Tags: ida debugging binaryninja reversing reverse_engineering tracing
Rating:
# Note:
Due to https://ctf.texsaw2024.com/ going down, I do not have the original file, but I have the (spoiler) demoved version which I uploaded to discord to display my progress.
# The crackme's background
\
In the past, I've seen Christopher Domas's work. I could tell from the challenge name it was going to be Christopher Domas related because of this awesome project he made: https://github.com/xoreaxeaxeax/REpsych. But I did not expect it to be movfuscated (pick a better name devs! Edit: after reading the official writeup I realized it was a hint, lol)\
For those who do not know, x86 mov is Turing complete. This means that, only using the mov instruction, you can remake any program. Christopher's role in this was making a mov compiler: https://github.com/xoreaxeaxeax/movfuscator
# Initial analysis
It only uses mov, and it's compiled for Linux. The flag is the amount of instructions executed + the hidden message. It takes no input (not via stdin, a file, or anything), and has a flat control flow (no comparisons, even when demovuscated).
# The first part of the flag
\
Thankfully, my teammate knew how to use perf.
# The second part
All info that is given is: it's a hidden message ;-;
### Demov
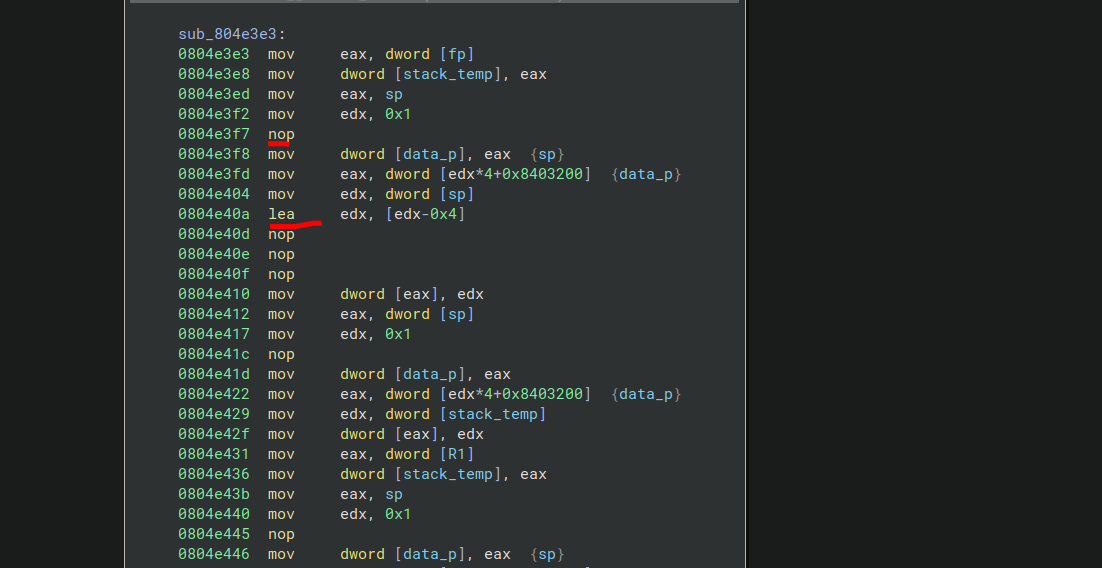
