Tags: forensics misc
Rating: 4.7
Original writeup at https://mallux.azurewebsites.net/2021/01/31/pdf-analysis/
# PDF is broken and so is this file
## TL;DR
Analyze broken pdf file and extract several hints that lead to the solution
## Description
*This PDF contains the flag, but you’ll probably need to fix it first to figure out how it’s embedded. Fortunately, the file contains everything you need to render it. Follow the clues to find the flag, and hopefully learn something about the PDF format in the process.*
The challenge provides us with a challenge.pdf file
## The ruby script
When we try to open the pdf, we just get a white page with nothing on it. Let's run strings on it and see if we can find something:
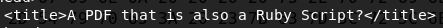
This line reveals that the pdf file can also be interpreted as a ruby script. Here's the entire script:
```
port = 8080
if ARGV.length > 0 then
port = ARGV[0].to_i
html=DATA.read().encode('UTF-8', 'binary', :invalid => :replace, :undef => :replace).split(/<\/html>/)[0]+"</html>\n"
v=TCPServer.new('',port)
print "Server running at http://localhost:#{port}/\nTo listen on a different port, re-run with the desired port as a command-line argument.\n\n"
loop do
s=v.accept
ip = Socket.unpack_sockaddr_in(s.getpeername)[1]
print "Got a connection from #{ip}\n"
request=s.gets
if request != nil then
request = request.split(' ')
end
if request == nil or request.length < 2 or request[0].upcase != "GET" then
s.print "HTTP/1.1 400 Bad Request\r\nContent-Length: 0\r\nContent-Type: text/html\r\nConnection: close\r\n\r\n"
s.close
next
end
req_filename = CGI.unescape(request[1].sub(/^\//,""))
print "#{ip} GET /#{req_filename}\n"
if req_filename == "favicon.ico" then
s.print "HTTP/1.1 404 Not Found\r\nContent-Length: 0\r\nContent-Type: text/html\r\nConnection: close\r\n\r\n"
s.close
next
elsif req_filename.downcase.end_with? ".zip" then
c="application/zip"
d=File.open(__FILE__).read
n=File.size(__FILE__)
else
c="text/html"
d=html
n=html.length
end
begin
s.print "HTTP/1.1 200 OK\r\nContent-Type: #{c}\r\nContent-Length: #{n}\r\nConnection: close\r\n\r\n"+d
s.close
rescue Errno::EPIPE
print "Connection from #{ip} closed; broken pipe\n"
end
__END__
<html>
<head>
<title>A PDF that is also a Ruby Script?</title>
</head>
<body>
<center>
<h1>Download</h1>
</center>
</body>
</html>