Tags: pcap
Rating:
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/AngstromCTF_2022/#shark2) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/AngstromCTF_2022#shark2) out
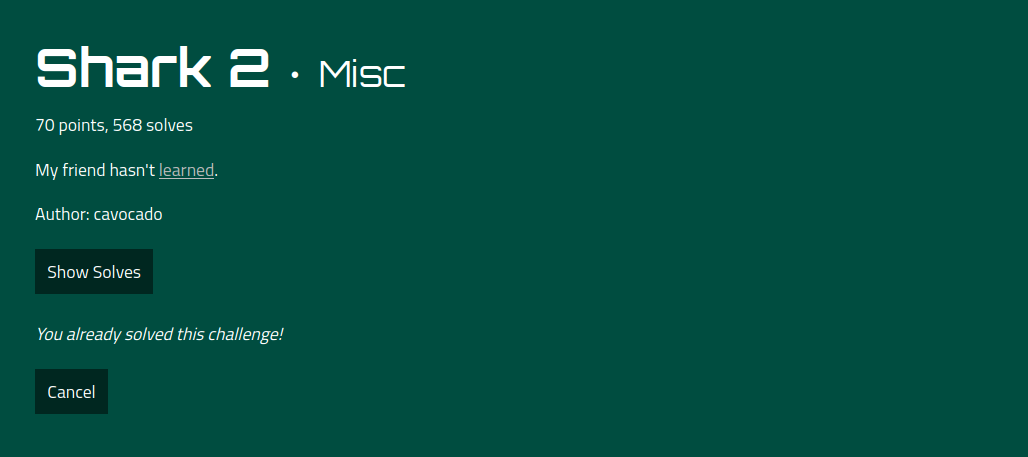
Followed by Shark1 we thought why not do Shark2 ? So we did. Again we got a pcap file to work with. So we used the follow TCP Stream method to see if something interesting comes up. Once we went trough the different streams we saw in tcp.stream 1 an interesting message.
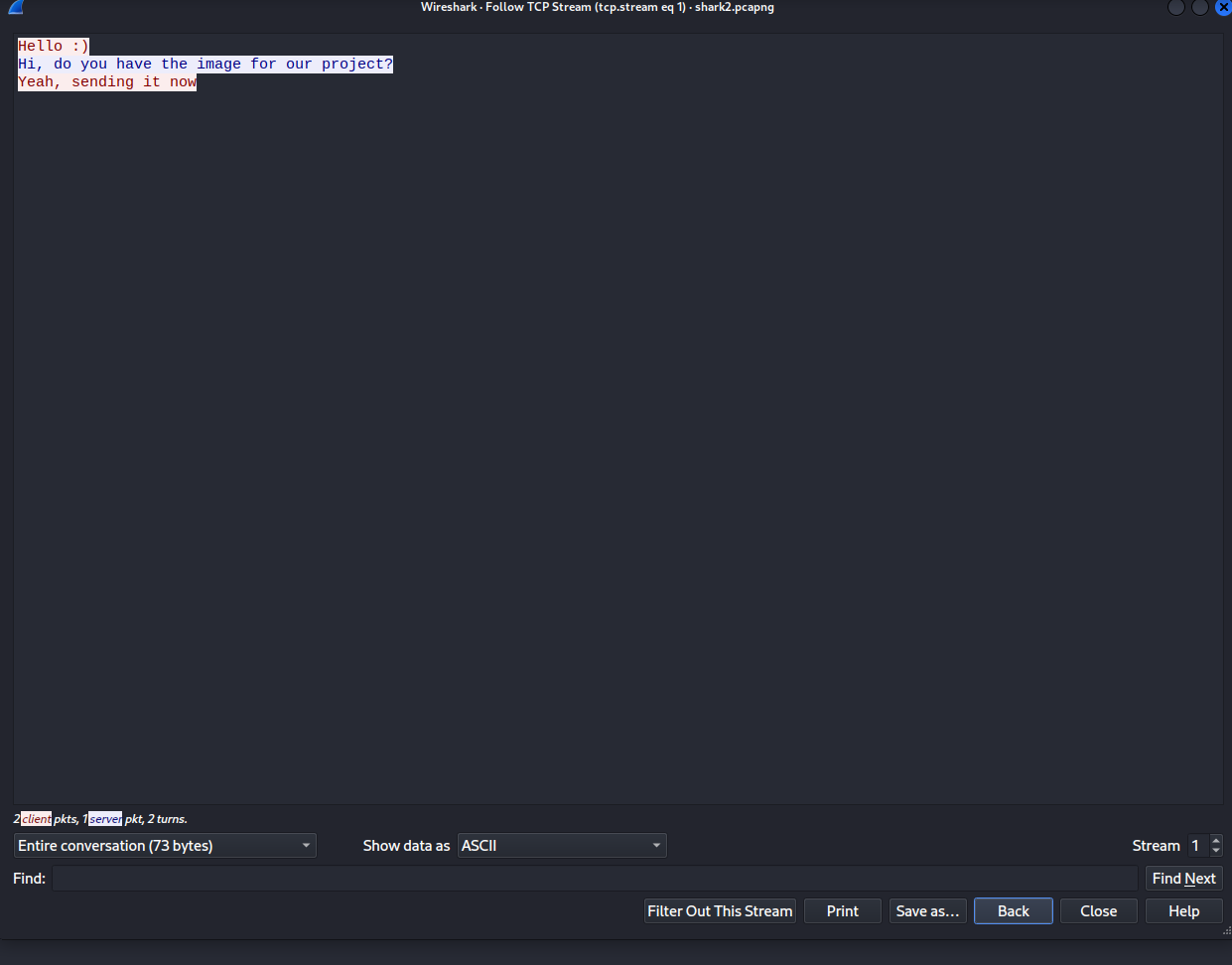
So we were pretty sure that the flag is hidden within the next TCP Stream.
