Tags: decompile morse
Rating:
# Trash Royale
## Problem Statement:
Find the flag, and make sure its wrapped in LITCTF{}
Ugh, I keep forgetting my password for https://spectacle-deprive4-launder.herokuapp.com/, so I will just it here (sic).
Username: LexMACS and Password: !codetigerORZ
## Solution
Open the website, and you'll see a login page. At first, we expirmented with different login/password combos (basic SQL injection techniques) to try and break the login page but nothing worked. We moved on to logging in with the provided username and password.
Upon navigating to home, you are presented with the following page:
The first thing we saw was the morse code at the top. Clicking it, we got HEHEHEHAW. Not useful.
The webpage was unremarkable, except for the line which read `For a special few, our web developers have made the game available in early access!`. This made us search for the early access game.
Viewing the page source, one finds a hidden link:
Navigating to that url, we see a screen with an exe and an image. The image was useless (according to basic steganography). We also saw a warning that the sounds were buggy, pointing us towards finding sound files, mp3 and wav files.
We downloaded the executable. When we searched for strings in the executable, we found a string called "flag.mp3". This matched up with our observation above, and we started searching for ways to get the mp3 out of the executable. When we ran the executable, the top left icon displayed a snake:
This snake was clearly the pygame logo, indicating that the executable was compiled with pyinstaller with the --onefile flag. So, we used [pyinstxtractor](https://raw.githubusercontent.com/extremecoders-re/pyinstxtractor/master/pyinstxtractor.py) to extract the contents of the executable. Once extracted, we `cd`ed into the trash-royal.exe_extracted folder: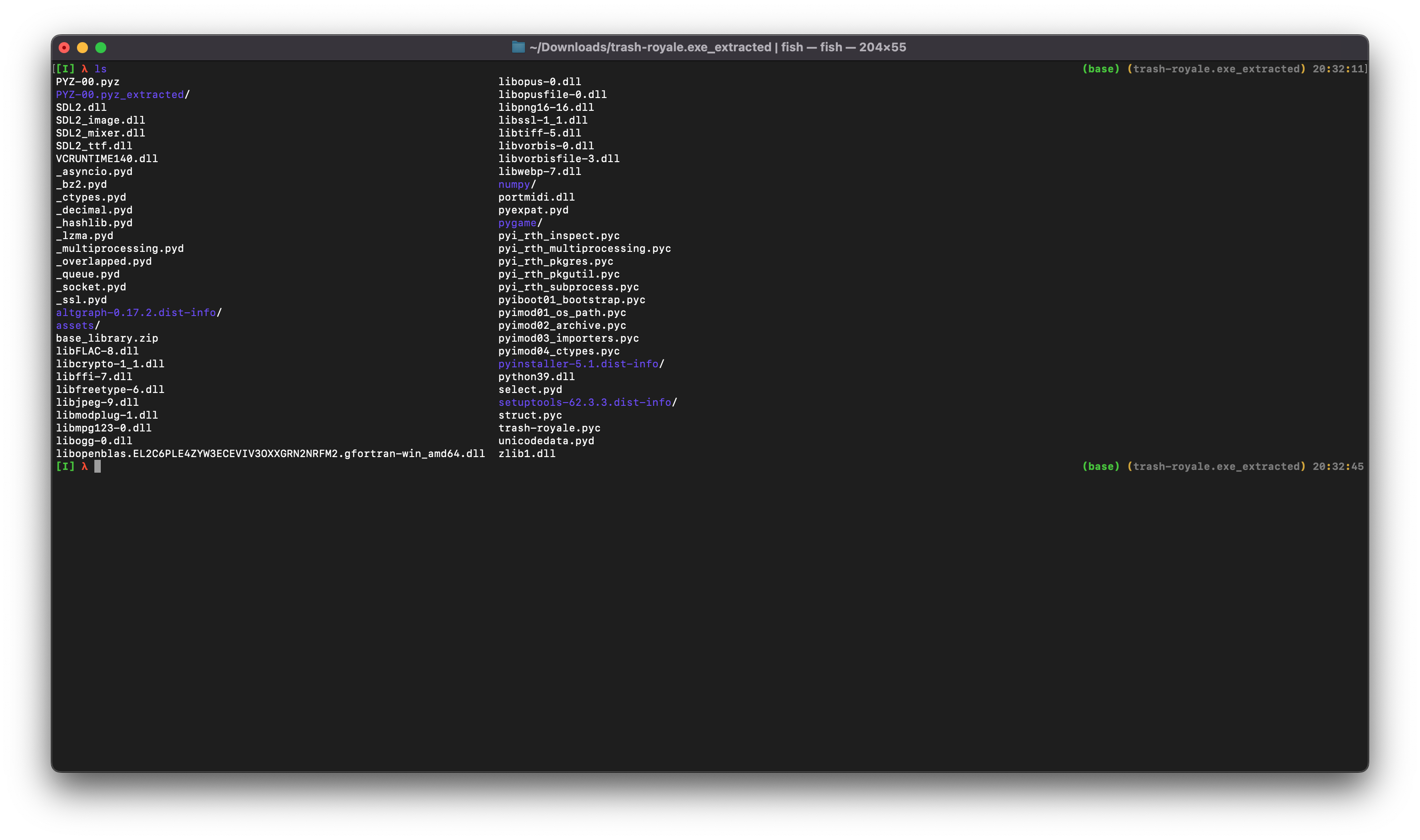
Music files are typically stored in `/assets` so we checked the folder, and found `flag.mp3`
Playing the mp3 file gives the user a bunch of hes and haws, indicating morse code. Given that he was shorter than haw, we let he represent `.` and haw represent `_`.
