Tags: web hackday 2fa
Rating:
# Advocating-for-2FA
----------------------------------------------------------
## [1] Analyze the target :
we will start from this url https://oup0leb6eit.hackday.fr, it will show coming soon page
if we go to robots.txt file , it will show the path of the sitemap as shown in the photo :

so we will visit the sitemap.xml , note that the path was http://localhost:8080/sitemap.xml
don't worry we will not perform any kind of ssrf or lfi here , sitemap.txt will open directly

as shown in the photo , the sitemap.txt file contain two pages rather that the home , login and register
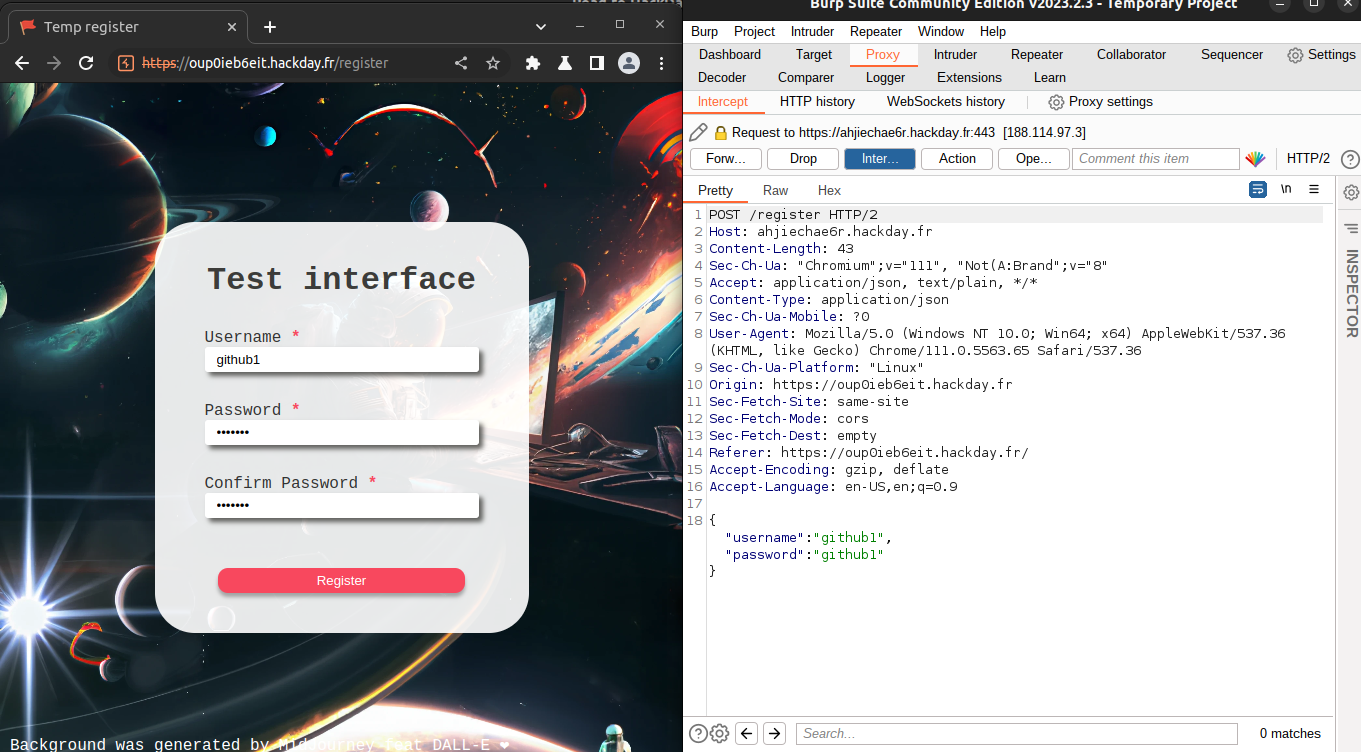
we will go to the registration page to register a new user