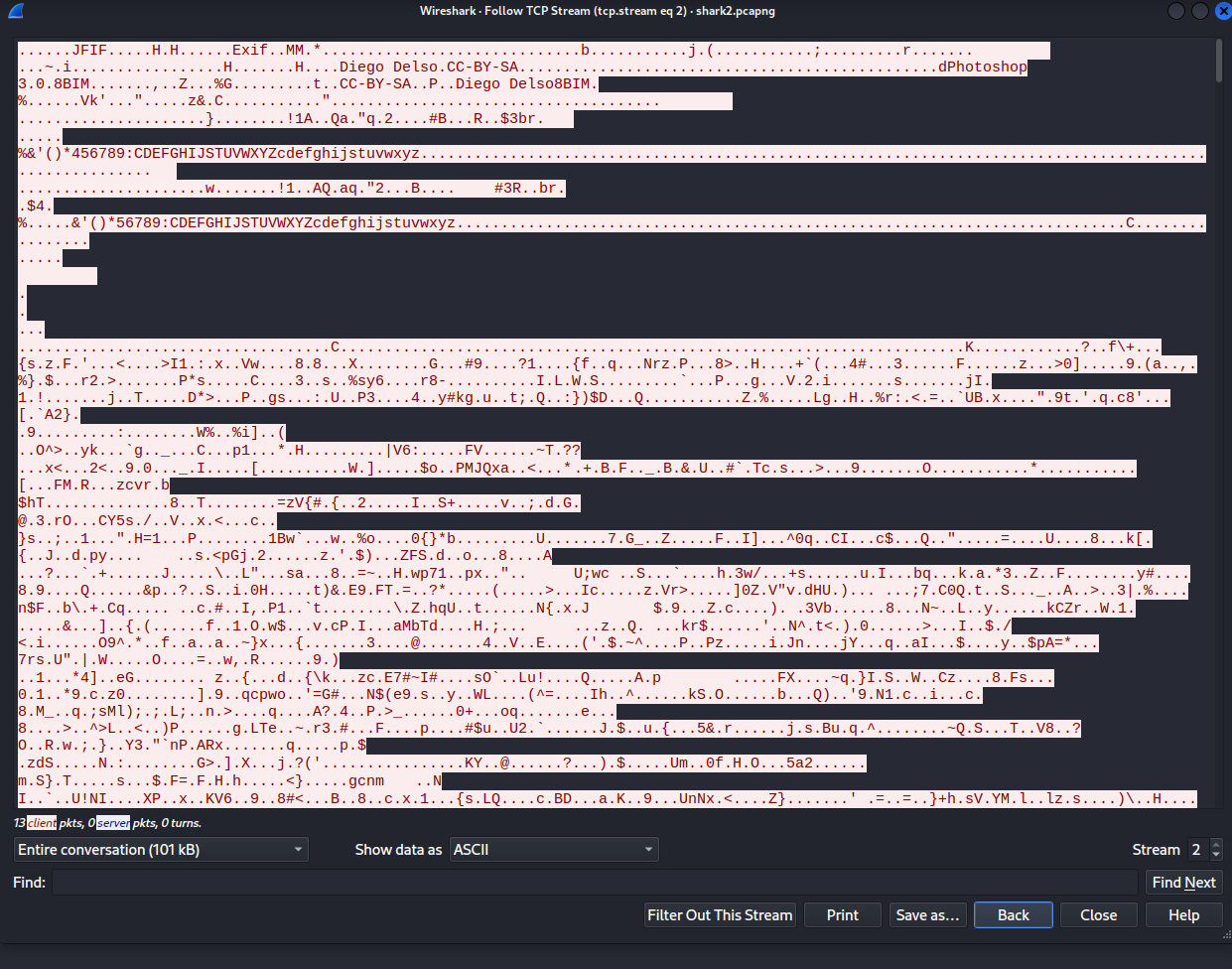
So based on words like photoshop which is a image editing program we concluded that its probably a picture what was sent here. But when we checked if we can export the content of a HTTP connection wireshark said "no no there is nothing" (#><).
