Tags: forensics
Rating:
> Hi there incident responder. So we have this company that was breached sometime last week, but their SOC team only keeps HTTP request logs ? We took down all of our wolvsecsolutions websites as a precaution.
>
> Maybe there’s still a way to figure out what happened? Why did they click on a suspicious link? Somebody told me there’s a flag on the link now?
We parse logs containing the keyword wolvsecsolutions. You can use an editor to do this. I used sublimetext. (Ctrl+L to get the selected keywords as a complete row)
[Link for sublimetext video](https://margheritaviola.com/2024/03/20/wolvctf-forensics-log-analysis-writeup/).
Here I delete frequently used hosts for example dev.wolvsecsolutions.
[Link for sublimetext video](https://margheritaviola.com/2024/03/20/wolvctf-forensics-log-analysis-writeup/).
One of the remaining hosts draws our attention.
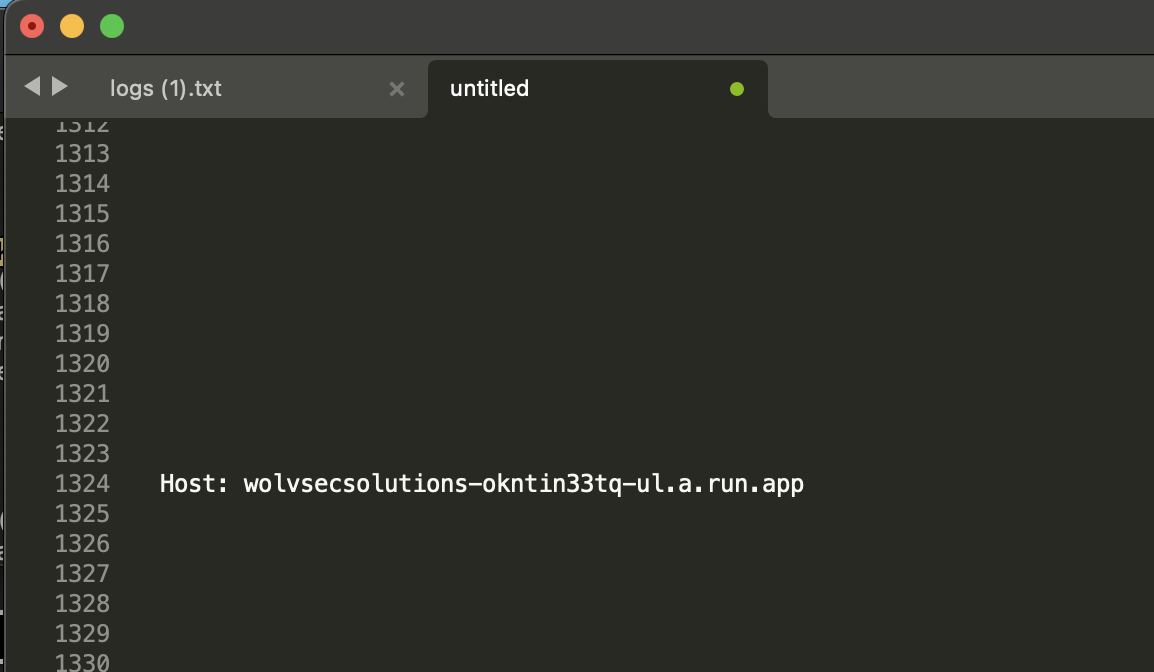
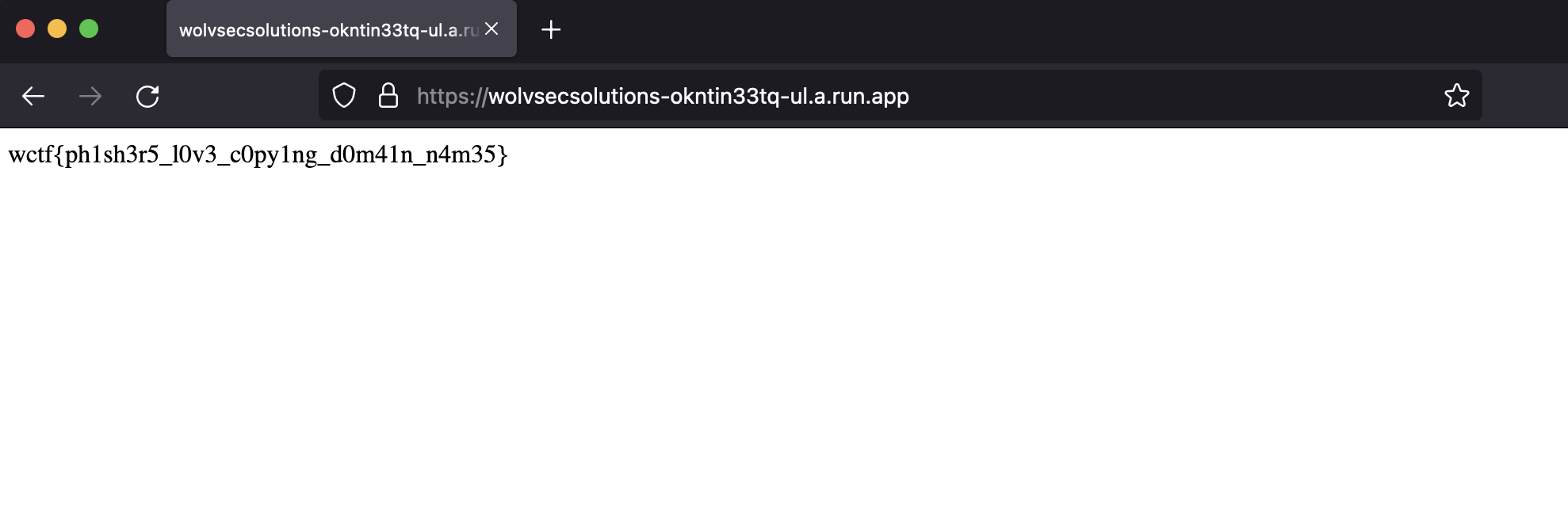
`wctf{ph1sh3r5_l0v3_c0py1ng_d0m41n_n4m35}`