Tags: forensics
Rating: 4.0
> I get that the attackers were in my PC, but how did they achieve persistence?
We use the OSForensics tool to do forensics in our.DMP file. The free version will do the job. We use the Hex/String Viewer feature to look at the detailed contents of the file and here we notice the base64 code.
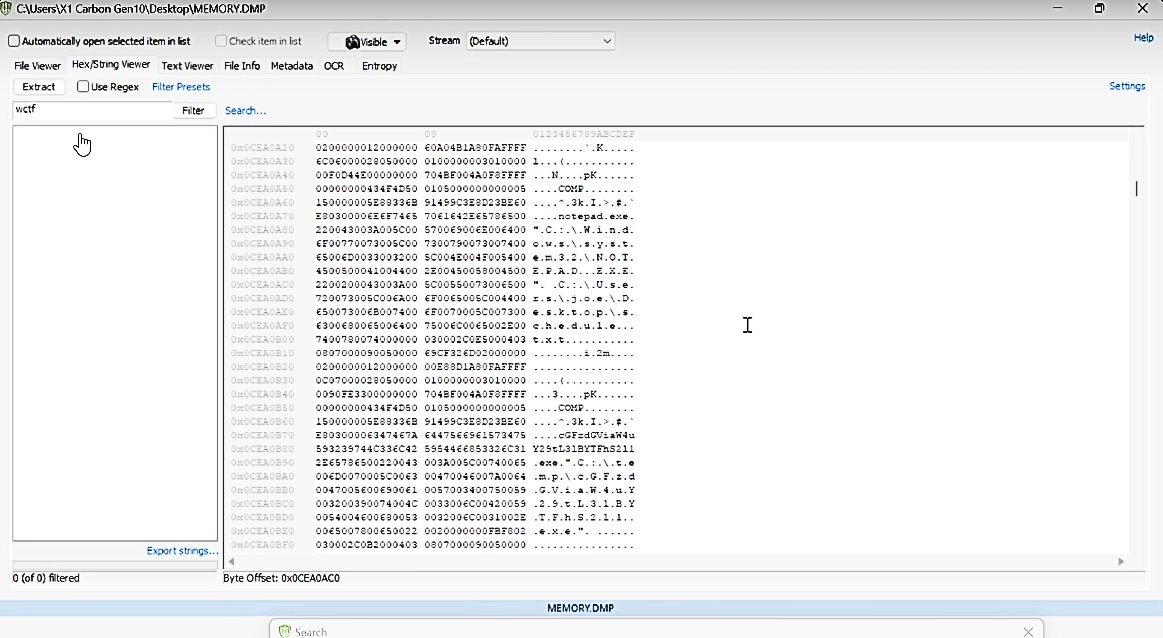
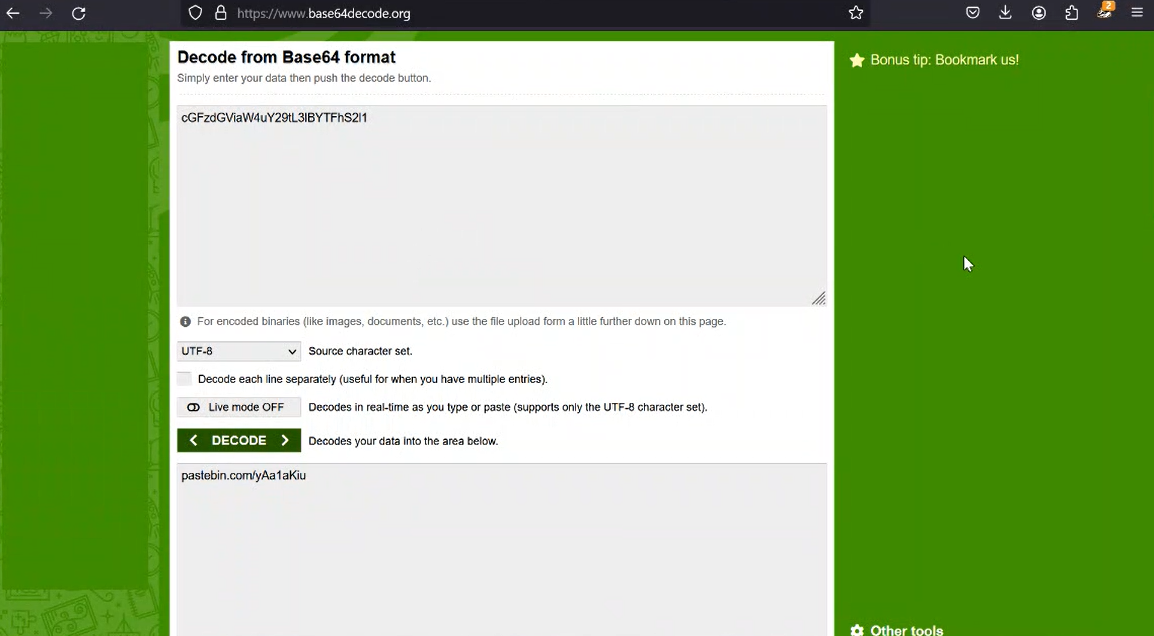
When we decode Base64, we get the Pastebin link and if we go to the link, we reach the flag.
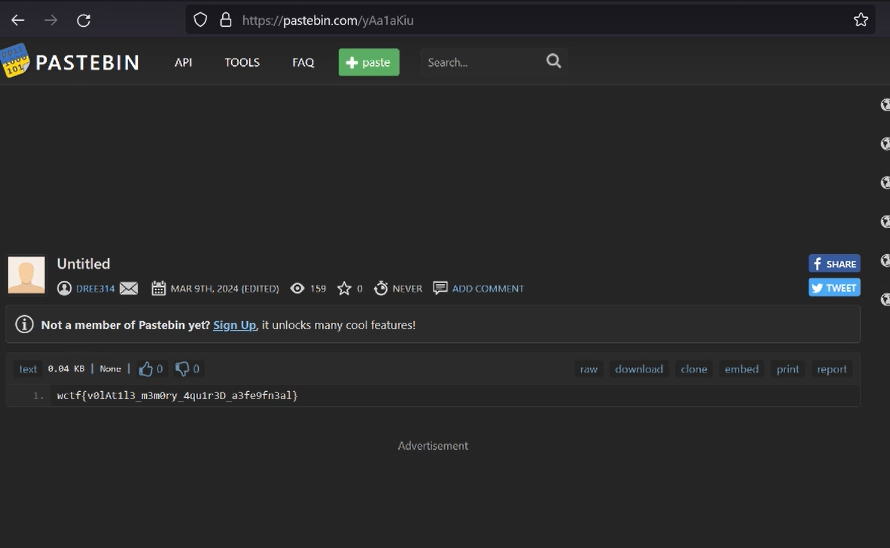
`wctf{v0lAt1l3_m3m0ry_4qu1r3D_a3fe9fn3al}`