Rating:
# Super Encryption!
**60 points**
```
My friend sent me a flag encrypted with an encryption program.
Unfortunately, the decryption doesn't seem to work.
Please help me decrypt this: dufhyuc>bi{{f0|;vwh<~b5p5thjq6goj}
```

The decryption is not implemented in the attached file (`superencrypt`) so the inverse of the encryption has to be handcrafted.
**The entrypoint(`main`) in IDA**
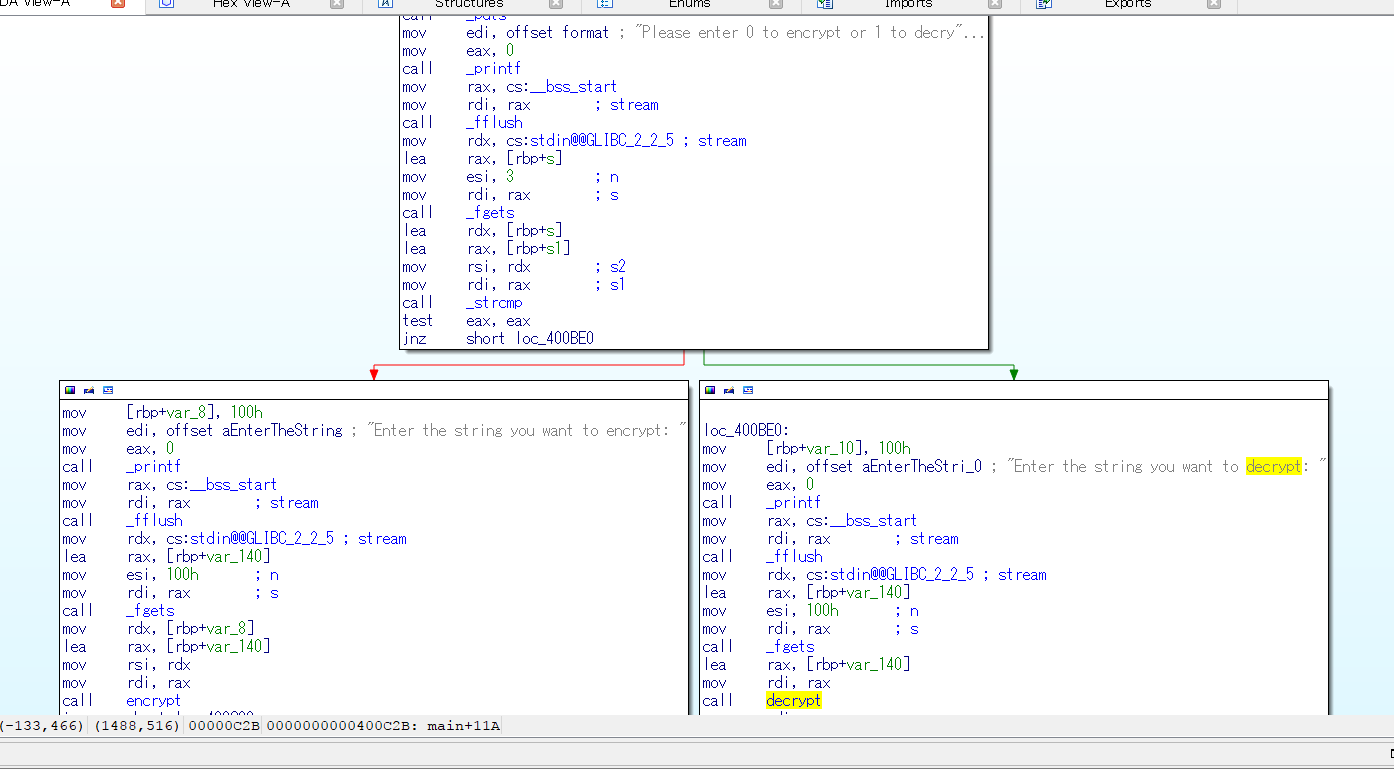
A very straight forward branch is made to `encrypt` and `decrypt` based on the user input.

As expected, nothing happens in the `decrypt` function.
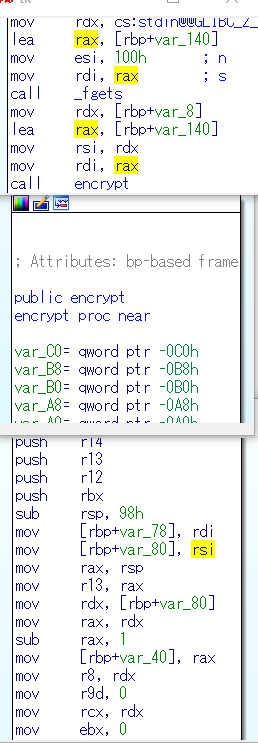
Prior to calling `encrypt`, the parameters are copied to `rsi` and `rdi` and later on copied to the stack in the function entrypoint.
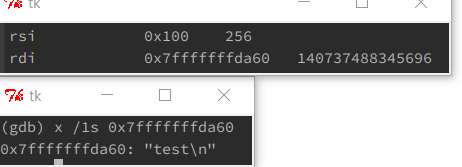
`rdi` points to the given string
`rsi` holds `0x100` which is probably the buffer length

Although there are 3 loops in the function, the encryption itself is done in the first one. To be specific, a key is derived from the loop counter(`i`) and added to each character.

The second and third loops are responsible for reversing the order of the cipher in chunks of 5 and 3 respectively.
The following steps need to be taken for decryption.
1. Reverse order by chunks of 3
2. Reverse order by chunks of 5
3. Derive key from loop counter and subtract from each character
One thing to note is that instead of deriving the key myself, I ripped the key by logging the values stored in `v13`(`xmm0`).