Tags: forensics
Rating:
> I recently had my passwords and other sensitive data leaked, but I have no idea how. Can you figure out how the attacker got in to my PC?
The pcap file is opened in Wireshark and if we browse the packet in it, SMB packages attract attention and we select SMB as a filter in the first stage.
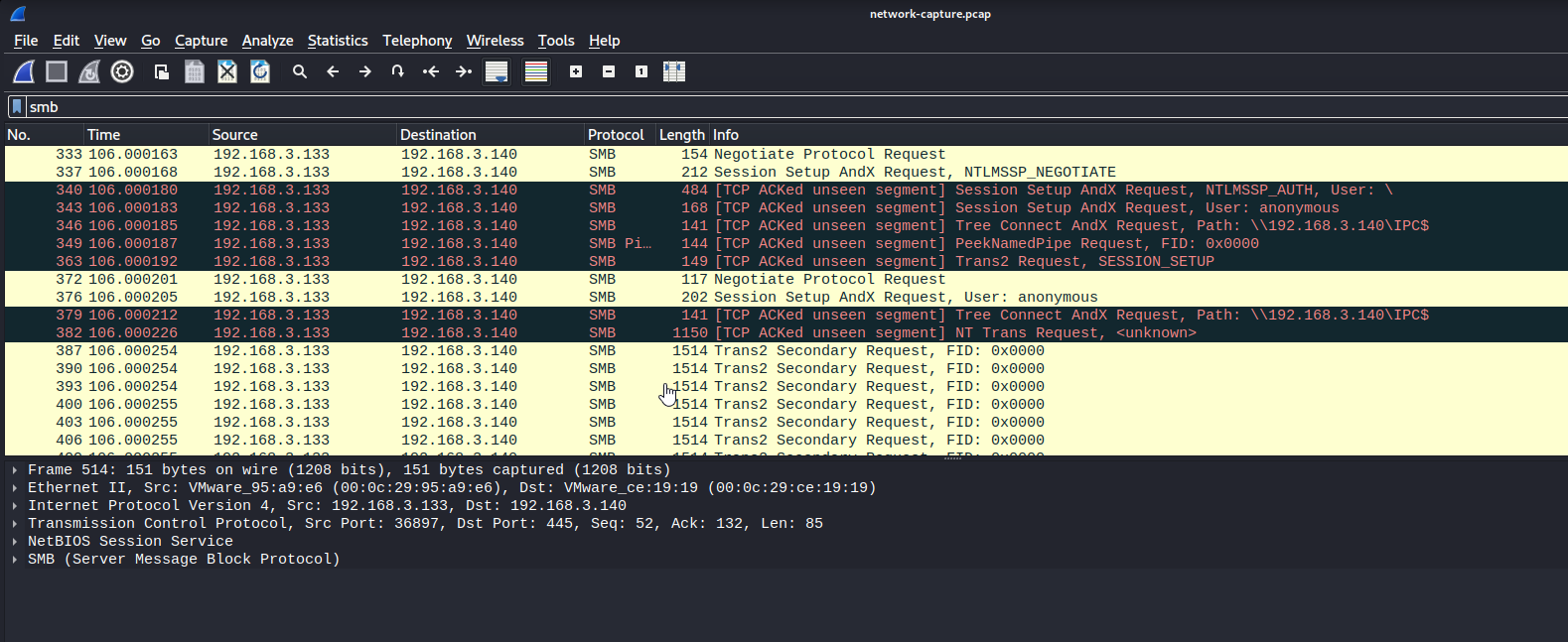,
