Rating:
# How's the Shark
This time we got an pcap file to look into. When we first checked the TCP stream we found out that this was a capture of a client server connection to a webside. The first thing we checked was the easy one by searching for the flag via the flagformat *KCTF*. Funny enough the creators put a fake flag into the capture.
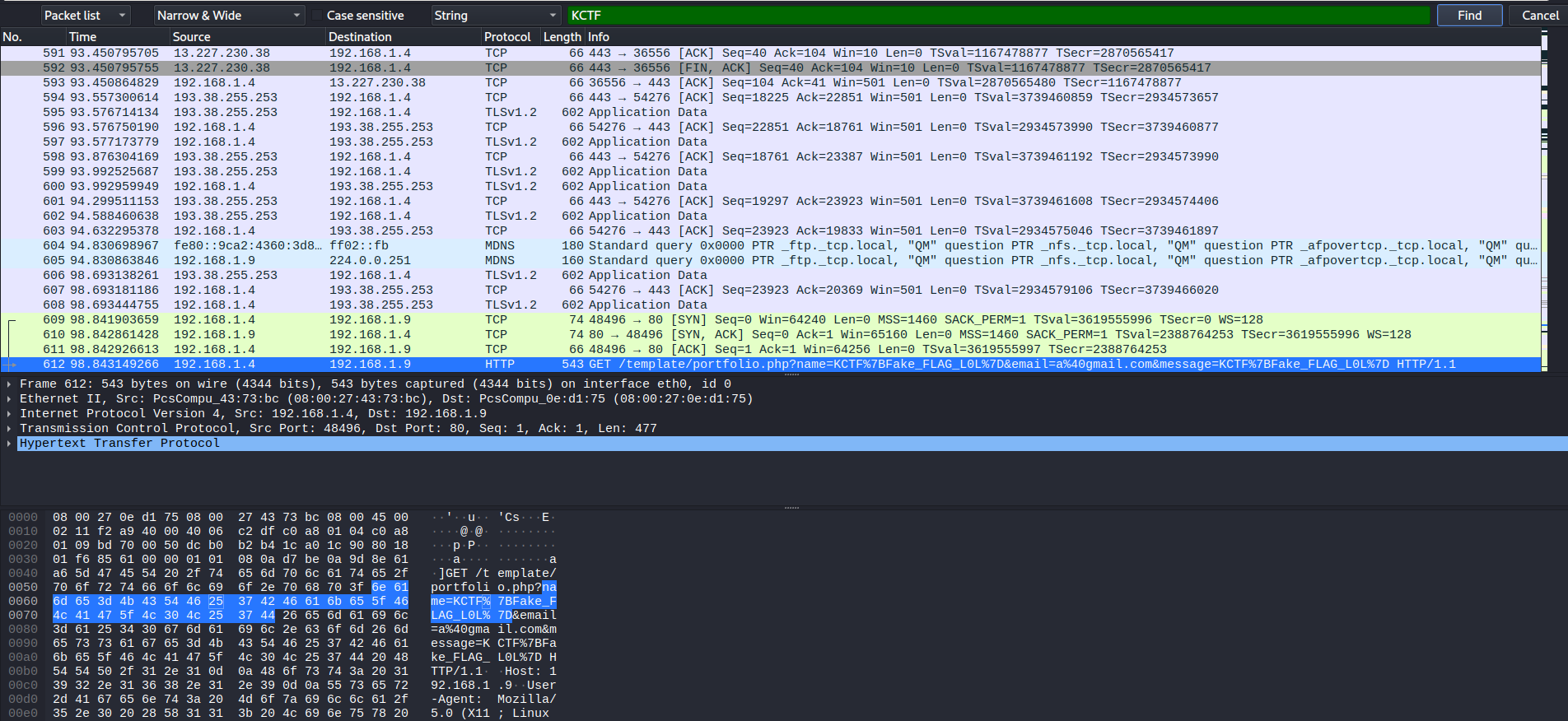
You never know what chall creator think so we tried *KCTF{Fake_FLAG_LOL}, with no success. Next step was that nothing was in String format we checked the files transfered during the connection by exporting all of them to our local drive. Lots of garbage in it but one which got our attention. Not sure why but something special was about it, something (⋆._.)⊃▁⛥⌒*゚.❉・゜・。.

With that we had our flag *KCTF{A_ShaRk_iN_tHe_WirE}*
Our [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/KnightCTF_2022#hows-the-shark) and [webpage](https://bsempir0x65.github.io/CTF_Writeups/KnightCTF_2022/#hows-the-shark)