Tags: protocol decode signal decoding
Rating:
# sqUARe paymenT terminal
The challenges contains a Terminal_Cap.sal file. This file is a capture of an asynchronous serial communication. The uppercase letters "UAR" are actually a hint to
the UART protocol that stands for "Universal Asynchronous Receiver/Transmitter".
*Not needed for the challenge. Unpacking the file gives us 8 binary files numbered from 0 - 7. This file actually contains communication. The number at the end of each
file stands for a channel. So channel 0-7. For this challenge only the channel 0 was used.*
Now looking for software to analyse the file I found [Logic 2](https://www.saleae.com/downloads/) from salae. There might be other tools as well.
Opening the capture in the software it shows as 7 channels while only the channel 0 had some communication in the capture. With the software we can then setup an analyser
in this case Async Serial. As for the settings most of them were default settings. Only the bitrate had to be changed. To get the bitrate right we need to
measure the fastest bits. In our case it is 38.4 kHz which is 38400 bits per second.
Check for further details the documentation on salaes website.
- [Using Async Serial(Analyzer)](https://support.saleae.com/protocol-analyzers/analyzer-user-guides/using-async-serial)
- [Decoding UART](https://support.saleae.com/protocol-analyzers/analyzer-user-guides/using-async-serial/decode-uart)
After adding an asynchronous analyser
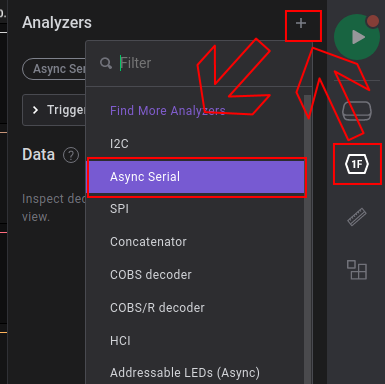
and setting up our analyser with 38400 bits/s

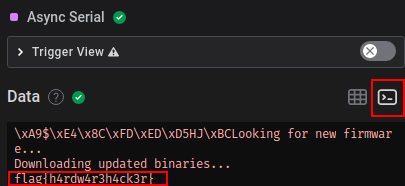
we can see in our data table view hex data and have no framing errors (Happens due to wrong settings like bitrate etc.).

Now we could export the data and decode the hex data ourselves. But luckily the tool contains a terminal view which already decodes it for us and gives us the flag.