Rating:

Unzipped the provided file and got an encrypted.txt file
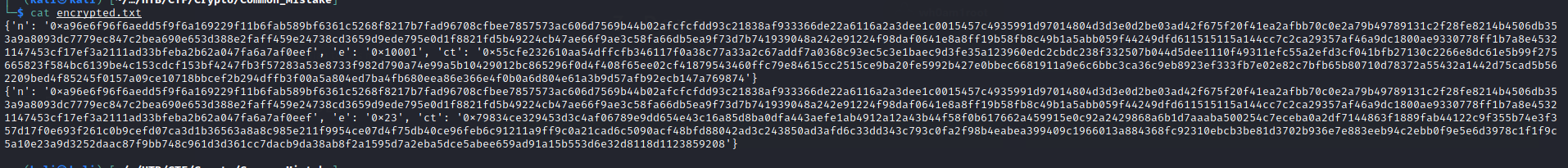
Considering we have the same n and two different e and c means this should be a Common Modulus attack. The title of the challenge hints at it as well.
I converted the hex strings into int using python.
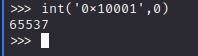
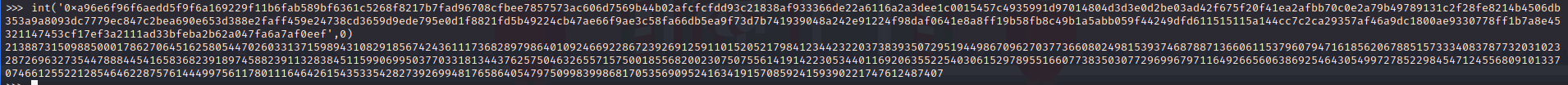
I'm not great at scripting crypto stuff but I did find this script.
https://raw.githubusercontent.com/a0xnirudh/Exploits-and-Scripts/master/RSA%20Attacks/RSA%3A%20Common%20modulus%20attack.py
After fixing the identation issues, I pasted the n, c1,c2, e1 and e2 and I ran the script and I got a decimal value.
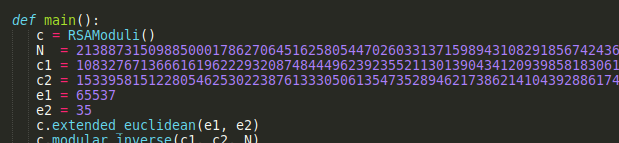
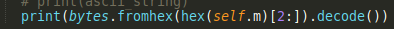
I modified the script some more to convert the decimal value to hex and then to ASCII.
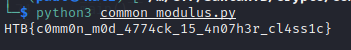
HTB{c0mm0n_m0d_4774ck_15_4n07h3r_cl4ss1c}