Tags: pcap
Rating:
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/AngstromCTF_2022/#shark1) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/AngstromCTF_2022#shark1) out
Based on the name and the fact that we get a pcap file its time to bring out wireshark or whatever package inspection tool you like. (o^ ^o)
Once uponed up with wireshark we can see that we have a quite short recording with 27 packages. So you could just search for actf as first part of each Flag which gives you:
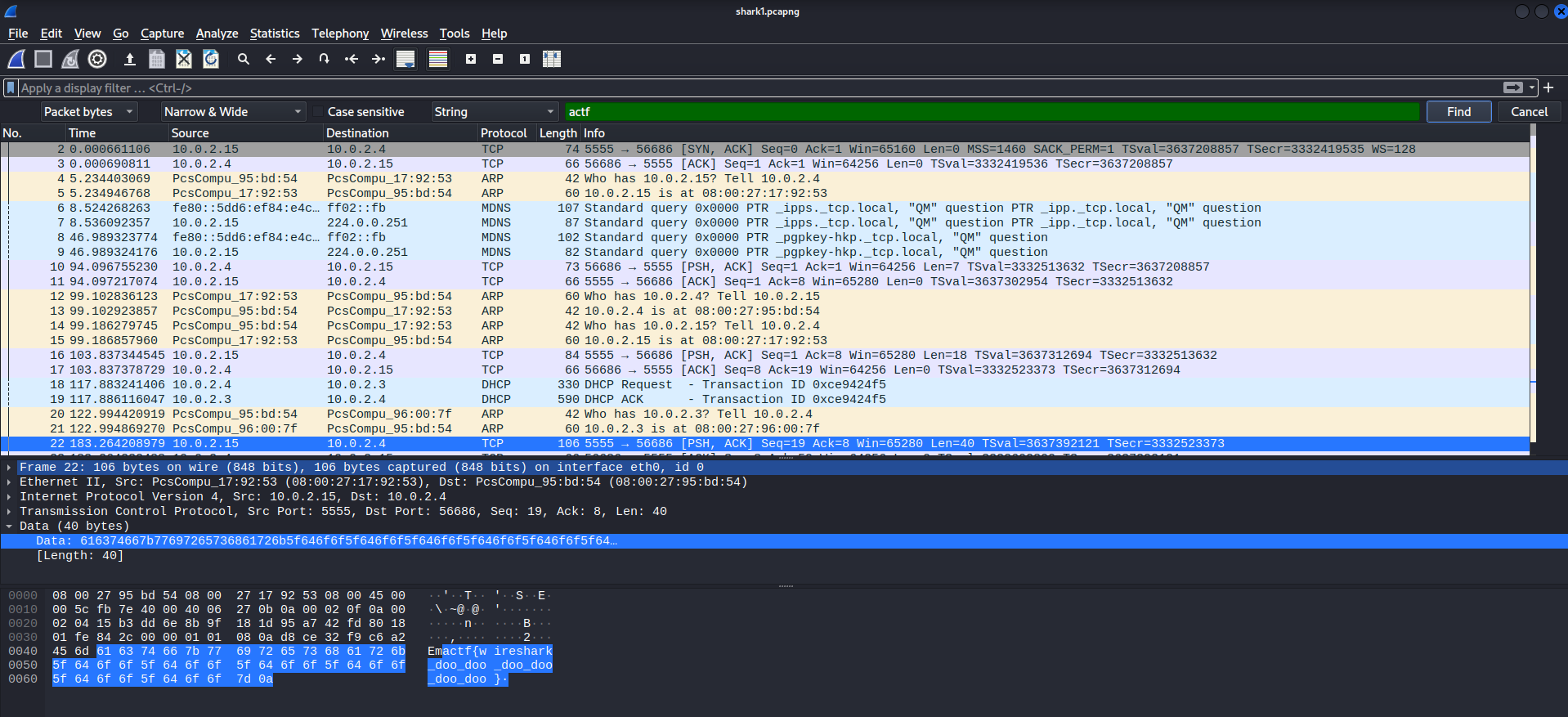
But this is too easy. We like to understand the conversation happening so we followed the TCP Stream:
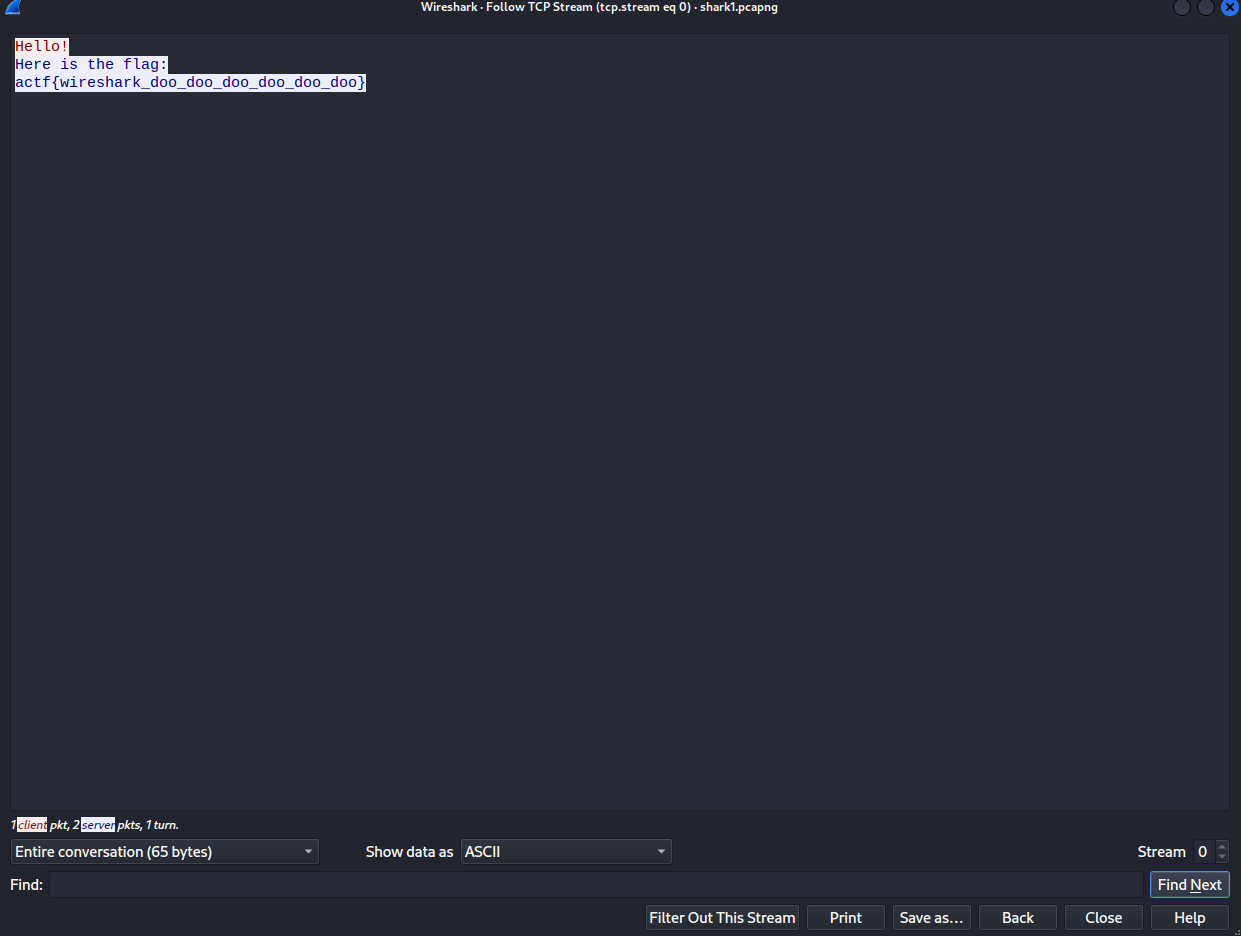
which gives us a way easier method to copy paste the flag (o・_・)ノ”(ノ_<、).