Rating:
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/VU_Cyberthon_2023/#what-is-sha1-checksum-of-image-file-blk0_mmcblk0bin) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/VU_Cyberthon_2023#what-is-sha1-checksum-of-image-file-blk0_mmcblk0bin) out
By now the image file was on our system, which means we could start the first question. There are lots and lots of ways to solve this question but we just used the tools we already have on the Flare VM, which in our case was [hashmyfiles](https://www.nirsoft.net/utils/hash_my_files.html). It took a bit but the result was as expected with all the hashes you could ask:
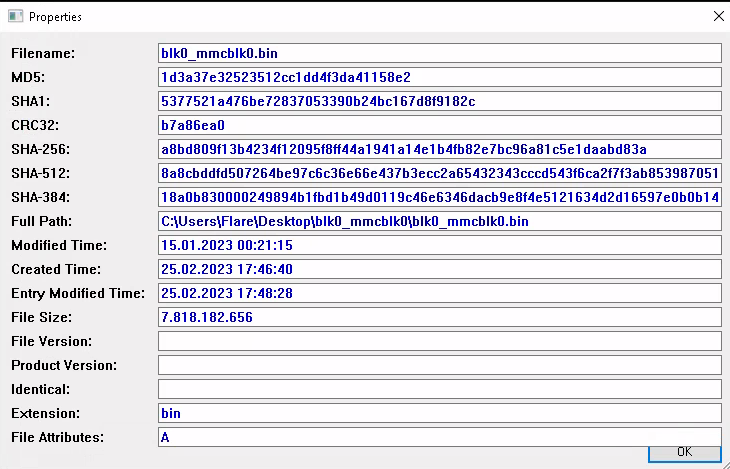
As you can see the SHA1 hash is **5377521a476be72837053390b24bc167d8f9182c**
Little nice start to any investigation to ensure you have an unmodified file and nothing broke during the transmission.