Tags: sqli
Rating: 3.0
We are greeted with a login screen.
Flag is in the database so at first I thought I would need to do some SQL injection to get the flag from the table.
We have credentials from the database.sql file
Logged in with admin on my local instance and immediately saw the flag. Is it that easy?
No, on the remote website we get an invalid password. However it seems we have SQL injection directly on the login screen. With the standard sql injection ```' or 1=1-- -``` we get logged in as manager.
We do get a JWT token however the secret is random.
With this SQL injection, we were able to get on as admin:
```
admin'-- -
```
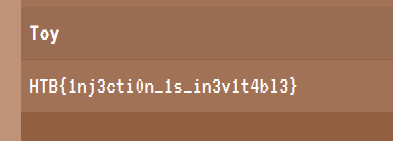
HTB{1nj3cti0n_1s_in3v1t4bl3}