ftp.response.code == 230`, then follow the TCP stream (Right click and select **Follow | TCP Stream**) of that communication to find the password entered.