If we look inside the SMB packages, we see frames where base64 decoders are available.
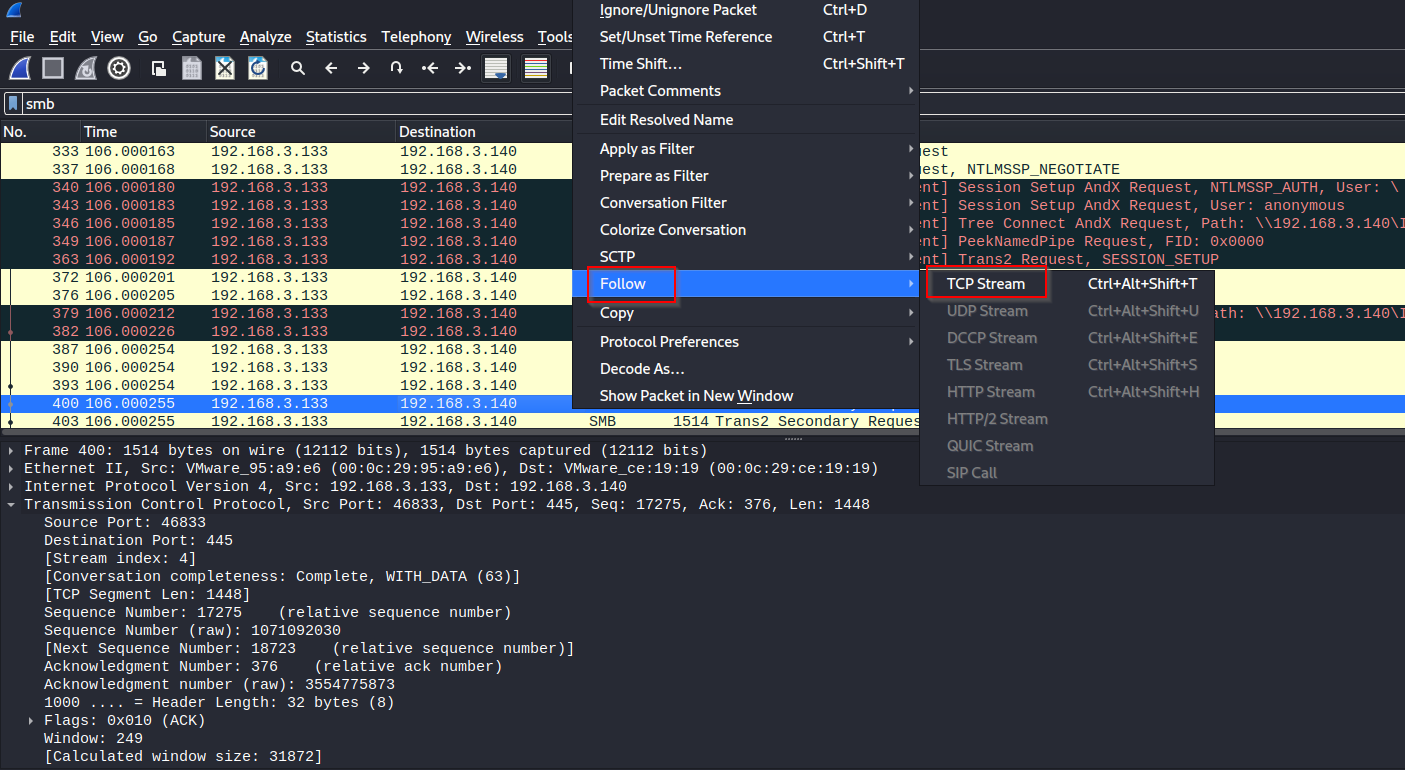
If we copy the TCP stream content and delete the redundancies, we get our base64 code.
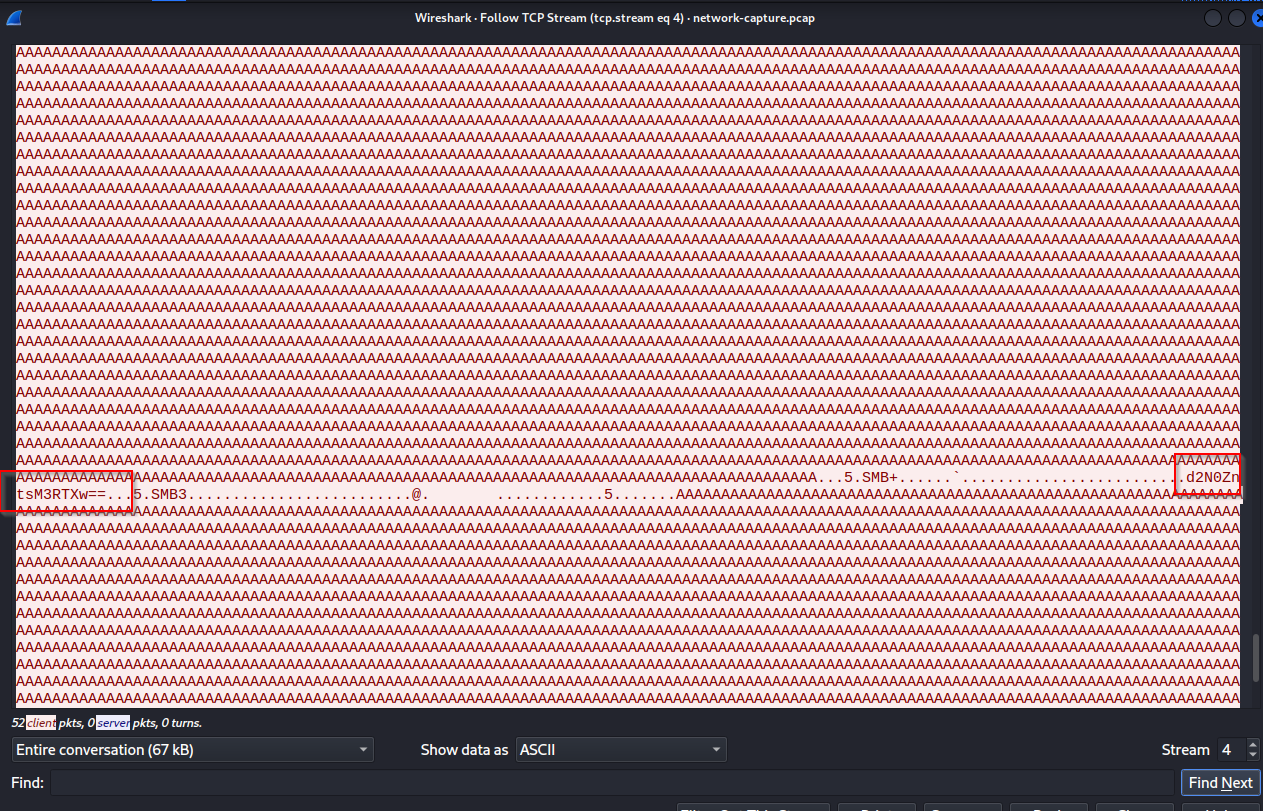
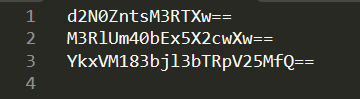
We get three base64 codes, decode them separately, and then combine them to get the flag.
```
wctf{l3tS_3teRn4lLy_g0_bLU3_7n9wm4iWnL}
```