Demovfuscating was annoying, but doable. Long ago, I tried compiling demovuscator (https://github.com/leetonidas/demovfuscator), but failed. So, this time, I searched for a docker container instead, and found it: https://hub.docker.com/r/iyzyi/demovfuscator\
Does it have malware? Does it upload my binary to some random website? I don't know, but it works (kinda):
### Finding the hidden message
After A LOT of trial and error, I finally found out how to obtain the flag:
1. I dumped the decompilation:
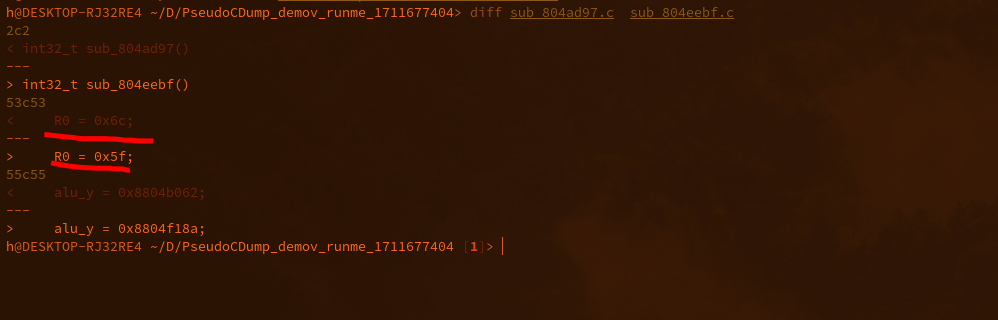
2. I ran a diff checker against the sub functions, the only difference is the written address, the function name, and most importantly: the value written (THOSE LOOK LIKE CHAR VALUES!):
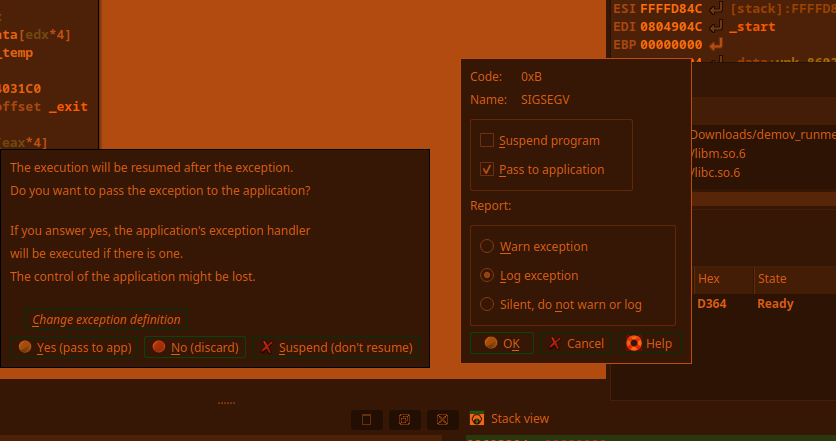
2.5. While debugging, make all exceptions pass to app (movfuscated binaries need exceptions in order to work):
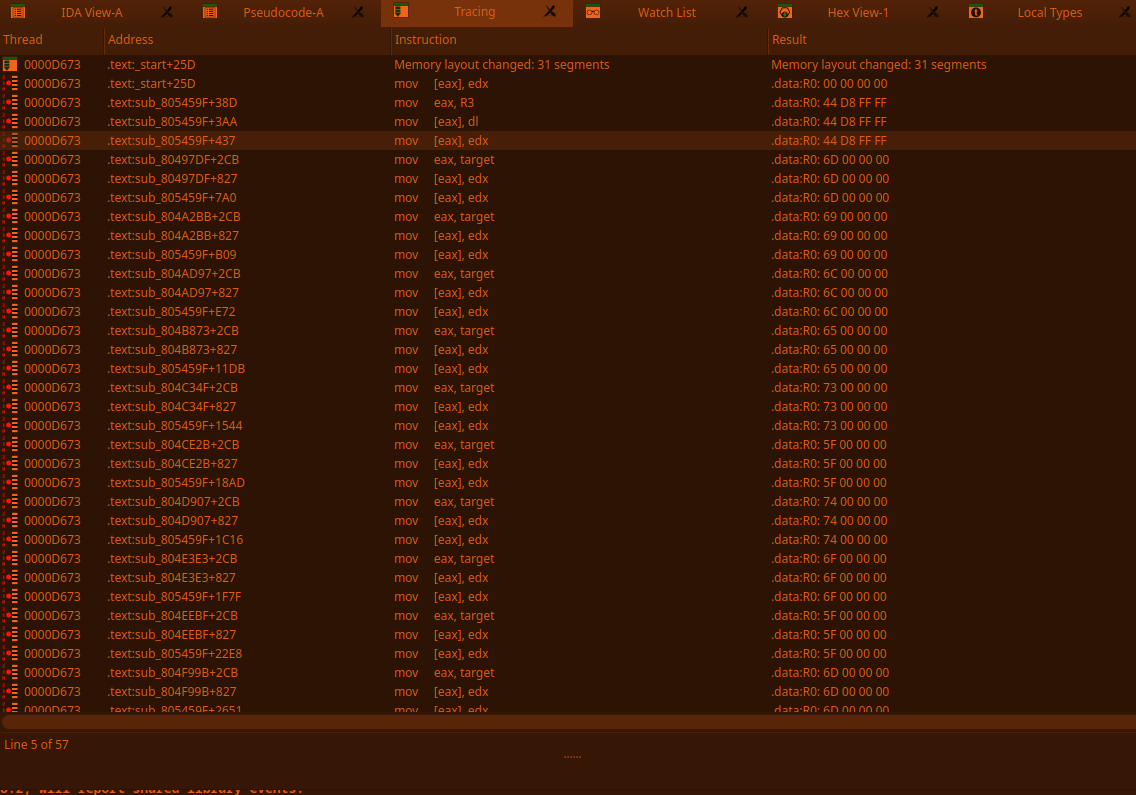
3. I traced the variable (R0) in IDA (yes I use IDA's debugger, fight me):
\
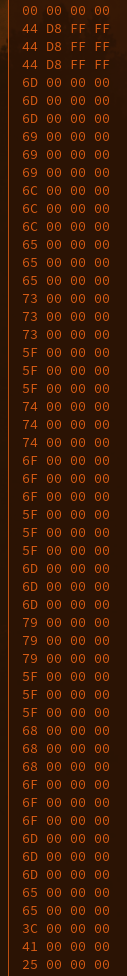
4. Copy all the hex values and use a vim macro to extract the hex values (I'm scared of regex):\
5. Use magical cyberchef (not to be confused with cyberchef's magic thing) for hex decoding:
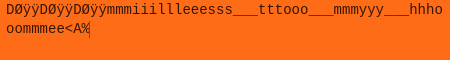
6. Based off of eyeballing, each char is repeated three times except e, and the stuff written at the beginning and the end appears to be junk:\

# All together
texsaw{387711_miles_to_my_home}
# Conclusion
I am yet to need to reverse engineer anything in quite a few reverse engineering challenges