Tags: rev
Rating:
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/SEETF_CTF_2022/#best-software) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/SEETF_CTF_2022#best-software) out
This time we need to help out our man Gelos to get the License key for the Best Software around. So at first glance we saw that we got an .exe file so we run "file" on it to see what it is exactly:
```console
└─$ file BestSoftware.exe
BestSoftware.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows
```
Hah a good old .Net executable (ー ー;). Cause we did not have a Windows system around we needed to setup our Linux distro first to work on this. So we need:
- [ ] A way to execute the binary
- [ ] Inspect the PE
- [ ] Get the Flag
So the easiest way probably would be to spin up windows for it but we found the following solutions for each problem:
- [x] A way to execute the binary -> install mono for it. We used the mono-complete based on the description to ensure that everything works [mono](https://www.mono-project.com/download/stable/)
- [x] Inspect the PE -> We found a neat github project to bring ILSpy to Linux. Worked flawlessly [AvaloniaILSpy](https://github.com/icsharpcode/AvaloniaILSpy)
- [ ] Get the Flag -> thats the next part
Okay so we had our setup so lets have a look into the file with ILSpy.
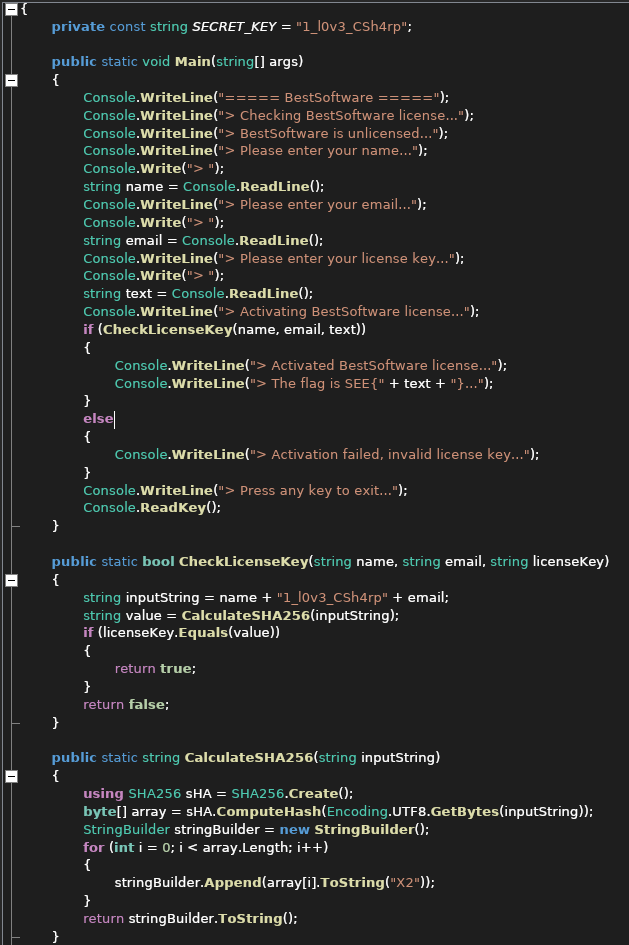
Now we can see that the program is not too much of a hassle to go trough. In the main function we can see that we get asked the name and email we got from the challenge description and the searched license key. After that the Function CheckLicenseKey which takes our input and checks if the SHA256 of our name + "1_l0v3_CSh4rp" + email matches the one we used as a license key. With that knowledge we just need to create the SHA256 hash like in the function CalculateSHA256 and we get our flag. (Actually the flag is just the Licensekey so we do not actually run the program).
For that we just copied all the code we have into an online .Net compiler and instead of the check of the key we just write it out and voila. We called it the Keygenerator for the Best Software:
Disclaimer: Never execute to something you don't know. So maybe not the best habit to have. But what could possible go wrong?
```csharp
using System;
using System.Security.Cryptography;
using System.Text;
internal class Program
{
private const string SECRET_KEY = "1_l0v3_CSh4rp";
public static void Main()
{
Console.WriteLine("===== BestSoftware Keygenerator =====");
Console.WriteLine("> Checking if you are from the police");
Console.WriteLine("> (ㆁᴗㆁ✿)");
Console.WriteLine("> (✿ㆁᴗㆁ)");
Console.WriteLine("> Please enter your name...");
Console.Write("> ");
string name = Console.ReadLine();
Console.WriteLine("> Please enter your email...");
Console.Write("> ");
string email = Console.ReadLine();
Console.WriteLine("> Creating BestSoftware license...");
string inputString = name + "1_l0v3_CSh4rp" + email;
string value = CalculateSHA256(inputString);
Console.WriteLine("> The key is " + value + " now go go");
Console.WriteLine("> Press any key to run...");
Console.ReadKey();
}
public static string CalculateSHA256(string inputString)
{
using SHA256 sHA = SHA256.Create();
byte[] array = sHA.ComputeHash(Encoding.UTF8.GetBytes(inputString));
StringBuilder stringBuilder = new StringBuilder();
for (int i = 0; i < array.Length; i++)
{
stringBuilder.Append(array[i].ToString("X2"));
}
return stringBuilder.ToString();
}
}
```
Sure, every great software should have also a great [Keygenerator](https://dotnetfiddle.net/rNaB1H). So with the given name and email the Flag is: SEE{28F313A48C1282DF95E07BCEF466D19517587BCAB4F7A78532FA54AC6708444E} . Again I think the reverse challenges are done by us not the way they should be.
- [x] Get the Flag
we did it ヾ(๑ ³ㅿ³)ノ onto the next one