Tags: crypto reverse
Rating:
## Crypt0r - Part 3 : Solution
I've finished it only a day after, though as far as I know, this is the first public solution available (at the time of writiing).
the challenge is to reverse a 64 bit ELF ransomware, specifically its encryption algorithm in order to decrypt a given file (the-file-to-decrypt.flag)
after finishing the prviouse steps, I had what looked like 2 early copies of the ransomware called crypt0r.jessie and crypt0r.wheezie.
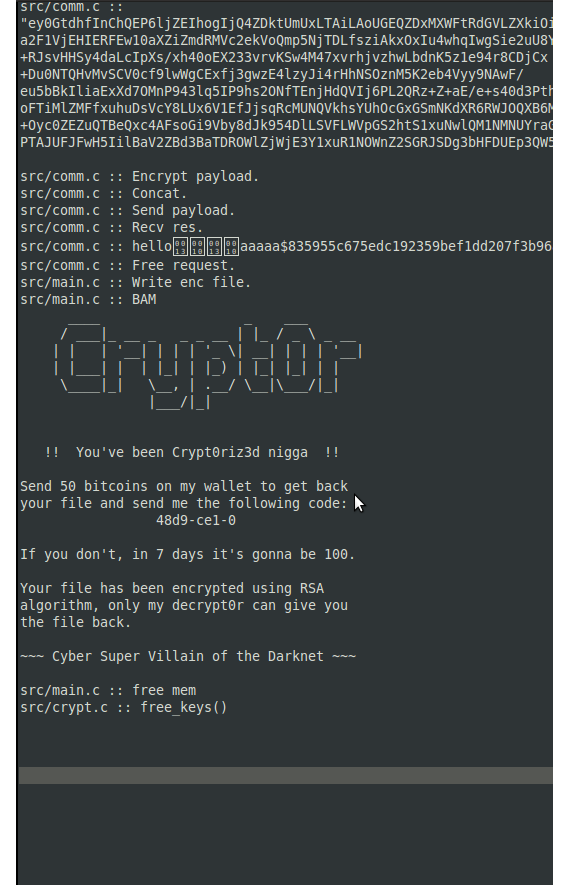
The ransomware looks for a file called 'crypt.me' to start encrypting.
and connects to a CnC server at address 137.74.26.184 port 1337, to send it the key.. I've rerouted the address to my small python server, though I'm not sure if it was necessary.
$ sudo iptables -t nat -A OUTPUT -p all -d 137.74.26.184 -j DNAT --to-destination 127.0.0.1
After reversing for a while (unfurtunatly a while longer than needed), I've identify that the encryption algo is RSA being initialized with openssl functions.. there i've noticed a line that broke gdb execution:
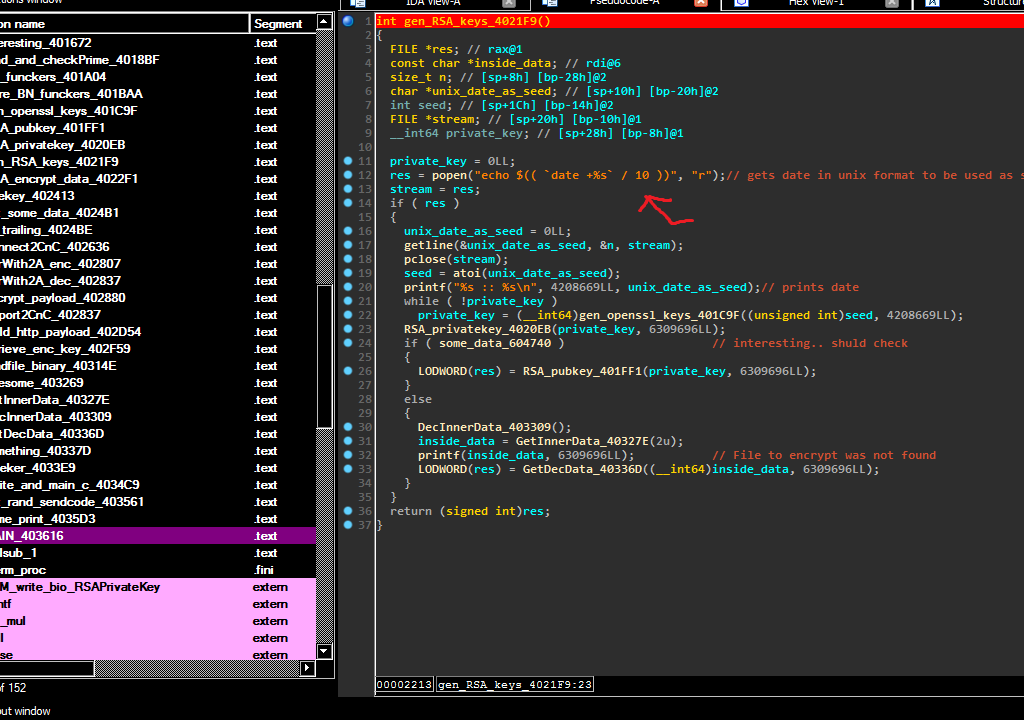
echo $(( `date +%s` /10 ))
Apart from that, the ransomware also saved the private.pem key after encrypting...
