Rating:
# Reversing : Keygenme
## Description
Can you get the flag?
## Solve
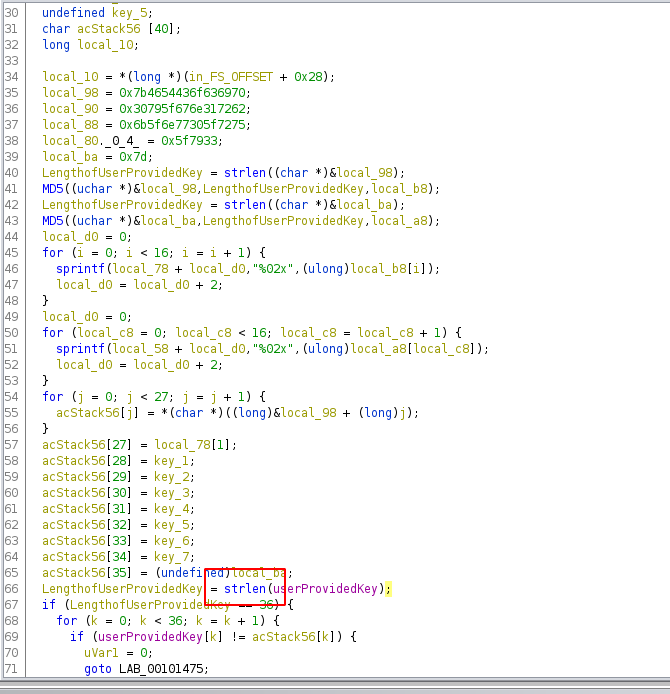
Running through the code in ghidra I was able to locate the comparison its doing with the provided user key and the expected characteristics about the key comparison.
The key is expected to be 36 chars long
The key starts with `picoCTF{br1ng_y0ur_0wn_k3y_` and ends with `}` leaving 8 bytes to work out
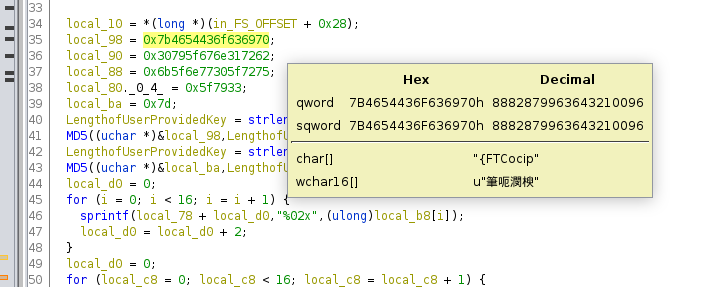
We can target the strlen function to get close to our comparison by opening the binary with GDB and setting a breakpoint for `strlen`
```bash
break strlen
```
Running the application now with a dummy key filling the blank space with `AAAAAAAA` will help us to process as the hex value of `A` is `0x41`.
```
r <<