So we then googled the file header info a knew then that [JFIF](https://en.wikipedia.org/wiki/JPEG_File_Interchange_Format) is actually something like a jpeg. So the easy way people probably used is just to export the TCP stream in raw format and pingo. But not us we are not so clever ヽ༼௵ل͜௵༽ノ.
What we did is used the tool foremost on the pcap file which found also this header in the pcap file and extracted for us the jpeg. Not sure why but the exported one is a bit glitchy so we have unique one.
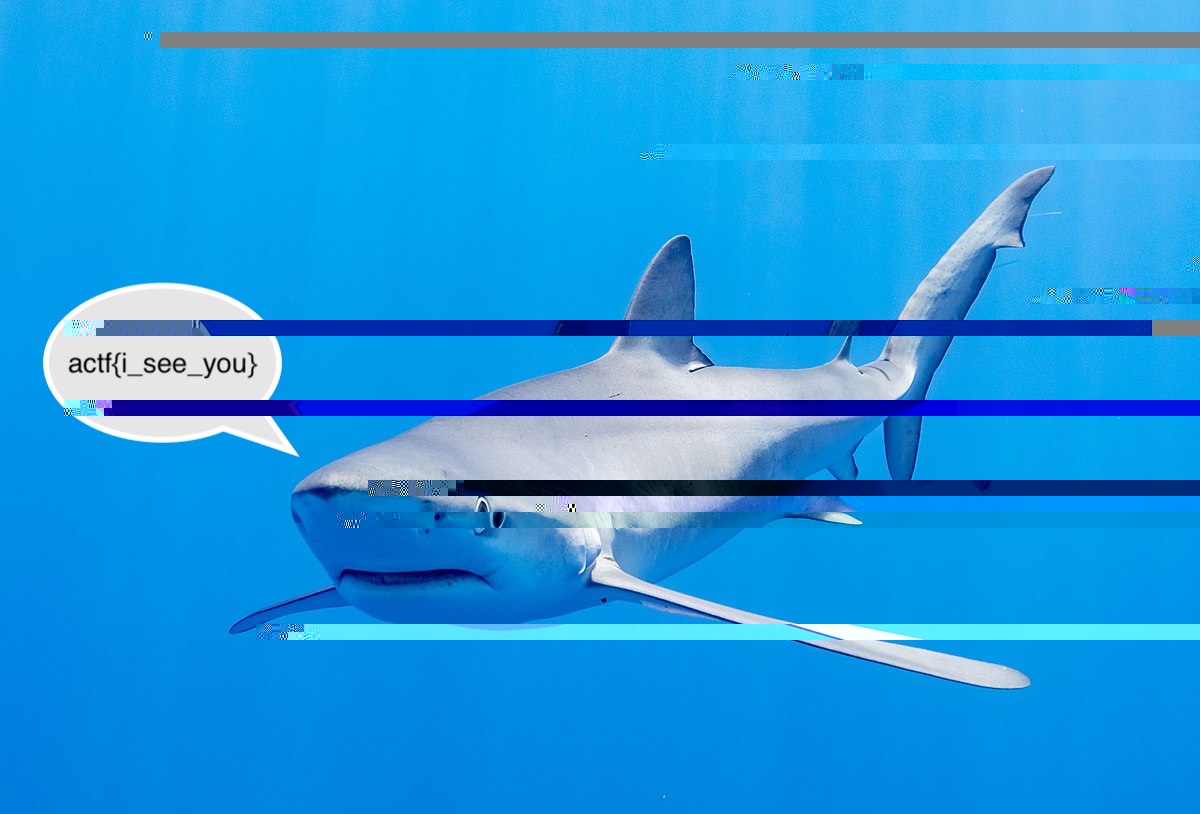
Another one solved, good run !