Tags: forensics
Rating: 4.0
## Alpine 2:
### Description:
```
What was the IP address of the attacker? (Note: Matt Johnson never logged in remotely.)
Flag format - byuctf{ip_address}
```
## Solution:
Alpine 2 is a medium difficulty forensics challenge, same as alpine 1 we have to investigate the same system and answer some questions about the attacker’s doing, this time we need to find the ip of the attacker, and as we seen on the first challenge the attacker has persistence access (ssh) to the machine so i decided to check the /var/log/ which is the directory that keeps logs in a linux system inside of it i found multiple files or logs
as we can see not all logs contain data, but the messages file is the most interesting one which contain a variety of messages, such as mail, kern, and ofcourse auth which will give us login attempts via ssh, and remember Matt Johnson never logged in remotely, so i went ahead and grep’d ssh
```
cat messages | grep ssh
```
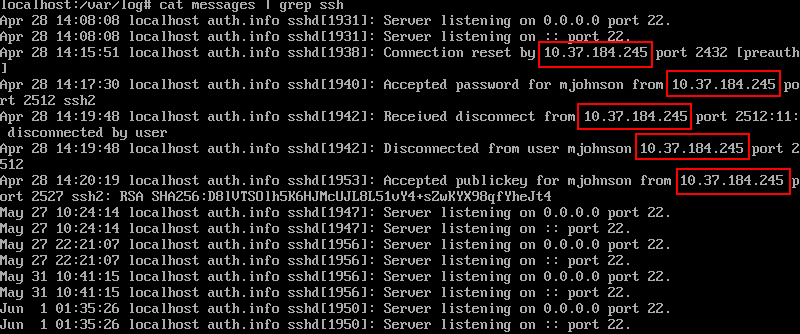
which gave us some ssh activities with the remote ip address of the attacker
## Flag: `byuctf{10.37.184.245}`