Tags: forensics persistence
Rating:
# Eternally Pwned: Persistence
> Author: dree_
> Description: I get that the attackers were in my PC, but how did they achieve persistence?
[MEMORY.DMP](https://drive.usercontent.google.com/download?id=19kx1J7rTkck3EswVd42ZiQUr2sBo-s2J&export=download)
The next forensics challenge is `Persistence`, that we have to investigate the dump of memory unknown profile
So we can use `strings` or another method to determine some profile informations like trying this examples:
> `$ strings MEMORY.DMP | grep "notepad"`
>
> `$ strings MEMORY.DMP | grep "microsoft"`
>
> `$ strings MEMORY.DMP | grep "windows"`
(a bit ridiculous, but helpful ?)
Note that we have already know this is a dump of windows, so we can retrieve the information of it with `Volatility 3`
```bash {title="windows.info"}
$ volatility3 -f MEMORY.DMP windows.info
Volatility 3 Framework 2.5.0
Progress: 100.00 PDB scanning finished
Variable Value
Kernel Base 0xf80001852000
DTB 0x187000
Symbols file:///home/nopedawn/volatility3/volatility3/symbols/windows/ntkrnlmp.pdb/3844DBB920174967BE7AA4A2C20430FA-2.json.xz
Is64Bit True
IsPAE False
layer_name 0 WindowsIntel32e
memory_layer 1 WindowsCrashDump64Layer
base_layer 2 FileLayer
KdDebuggerDataBlock 0xf80001a430a0
NTBuildLab 7601.17514.amd64fre.win7sp1_rtm.
CSDVersion 1
KdVersionBlock 0xf80001a43068
Major/Minor 15.7601
MachineType 34404
KeNumberProcessors 1
SystemTime 2024-03-09 12:05:40
NtSystemRoot C:\Windows
NtProductType NtProductServer
NtMajorVersion 6
NtMinorVersion 1
PE MajorOperatingSystemVersion 6
PE MinorOperatingSystemVersion 1
PE Machine 34404
PE TimeDateStamp Sat Nov 20 09:30:02 2010
```
See! It's a dump of windows, now we can retrieve the information of process are running
```bash {title="windows.pstree"}
$ volatility3 -f MEMORY.DMP windows.pstree
Volatility 3 Framework 2.5.0
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime
4 0 System 0xfa8018d8db30 71 497 N/A False 2024-03-09 11:47:48.000000 N/A
* 224 4 smss.exe 0xfa8019c06310 2 29 N/A False 2024-03-09 11:47:48.000000 N/A
296 288 csrss.exe 0xfa801a39a750 9 341 0 False 2024-03-09 11:47:49.000000 N/A
348 288 wininit.exe 0xfa801a3b8b30 4 77 0 False 2024-03-09 11:47:49.000000 N/A
* 468 348 lsm.exe 0xfa801a40eb30 11 144 0 False 2024-03-09 11:47:49.000000 N/A
* 460 348 lsass.exe 0xfa801a4083b0 8 569 0 False 2024-03-09 11:47:49.000000 N/A
* 444 348 services.exe 0xfa801a3ff5f0 9 200 0 False 2024-03-09 11:47:49.000000 N/A
** 640 444 svchost.exe 0xfa801a54bb30 9 243 0 False 2024-03-09 11:47:50.000000 N/A
** 1536 444 spoolsv.exe 0xfa801a93fb30 13 254 0 False 2024-03-09 11:56:05.000000 N/A
** 908 444 svchost.exe 0xfa801a5ccb30 8 197 0 False 2024-03-09 11:47:50.000000 N/A
*** 1304 908 dwm.exe 0xfa801a75a060 4 66 1 False 2024-03-09 11:47:51.000000 N/A
** 1040 444 svchost.exe 0xfa801a6d0060 4 46 0 False 2024-03-09 11:47:51.000000 N/A
** 2040 444 mscorsvw.exe 0xfa801a85db30 8 84 0 True 2024-03-09 11:49:52.000000 N/A
** 1956 444 sppsvc.exe 0xfa801a87f4f0 5 151 0 False 2024-03-09 11:47:59.000000 N/A
** 812 444 svchost.exe 0xfa801a5a49e0 34 953 0 False 2024-03-09 11:47:50.000000 N/A
** 1200 444 taskhost.exe 0xfa801a722b30 6 117 1 False 2024-03-09 11:47:51.000000 N/A
** 692 444 svchost.exe 0xfa801a5645f0 14 288 0 False 2024-03-09 11:47:50.000000 N/A
** 948 444 svchost.exe 0xfa801a5dc5f0 17 441 0 False 2024-03-09 11:47:50.000000 N/A
** 