Rating: 5.0
# Enumeration
In home directory of `leonardo` user there are two files:
- noteToAdministraotr.txt
- list.txt
`OneRule` could be a hint to `OneRuleToRuleThemAll` hashcat rule.
`Linpeas` output showed that `sudoers` file was readable, and user `leonardo` can run `diff` binary as root.
With that reading `/etc/shadow` is possible.
To crack hashes custom wordlist was made that contained favouire songs and artists from `list.txt` file.
```
The Notorious B.I.G. - Juicy
The Notorious B.I.G
Juicy
Snoop Dogg - Who Am I
Snoop Dogg
Who Am I
Kanye West - Diamonds From Sierra Leone
Kanye West
Diamonds From Sierra Leone
Outkast - Southernplayalisticadillacmuzik
Outkast
Southernplayalisticadillacmuzik
Drake - War
Drake
War
Alpha Wann - ÇA VA ENSEMBLE
Alpha Wann
ÇA VA ENSEMBLE
Freeze Corleone 667 - Freeze Raël
Freeze Corleone 667
Freeze Raël
Alpha Wann - apdl
Alpha Wann
apdl
Lomepal - A ce soir
Lomepal
A ce soir
Paris c'est loin - Booba
Paris c'est loin
Booba
```
And as hinted in `noteToAdministrator.txt` this was ran against hashcat `OneRuleToRuleThemAll` rule.
```bash
hashcat --force leonardo_w -r OneRuleToRuleThemAll.rule --stdout >newword
```
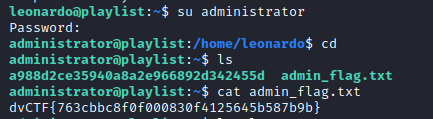
With that custom wordlist `administrator` password was cracked.
`administrator:oLmepaloLm`
This set of credential allowed to login as `administrator` user.