In order to easily see dots vs dashes, we opened the file in audacity.
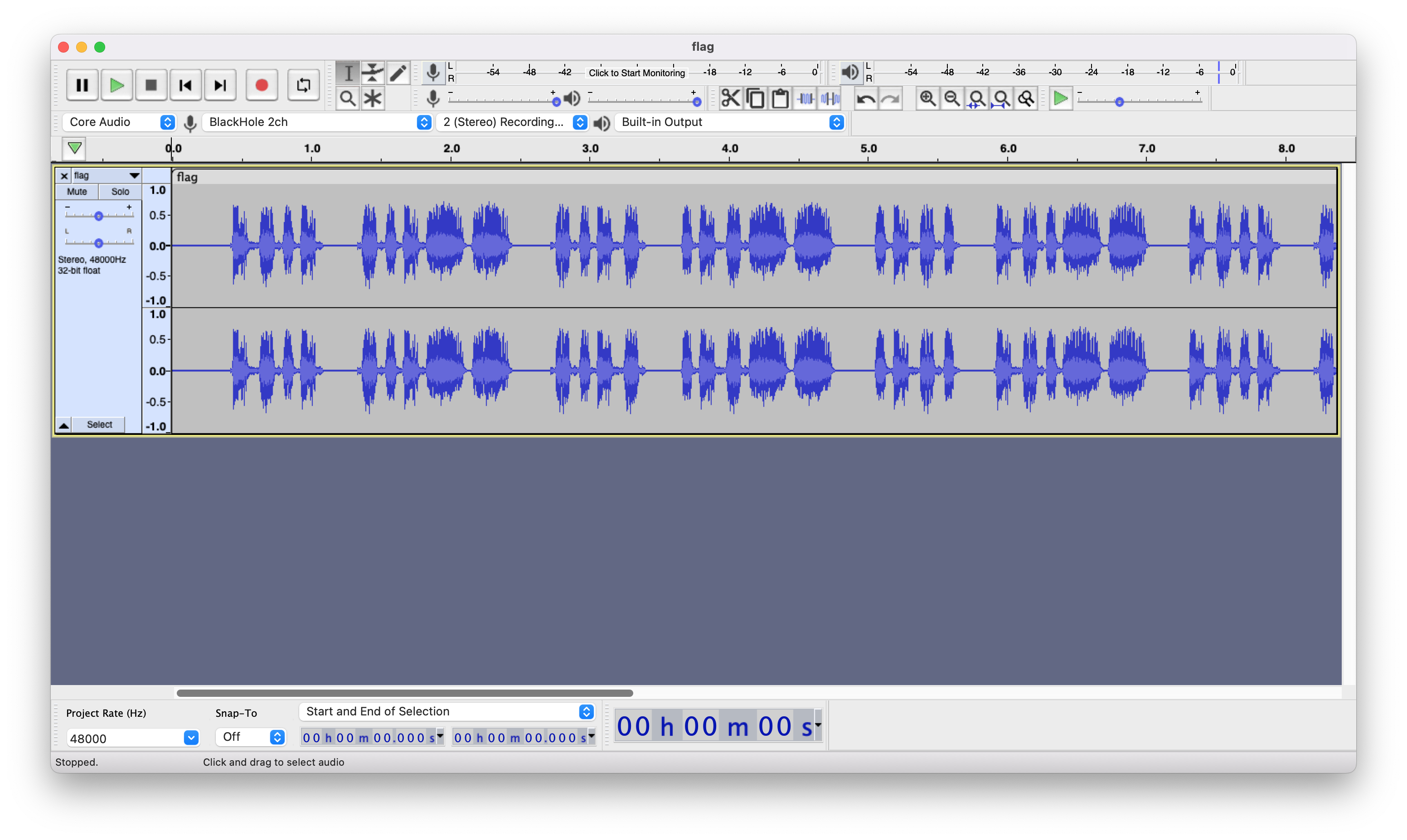
The morse code was `.... ...-- .... ...-- .... ...-- .... ....- .-- - .... .-. . . -.-. .-. --- .-- -.`
Translating this to english gave `H3H3H3H4WTHREECROWN`.
## Answer
`LITCTF{H3H3H3H4WTHREECROWN}`