1332 444 mscorsvw.exe 0xfa801a705060 8 75 0 False 2024-03-09 11:49:52.000000 N/A
** 312 444 spoolsv.exe 0xfa801a6a6670 0 - 0 False 2024-03-09 11:47:51.000000 2024-03-09 11:55:05.000000
** 1852 444 msdtc.exe 0xfa8018e3e620 13 142 0 False 2024-03-09 11:49:53.000000 N/A
** 576 444 svchost.exe 0xfa801a521b30 12 348 0 False 2024-03-09 11:47:50.000000 N/A
*** 1848 576 WmiPrvSE.exe 0xfa801a500a10 7 118 0 False 2024-03-09 12:04:55.000000 N/A
*** 2052 576 WmiPrvSE.exe 0xfa801990fb30 9 248 0 False 2024-03-09 12:04:56.000000 N/A
** 1992 444 svchost.exe 0xfa801a46c220 6 67 0 False 2024-03-09 11:49:53.000000 N/A
** 860 444 svchost.exe 0xfa801a5c05a0 11 273 0 False 2024-03-09 11:47:50.000000 N/A
** 1380 444 svchost.exe 0xfa801a78e730 6 99 0 False 2024-03-09 11:47:52.000000 N/A
** 240 444 svchost.exe 0xfa801a41d060 18 295 0 False 2024-03-09 11:47:50.000000 N/A
** 2168 444 TrustedInstall 0xfa801a4fab30 7 223 0 False 2024-03-09 12:04:57.000000 N/A
360 340 csrss.exe 0xfa801a3bf060 7 266 1 False 2024-03-09 11:47:49.000000 N/A
* 988 360 conhost.exe 0xfa801a85e1d0 2 38 1 False 2024-03-09 11:49:15.000000 N/A
* 1868 360 conhost.exe 0xfa801a4a8630 2 38 1 False 2024-03-09 11:50:05.000000 N/A
408 340 winlogon.exe 0xfa801a3f75c0 4 97 1 False 2024-03-09 11:47:49.000000 N/A
1320 1292 explorer.exe 0xfa801a7637c0 30 712 1 False 2024-03-09 11:47:52.000000 N/A
* 896 1320 multireader.ex 0xfa801a8601d0 2 57 1 False 2024-03-09 11:54:50.000000 N/A
* 804 1320 cmd.exe 0xfa801a496450 1 21 1 False 2024-03-09 11:50:05.000000 N/A
* 1644 1320 notepad.exe 0xfa801a4ba060 1 57 1 False 2024-03-09 11:52:04.000000 N/A
* 1804 1320 cGFzdGViaW4uY2 0xfa801a8de800 8 258 1 False 2024-03-09 11:54:49.000000 N/A
* 1680 1320 cmd.exe 0xfa801a862060 1 19 1 False 2024-03-09 11:49:15.000000 N/A
* 1272 1320 iexplore.exe 0xfa801a983b30 11 381 1 True 2024-03-09 11:55:44.000000 N/A
** 1284 1272 iexplore.exe 0xfa801a503b30 16 348 1 True 2024-03-09 11:55:45.000000 N/A
2568 2492 taskmgr.exe 0xfa801ac2db30 7 124 1 False 2024-03-09 12:05:33.000000 N/A
```
I see there is a strange process running on `PID: 1804`, look like base64 `cGFzdGViaW4uY2`
```bash
$ echo "cGFzdGViaW4uY2" | base64 -d
pastebin.c
```
Hmm, A pastebin running on windows? What about the command-line dump history?
```bash
$ volatility3 -f MEMORY.DMP windows.cmdline
Volatility 3 Framework 2.5.0
Progress: 100.00 PDB scanning finished
PID Process Args
4 System Required memory at 0x20 is not valid (process exited?)
224 smss.exe \SystemRoot\System32\smss.exe
296 csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16
348 wininit.exe wininit.exe
360 csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16
408 winlogon.exe winlogon.exe
444 services.exe C:\Windows\system32\services.exe
460 lsass.exe C:\Windows\system32\lsass.exe
468 lsm.exe C:\Windows\system32\lsm.exe
576 svchost.exe C:\Windows\system32\svchost.exe -k DcomLaunch
640 svchost.exe C:\Windows\system32\svchost.exe -k RPCSS
692 svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted
812 svchost.exe C:\Windows\system32\svchost.exe -k netsvcs
860 svchost.exe C:\Windows\system32\svchost.exe -k LocalService
908 svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted
948 svchost.exe C:\Windows\system32\svchost.exe -k NetworkService
240 svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork
312 spoolsv.exe Required memory at 0x7fffffdf020 is not valid (process exited?)