I didn't had much expirience with the inner workings of RSA, though after googling, I found that because it used srand/rand C functions, it should be possible to generate the same private key.. if I'll get the original seed.
For clues, I've checked the 'the-file-to-decrypt.flag' file to see the modification date (Mon 03 Apr 2017 05:14:18 PM GMT), then converted it to unix timestemp format : 1491239658,
after that, I've edited the binary :
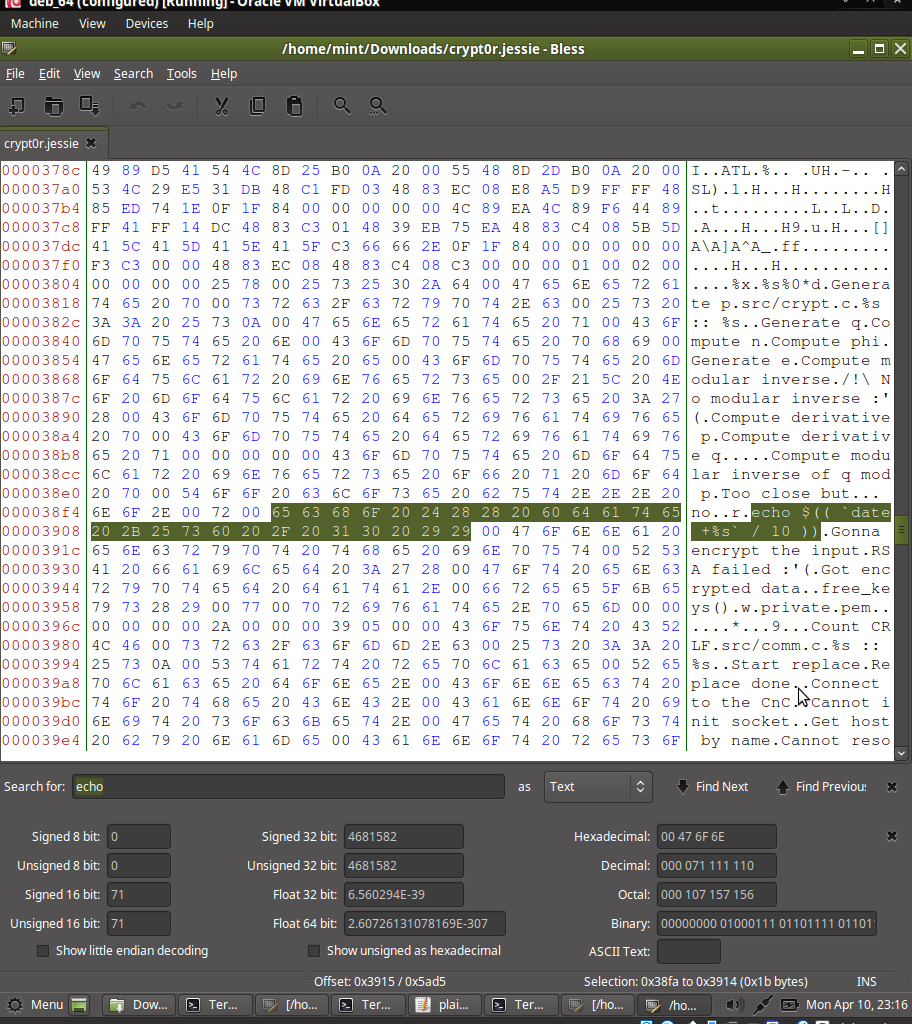
and changed the string "echo $(( `date +%s` /10 ))" to "echo $(( 1491239658 / 10 ))
Then executed crypt0r.jessie.. collected the stored private.pem, ran:
$ openssl rsautl -decrypt -in the-file-to-decrypt.flag -out result -inkey private.pem
and Bam.. there it was :
> Congratulations !
>
> You did decrypt this file. You really should consider joining OVH since we're
> looking at candidates just like you. However, here's your reward:
>
> INSA18c21e583eb590c14278068989349ac8
h45hm_nch.