as shown in the photo and like any registration panel , we have to provide a username , password and confirm that password
I will use github1 for the username and the password as shown below
everything is ok untill now
## [2] 2FA and it's bypass :
so when we confirm our login it will require a 2FA code , but how we can get the code ?
as shown below the challenge provide you a way to generate new 2FA instance

everything is beautiful , let's create the instance and complete
when we create the instance it will show a QR code as the photo below

note that there many famous applications to use it for this kind of authentication , I will use google authenticator
but why not to see what the QR contains , so let's use a decoder
as shown below when I decode it online

we can notice this string **otpauth://totp/Web%20Challenge%20-%20Authentification%20%28github1%29?secret=GVSDINBYMQZWKOLDHFTGIMJWMNQWKMTEHBSTGNBWGVRDOOJRGBSA&issuer=Hackday**
so we can see **github1** user clearly , but what is that secret ??
if we put it's value on https://gchq.github.io/CyberChef we will notice that the value is base32 decoded

but what is the output ??
the first impression was MD5 , so I have tried to crack it , but no results , so what ? stop ? of course no
then I have tried to do hash the username as MD5
so why not to do the MD5 again ?
BOOOOOOM!!!!!!
so that is the secret : BASE32(MD5(MD5(USERNAME)))
but wait a minute , what username would we choose ?
admin , Admin , ADMIN , besthacker ???
let's take a step to the back , if we will go to the main page we will found this JavaScript file https://oup0ieb6eit.hackday.fr/js/app.c323a17d.js
I have captured the most important part of it
```javascript
function Ce(e, a, t, s, o, i) {
return (0, r.wg)(), (0, r.iD)("div", ye, [(0, r._)("div", Ae, [o.message ? ((0, r.wg)(), (0, r.iD)("div", Fe, (0, v.zw)(o.message), 1)) : (0, r.kq)("", !0), (0, r._)("h1", null, "Welcome " + (0, v.zw)(o.username), 1), (0, r._)("button", {
id: "logout-btn",
onClick: a[0] || (a[0] = (0, n.iM)(((...e) => i.logOut && i.logOut(...e)), ["prevent"]))
}, "Logout"), "admin" === o.username ? ((0, r.wg)(), (0, r.iD)("h3", Le, [(0, r.Uk)(" Congratulations !!! You found the flag ;) ... "), (0, r._)("img", {
src: o.flag,
alt: "IMG error",
style: {
display: "none"
}
}, null, 8, Se)])) : (0, r.kq)("", !0)]), Ue])
}
```
so now we know that we must use **admin** username , but what is the e.token ?
Do't worry we will deal with it later
returning to the QR code it self we can do this equation on **admin** username BASE32(MD5(MD5(admin))) then put as secret value
so it will be like this
**otpauth://totp/Web%20Challenge%20-%20Authentification%20%28admin%29?secret=MMZTEOBUMQYGMOJUGYYDMZDFGFTGIMTBMYYTOMTBMJQTCNLCMYZQ=&issuer=Hackday**
after that we can use any online tool to generate a QR code from text .
once we generate the QR code we can scan it using google authenticator
So now we know how to get the admin OTP
## [3] JWT part
you can see that there is a header called **X-Access-Token** and it's value is JWT token generated for the user who logged in
if we copy it and try to modify it using jwt.io
we cannot just edit it and replace it by the new one , we need to find the secret of the JWT
but how ? to understand how jwt works and what is the vulnerabilities associated with you can check this link https://portswigger.net/web-security/jwt
I will crack it using hashcat
```hashcat jwt.txt -m 16500 ```
then ????
let's return to 2FA , we will put the token of the user we want and his otp

then we will see flag page :

the flag page will connect /getinfo endpoint in this api https://ahjiechae6r.hackday.fr
if the token was the admin token , then the flag page will return welcome admin and congrats , as shown

then it will redirect you to strange endpoint , if you decode it you will get the flag

Thanks for reading my writeup , it was amazing question , but everybody was bruteforcing :)