1040 svchost.exe C:\Windows\system32\svchost.exe -k regsvc
1200 taskhost.exe "taskhost.exe"
1304 dwm.exe "C:\Windows\system32\Dwm.exe"
1320 explorer.exe C:\Windows\Explorer.EXE
1380 svchost.exe C:\Windows\system32\svchost.exe -k NetworkServiceNetworkRestricted
1956 sppsvc.exe C:\Windows\system32\sppsvc.exe
1680 cmd.exe "C:\Windows\system32\cmd.exe"
988 conhost.exe \??\C:\Windows\system32\conhost.exe
2040 mscorsvw.exe C:\Windows\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe
1332 mscorsvw.exe C:\Windows\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe
1992 svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersonation
1852 msdtc.exe C:\Windows\System32\msdtc.exe
804 cmd.exe "C:\Windows\system32\cmd.exe"
1868 conhost.exe \??\C:\Windows\system32\conhost.exe
1644 notepad.exe "C:\Windows\system32\NOTEPAD.EXE" C:\Users\joe\Desktop\schedule.txt
1804 cGFzdGViaW4uY2 "C:\temp\cGFzdGViaW4uY29tL3lBYTFhS2l1.exe"
896 multireader.ex "C:\temp\multireader.exe"
1272 iexplore.exe "C:\Program Files (x86)\Internet Explorer\iexplore.exe"
1284 iexplore.exe "C:\Program Files (x86)\Internet Explorer\iexplore.exe" SCODEF:1272 CREDAT:71937
1536 spoolsv.exe C:\Windows\System32\spoolsv.exe
1848 WmiPrvSE.exe C:\Windows\system32\wbem\wmiprvse.exe
2052 WmiPrvSE.exe C:\Windows\system32\wbem\wmiprvse.exe
2168 TrustedInstall C:\Windows\servicing\TrustedInstaller.exe
2568 taskmgr.exe "C:\Windows\system32\taskmgr.exe" /1
```
Look athe process running `cGFzdGViaW4uY29tL3lBYTFhS2l1.exe`, decode it `cGFzdGViaW4uY29tL3lBYTFhS2l1`
```bash
$ echo "cGFzdGViaW4uY29tL3lBYTFhS2l1" | base64 -d
pastebin.com/yAa1aKiu
```
That's a pastebin link [https://pastebin.com/yAa1aKiu](https://pastebin.com/yAa1aKiu), and there's a flag on it
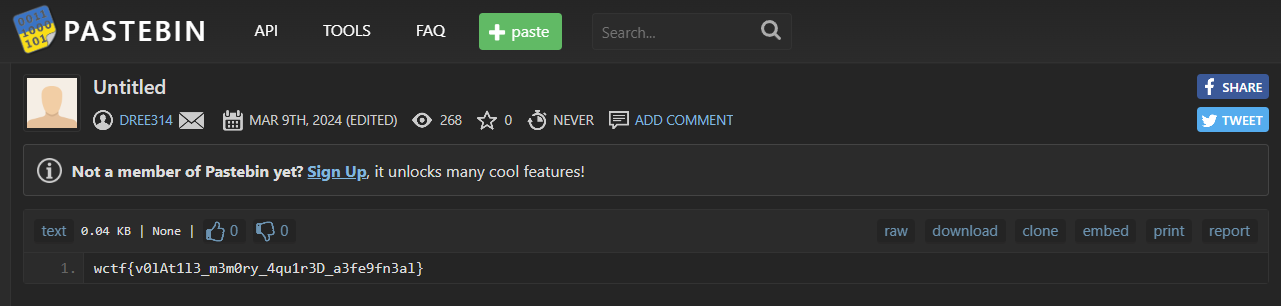
> Flag: `wctf{v0lAt1l3_m3m0ry_4qu1r3D_a3fe9fn3al}`