Tags: dotcode forensics qrcode
Rating:
Find me!
[Download Link](https://github.com/jbzteam/CTF/blob/master/WhiteHatSummer2017/Hue/Hue.zip)
Extracting the archive we got the following:
```
ls
Hue.zip 'my collection' openme.zip
```
`my collection` is a directory and `openme` is a password-locked archive
The directory contains a lot of `png` files with flags of states and some pieces of QRCode, reconstructing it

scanning it with zbar gave us the password for the archive
```
zbarimg qrcode.jpg
QR-Code:=== Ea5y p4ssw0rd h4h4 ===
scanned 1 barcode symbols from 1 images in 0.15 seconds
```
extracting `openme.zip` with the password gave us the following:
```
[openme.zip] here.png password:
inflating: here.png
inflating: flag.txt
```
`flag.txt` is just a dummy and contains `It's not here ^^`
After some research on the png we found out is `DotCode`
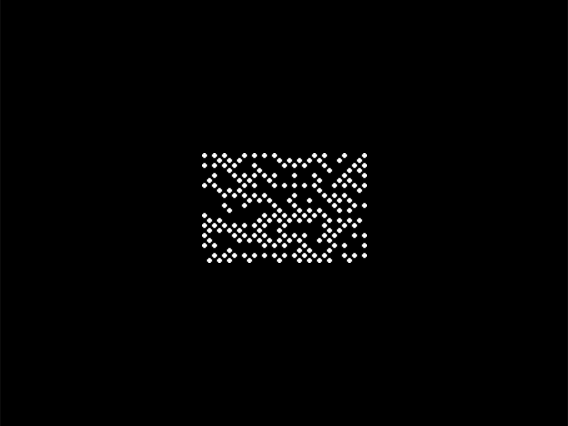
Scanning it with a DotCode Reader gave us:
`flag: d0tc0d3_s0_c00l`